Untrusted relay network secure transmission method based on opportunity type wireless energy collection
A secure transmission and relay network technology, applied in the field of secure transmission based on opportunistic wireless energy harvesting untrusted relay networks, can solve the problem of energy harvesting and secure communication of untrusted relay nodes with limited energy, It cannot describe the nonlinear characteristics of the energy harvesting circuit well, and limits the safe transmission performance of the system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
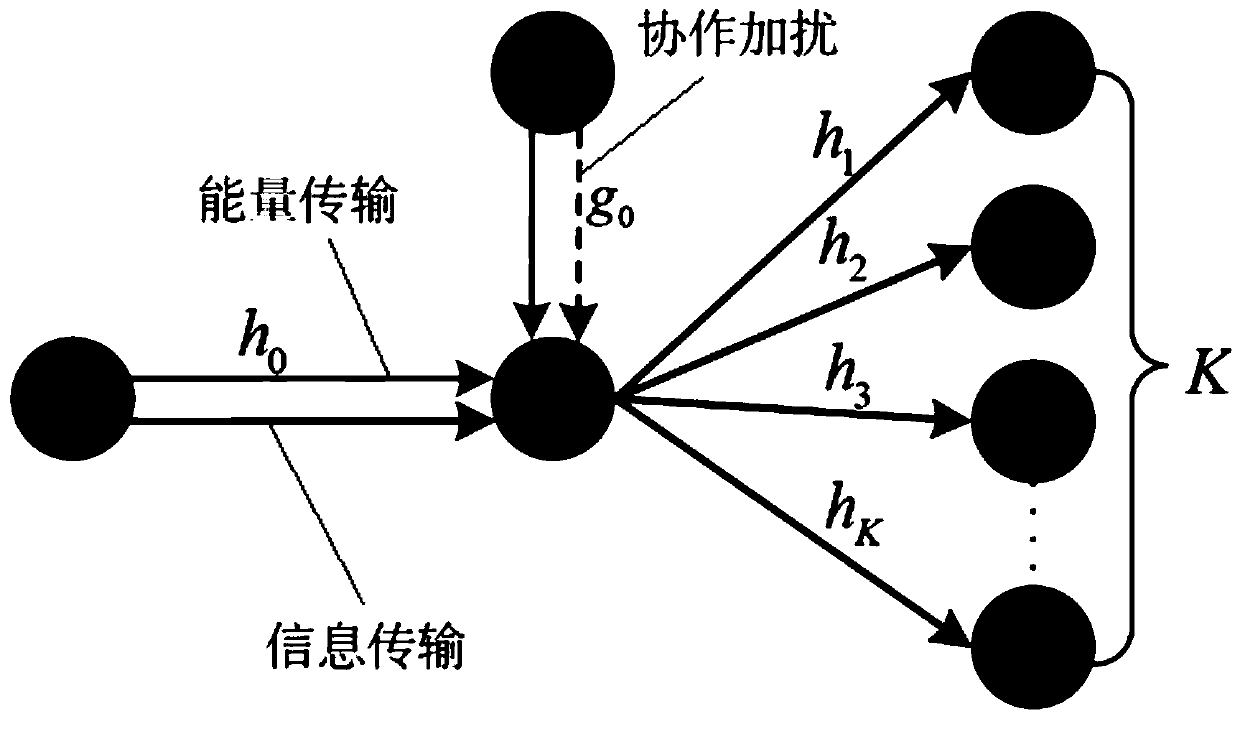
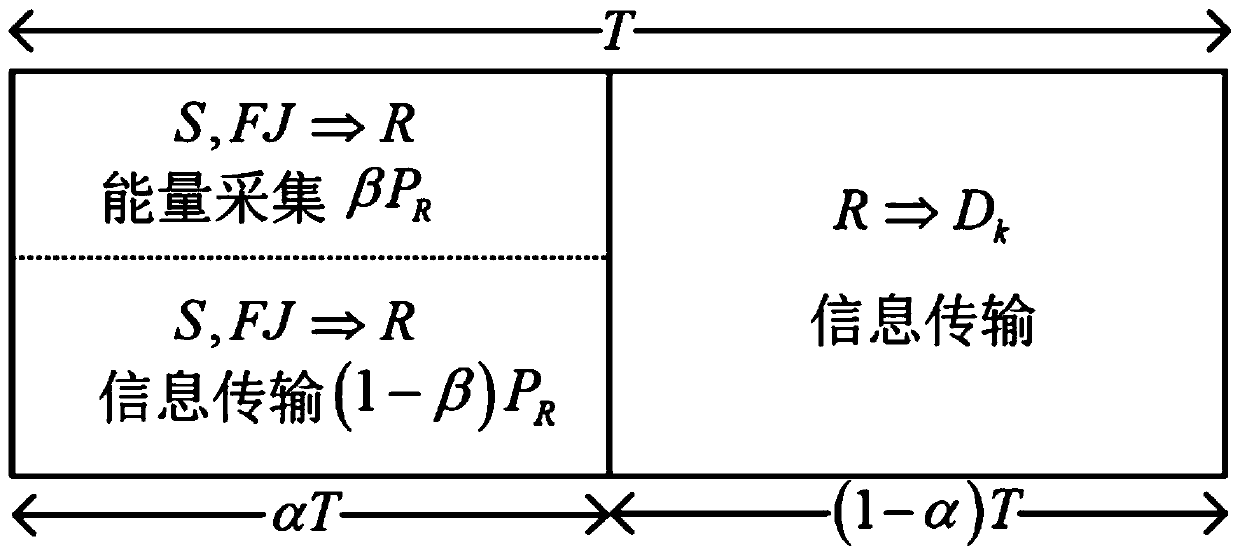
[0067] see figure 1 with figure 2 As shown, the present invention proposes an untrusted relay network secure transmission method based on opportunistic wireless energy harvesting, which is applied to an untrusted relay network secure transmission system. The system includes a source node S, an energy-limited Relay node R, a friendly interference node FJ, and K destination nodes D k , where k∈{1,...,K}; all nodes in the system are equipped with a single antenna, and work in half-duplex mode; the information transmission process from the source node to the destination node is completed within a time slot T .
[0068] Specifically, a secure transmission method based on opportunistic wireless energy harvesting in an untrusted relay network includes:
[0069] Step a, in the first time slot αT, the source uses power P S transmit information to the cooperative relay, while the friendly interfering node with power P J Sending artificial noise reduces the eavesdropping channel ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com