An information protection method, device, mobile terminal and storage medium
A mobile terminal, information protection technology, applied in the direction of digital data protection, can solve problems such as abuse of authority and inability to guarantee information security, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] refer to figure 1 , which shows a flow chart of the steps of an information protection method provided in Embodiment 1 of the present invention, which may specifically include the following steps:
[0025] Step 101, acquire target information.
[0026] In the embodiment of the present invention, if the application requests information such as address book, calendar, geographic location, images captured by the camera, and audio collected by the microphone on the mobile terminal, authorization from the user is required. When an application requests target information, it first obtains the target information and conducts real-time analysis to determine whether the target information needs to be protected.
[0027] For example, by adding a data privacy sandbox to monitor the use of key devices such as cameras, microphones, and GPS chips at the bottom of the system, when the application requests the target information obtained by these key devices, first determine whether t...
Embodiment 2
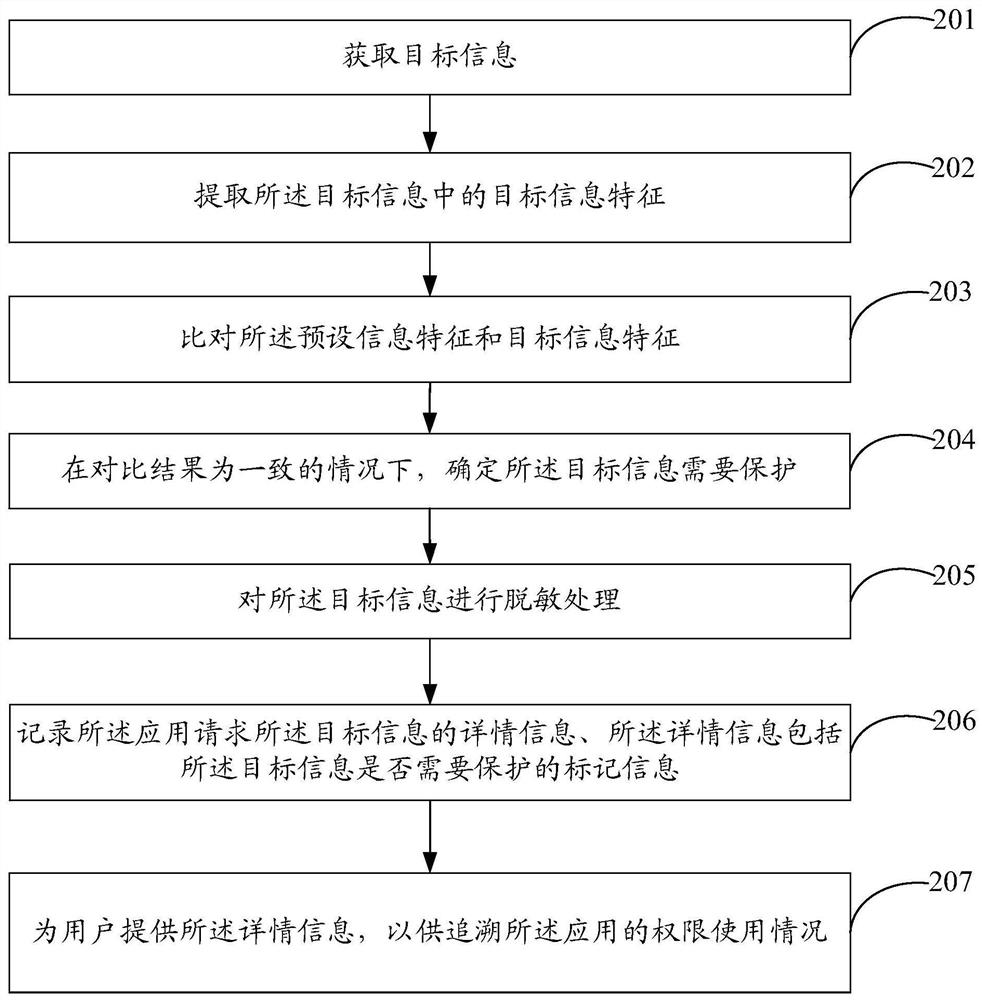
[0037] refer to figure 2 , which shows a flow chart of the steps of an information protection method provided in Embodiment 2 of the present invention, which may specifically include the following steps:
[0038] Step 201, acquire target information.
[0039] In the embodiment of the present invention, for the specific implementation manner of this step, reference may be made to the description in the foregoing embodiments, and details are not described here.
[0040] Step 202, extracting target information features in the target information.
[0041] In the embodiment of the present invention, the preset information protection rules include preset information features, which provide identification standards for subsequent data analysis. The preset information features can be set in advance by the user, or can be downloaded from the network, or The preset information feature can be obtained in any other applicable manner, which is not limited in this embodiment of the prese...
Embodiment 3
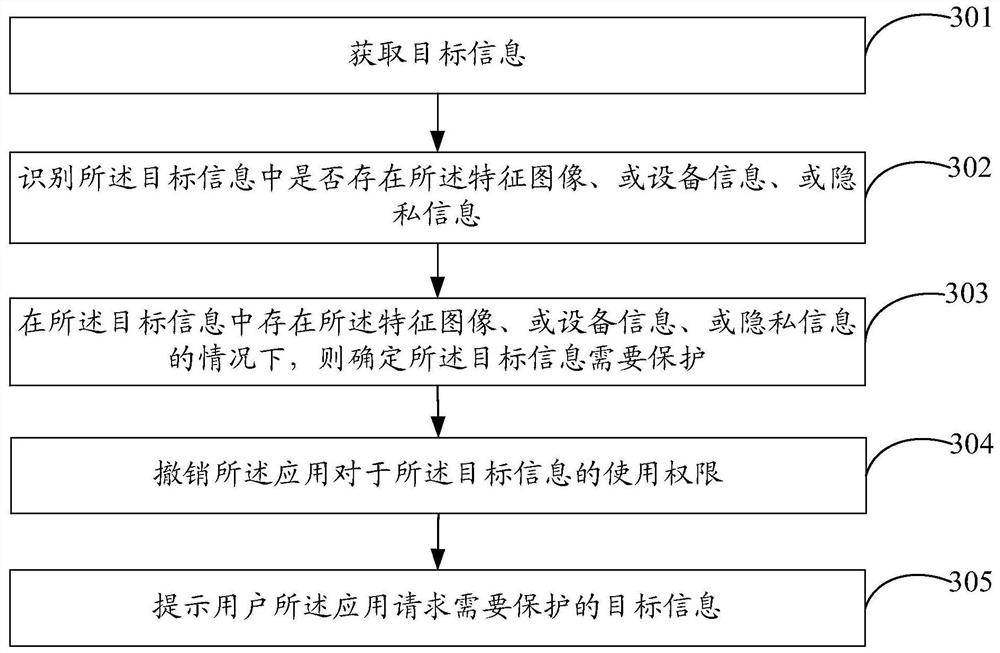
[0064] refer to image 3 , which shows a flow chart of the steps of an information protection method provided in Embodiment 3 of the present invention, which may specifically include the following steps:
[0065] Step 301, acquire target information.
[0066] In the embodiment of the present invention, for the specific implementation manner of this step, reference may be made to the description in the foregoing embodiments, and details are not described here.
[0067] Step 302, identifying whether the feature image, or device information, or private information exists in the target information.
[0068] In the embodiment of the present invention, the preset information protection rules include at least one of characteristic images, device information, and privacy information. In the settings of the operating system, switches for the above various preset information protection rules can be added, and the user can choose Whether to open.
[0069] Among them, characteristic im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com