Electronic voting method and system
An electronic and signature information technology, applied in the field of voting, can solve problems such as fraud, hindering the widespread application of electronic voting systems, and cheating votes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
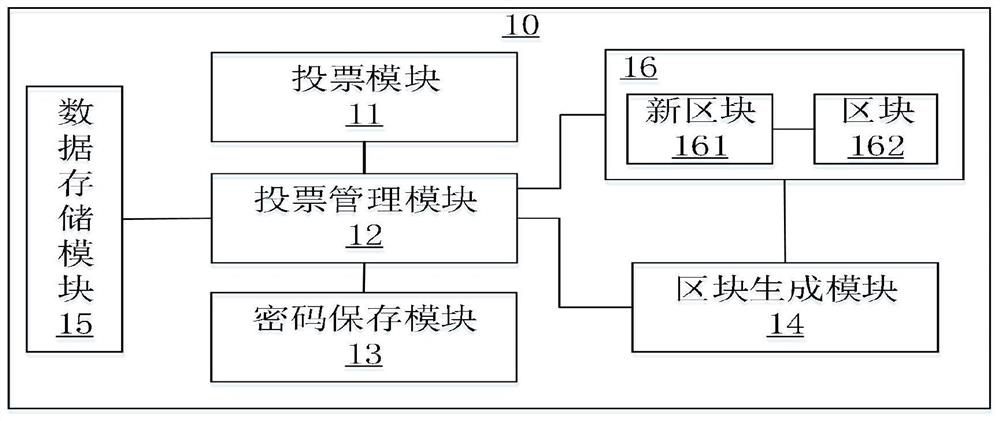
[0028] see figure 1 , the first embodiment of the present invention proposes an electronic voting system. Such as figure 1 As shown, the electronic voting system 10 includes, for example: a voting module 11 , a voting management module 12 , a password saving module 13 and a block generating module 14 . Wherein, the voting management module 12 is respectively connected to the voting module 11 , the password saving module 12 and the block generating module 14 .
[0029] Specifically, the voting module 11 is used for:
[0030] Obtain the identification code and voting list sent by the voting management module 12;
[0031] Generate a decryption private key, and calculate a corresponding encryption public key according to the decryption private key;
[0032] Keep the decryption private key, and send the encrypted public key to the voting management module 12, and the encrypted public key is stored in the password storage module 13 by the voting management module 12;
[0033] V...
no. 2 example
[0088] see Figure 5 , is a schematic flowchart of the electronic voting method provided in the second embodiment of the present invention. Such as Figure 5 As shown, the electronic voting method includes steps S31 to S34, for example.
[0089] Step S31: initiate a voting step;
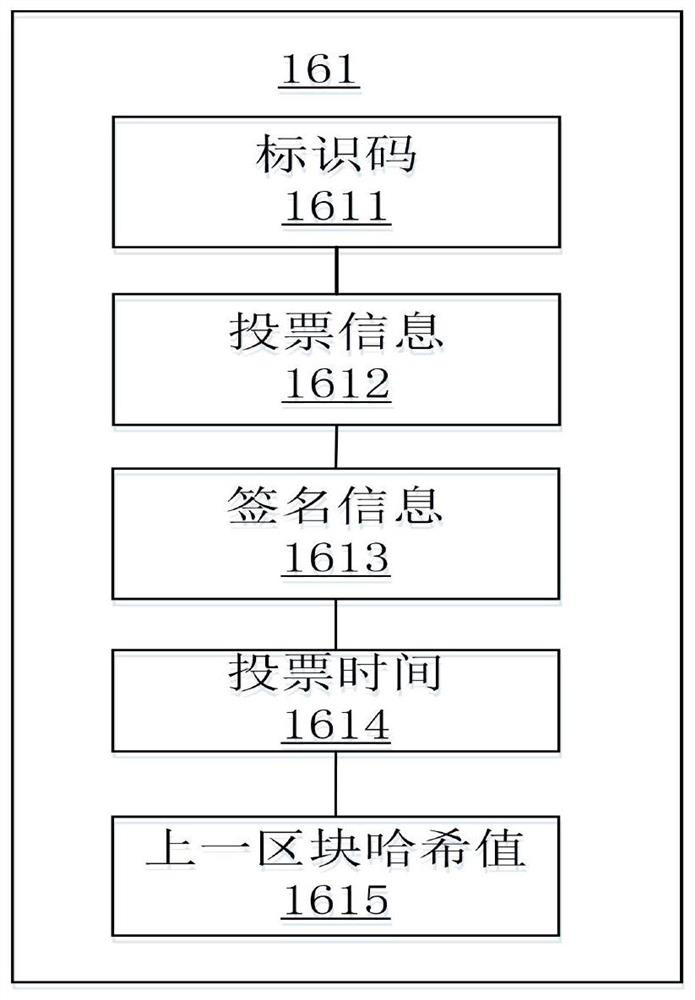
[0090] Among them, such as Image 6 As shown, step S31 includes, for example, steps S311 to S314.
[0091] Step S311: the voting module acquires the identification code and voting list sent by the voting management module;
[0092] Step S312: the voting module generates a decryption private key, and calculates a corresponding encryption public key according to the decryption private key;
[0093] Step S313: the voting module retains the decryption private key, and sends the encrypted public key to the voting management module, and the voting management module stores the encrypted public key in the password storage module;
[0094] Step S314: the voting module performs voting according to the vo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com