Method for identifying language used in encrypted VoIP network traffic
A technology for network traffic and identification methods, applied in the field of language analysis and discrimination, can solve the problems of high encryption overhead, large delay, and unacceptability, and achieve the effect of good discrimination accuracy and improved recognition accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
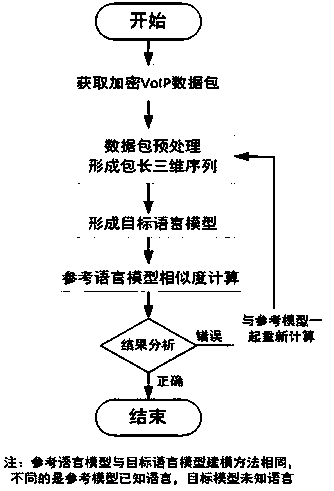
[0042] As a most basic implementation of the present invention, this embodiment discloses a method for identifying the language used in encrypted VoIP network traffic, such as figure 2 , comprising a modeling step, an acquisition processing step and a comparison and identification step;
[0043] Described modeling step is to set up the reference language packet length probability distribution model by using the VoIP packet length sequence feature formed by different languages;
[0044] The collection and processing step is to collect the language data used by the VoIP network traffic to be identified and perform preprocessing, and the preprocessing is to classify the language data according to language types to form a target language packet length probability distribution model;
[0045] The comparison and recognition step is to compare the target language packet length probability distribution model formed in the collection processing step with the reference language packet ...
Embodiment 2
[0048] As a preferred embodiment of the present invention, on the basis of Embodiment 1, a method for identifying the language used in encrypted VoIP network traffic disclosed in this embodiment further:
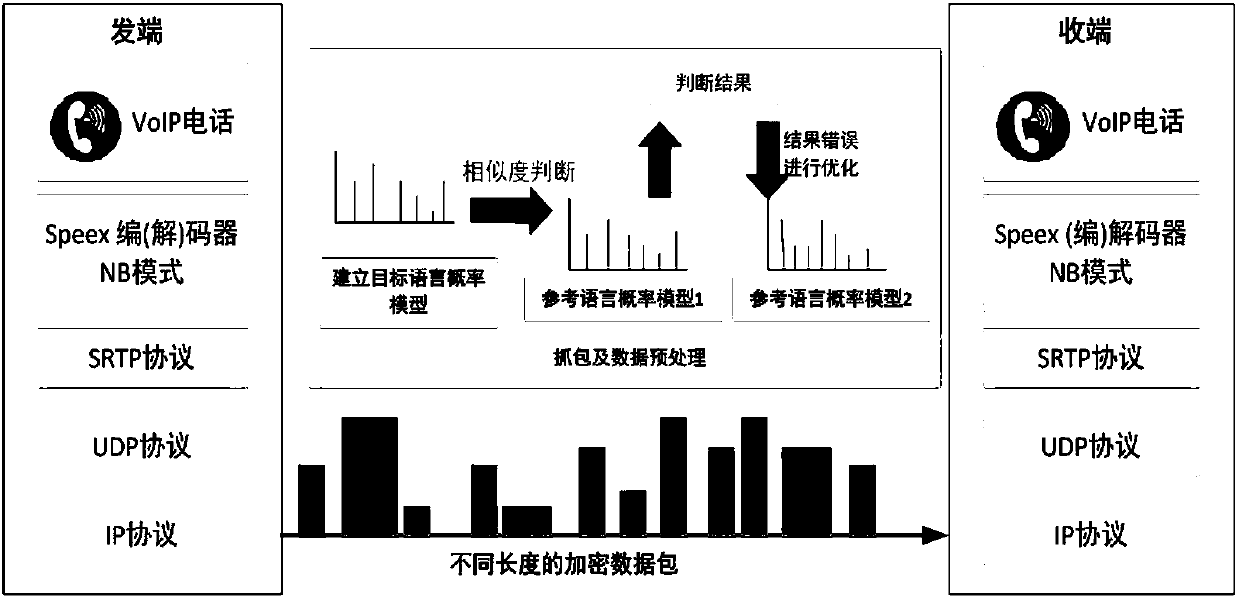
[0049] Such as figure 1 , the reference modeling step is to use the known reference speech language VoIP network traffic data with the Speex codec narrowband mode, according to the method of preprocessing in the collection processing step, form the three-dimensional time of the packet length after the data packet preprocessing Sequence (S i , S j , S k ), as a sample point of the reference language packet length probability model, the VoIP protocol runs on top of the TCP / UDP protocol, and most of them use the UDP protocol. The packet length here refers to the UDP layer data packet length in bytes minus the fixed The number of bytes in the length of the UDP header, the length of the UDP layer data packet can be obtained by directly reading the length field in the UDP heade...
Embodiment 3
[0062] As a preferred embodiment of the present invention, this embodiment discloses a method for identifying the language used in encrypted VoIP network traffic, including the following steps:
[0063] Step S1, network data collection and preprocessing; obtain data traffic packets from the network, remove irrelevant traffic, retain VoIP encrypted network traffic, and save files for data packet length feature extraction; preprocess data packets, and confirm VoIP The data packet uses the SRTP protocol on the UDP layer. Whether the SRTP protocol uses padding (the padding byte length needs to be deducted after padding is used), and the payload length can be obtained by using the built-in function of the packet capture software (free software Wireshark is recommended). Export the packet length field from the packet capture software and save it as a csv file for the next step of modeling
[0064] Step S2, forming the packet length probability model of the reference language; using ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com