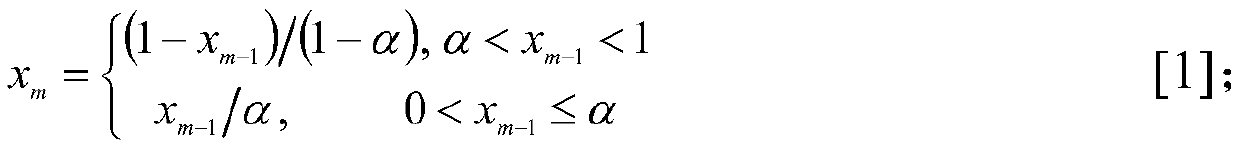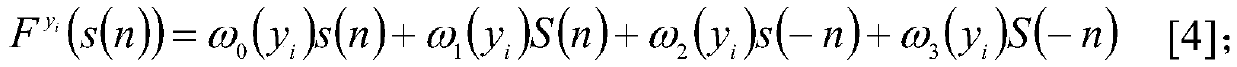WFRFT secure communication method based on chaotic mapping parameter pool
A technology of secure communication and chaotic mapping, which is applied in the field of chaotic technology and secure communication to achieve the effect of increasing concealment and security and increasing the difficulty of scanning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
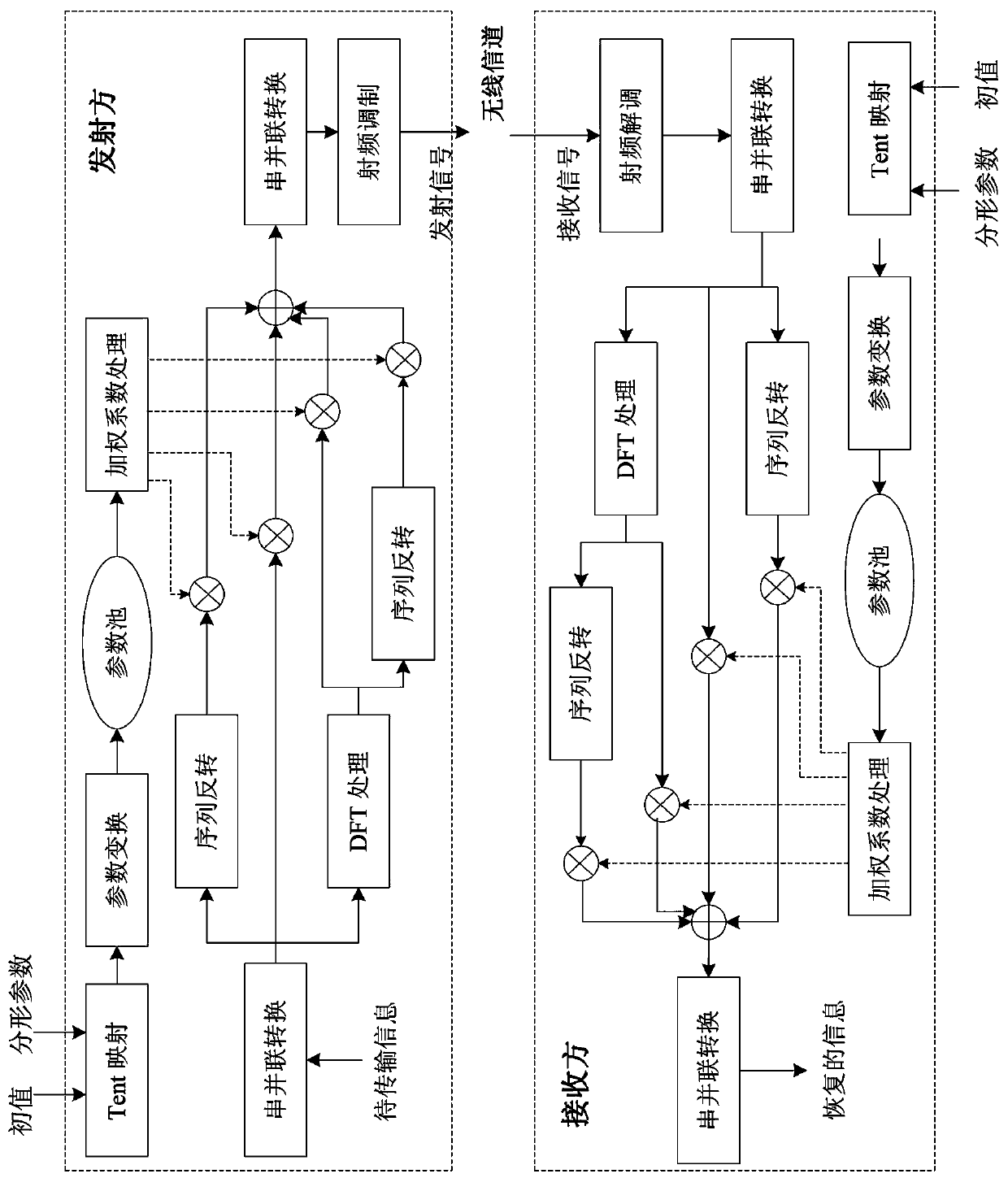
[0011] 1) The Lyapunov exponent value of Tent mapping is relatively high, that is, it has a better initial value sensitive dependence on the initial value, and the full mapping of Tent mapping has a wider range of fractal parameters and a larger application space. Therefore, the Tent mapping based The parameter pool constructor. The Tent sequence is generated by the iterative equation of formula (1), and the initial value range of the Tent map is [0 1), so x m Sequence values also range from [0 1).
[0012]
[0013] 2) Then use the Tent mapping output sequence to perform parameter transformation processing, such as formula (2), so that the transformed parameter y m The value interval is [0 4), and the value interval conforms to the 0-4 cycle characteristics of the modulation order.
[0014] the y m =4x m-1 (2).
[0015] 3) With the growth of the sequence rank m, use the real-valued parameter y m A parameter pool is formed, m∈[1N], the upper limit of m is determined...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com