Face recognition and detection-based visitor guiding system and method
A face recognition and guidance system technology, which is applied in the field of visitor guidance system based on face recognition detection, can solve the problems that a single visitor cannot pass, and the passage area cannot be finely controlled, so as to improve office efficiency and strengthen visitor freedom , Improving the effect of access control security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] This system is based on the visitor system through the interface technology to enable users to invite and make reservations for visitors, and the visitors actually obtain the authority to open the office area before they arrive. It ensures that the enterprise can effectively control the access control security and at the same time complete the self-service use of enterprise visitors when there is a network. It adds an intelligent operation mode to the modern office system and reduces unnecessary manual processing.
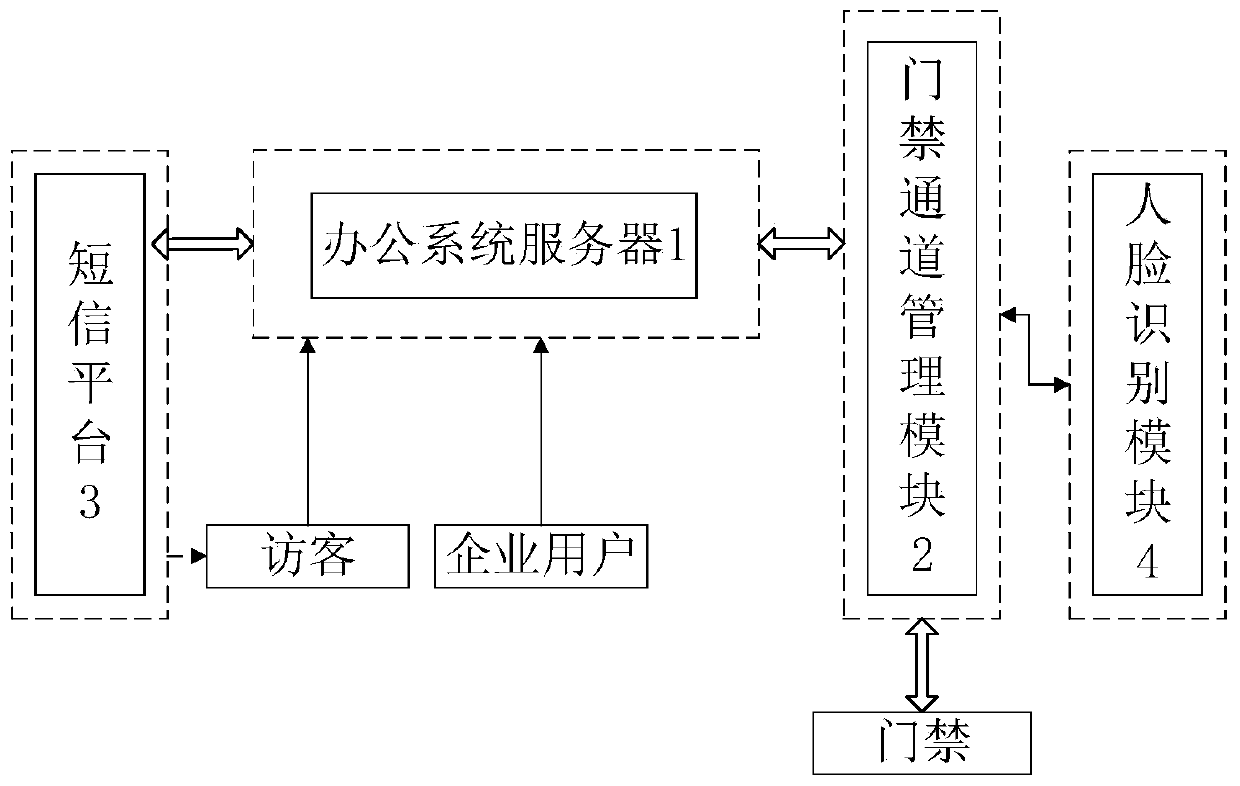
[0041] Such as figure 1 As shown, the visitor guidance system based on face recognition detection includes:
[0042] Office system server 1 with a user interface;
[0043] The access control channel management module 2 is connected with the access control and office system server 1, and is used to receive the authorized door opening signal;
[0044] The short message platform 3 is connected with the office system server 1, and provides fee-based cloud com...
Embodiment 2
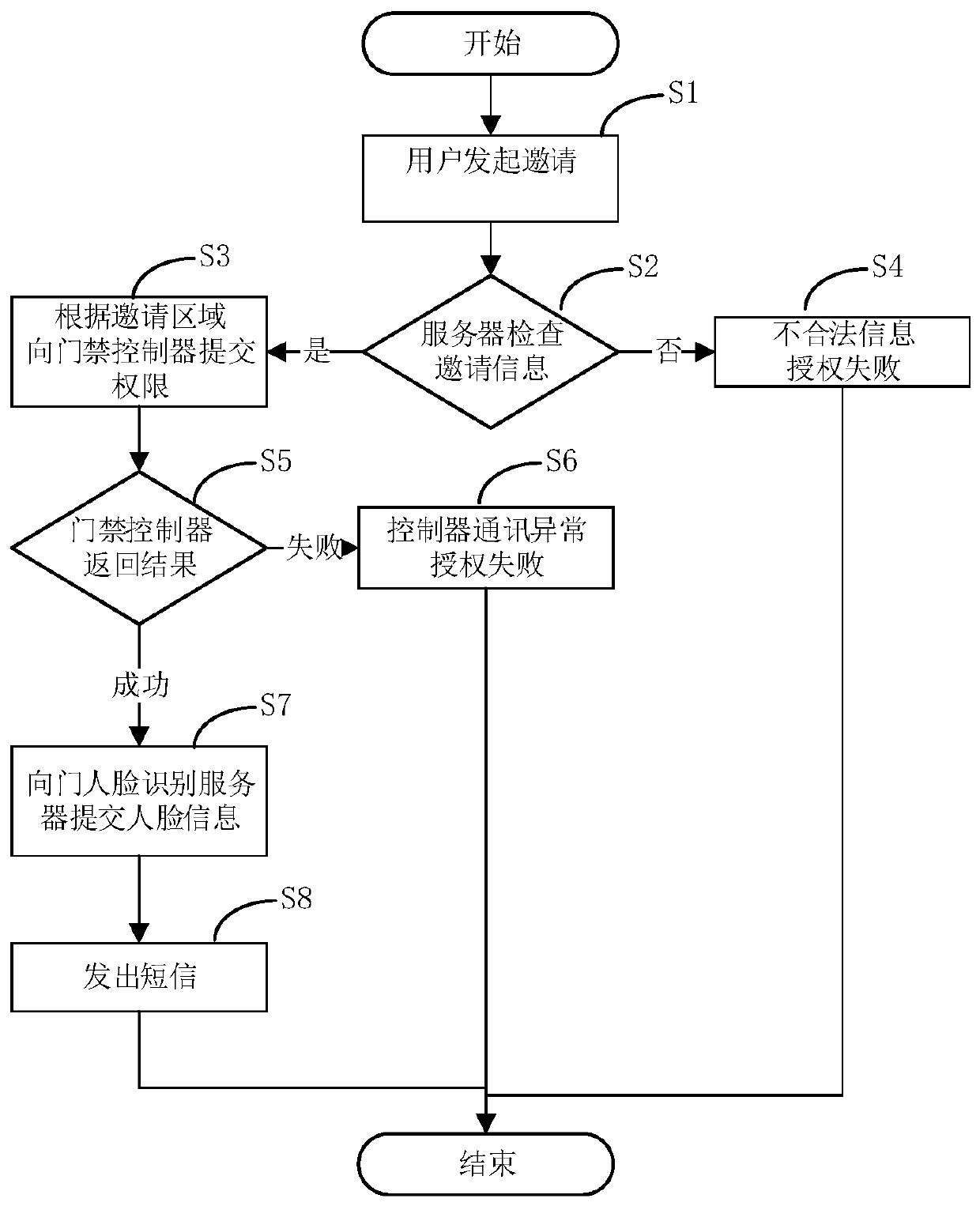
[0050] Such as figure 2 As shown, the method for entering visitor information using the system described in Embodiment 1 includes the following steps:
[0051] S1, the user sends an invitation to the office system server 1 through the user interface;
[0052] S2, the office system server 1 checks whether the invitation information is legal, if so, proceeds to step S3, otherwise proceeds to step S4;
[0053] S3, the office system server 1 submits the authority according to the access control channel management module 2 in the relevant area of the invitation, and enters step S5;
[0054] S4, the entry of visitor authority fails, and the process ends;
[0055] S5, the access control channel management module 2 returns the visitor authority input result, if successful, then enters step S7, otherwise enters step S6;
[0056] S6, the communication is abnormal, the entry of visitor authority fails, and the process ends;
[0057] S7, the visitor authority entry is successful, t...
Embodiment 3
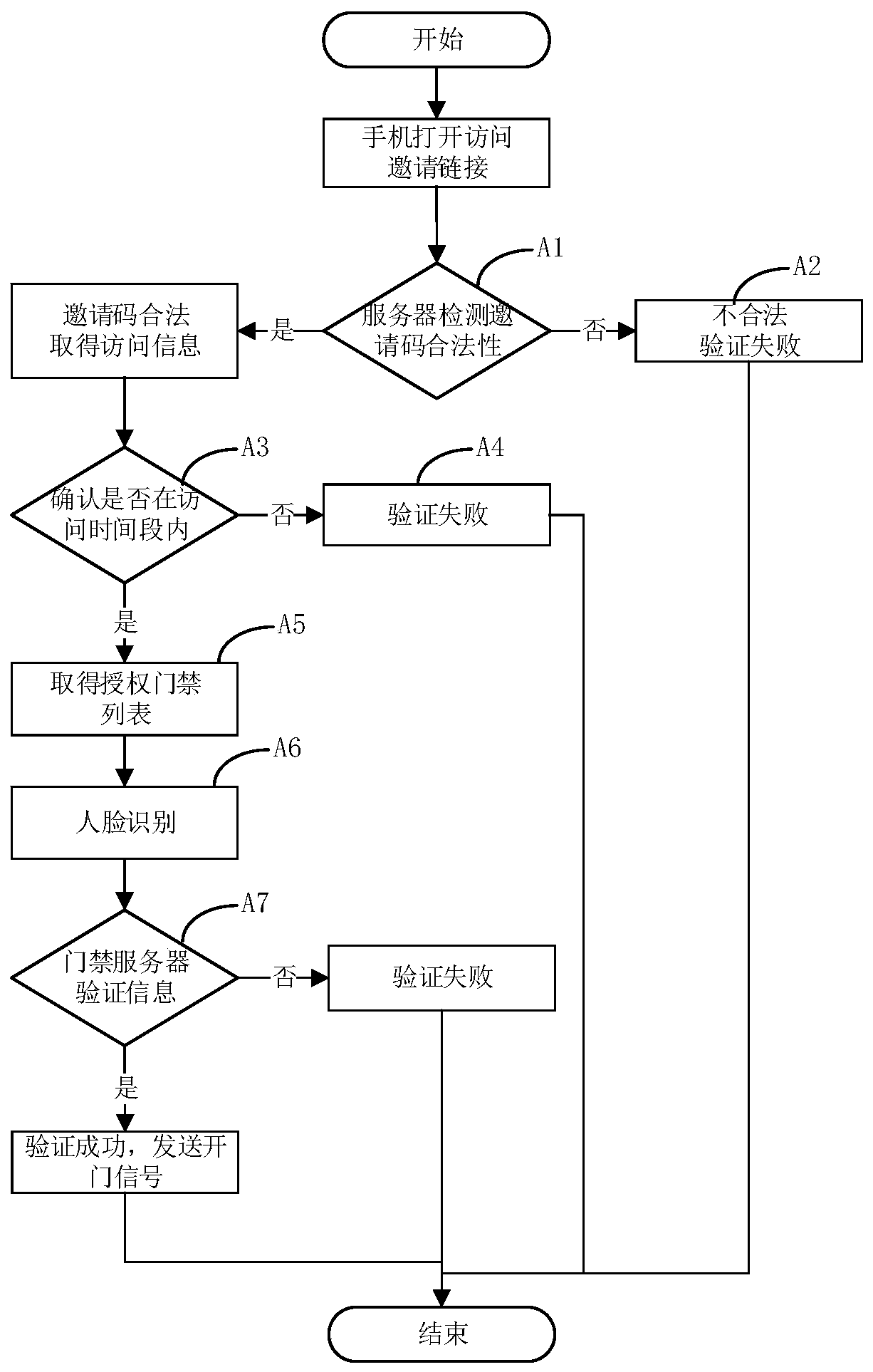
[0060] Such as image 3 As shown, the method for visitor verification using the system described in Embodiment 1 includes the following steps:
[0061] A1, after the invitation in the invitation text message is clicked, the office system server 1 checks whether the link is legal, if so, proceed to step A3, otherwise proceed to step A2;
[0062] A2, the verification fails, and the process ends;
[0063] A3, the office system server 1 detects whether the current time is within the visiting period corresponding to the visitor, if so, proceed to step A5, otherwise proceed to step A4;
[0064] A4, the verification fails, and the process ends;
[0065] A5, the office system server 1 sends an authorized door opening signal to the access control passage management module 2, and the authorized door opening signal contains the visitor's face information;
[0066] A6, the face recognition module 4 receives the face image and sends it to the access control channel management module 2; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com