An Algorithm to Avoid Costless Attacks in Blockchain Consensus
A blockchain and algorithm technology, applied in the blockchain field, can solve problems such as malicious node attacks, long-range attacks, and data inconsistencies, and achieve the effect of strengthening certainty and improving processing performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
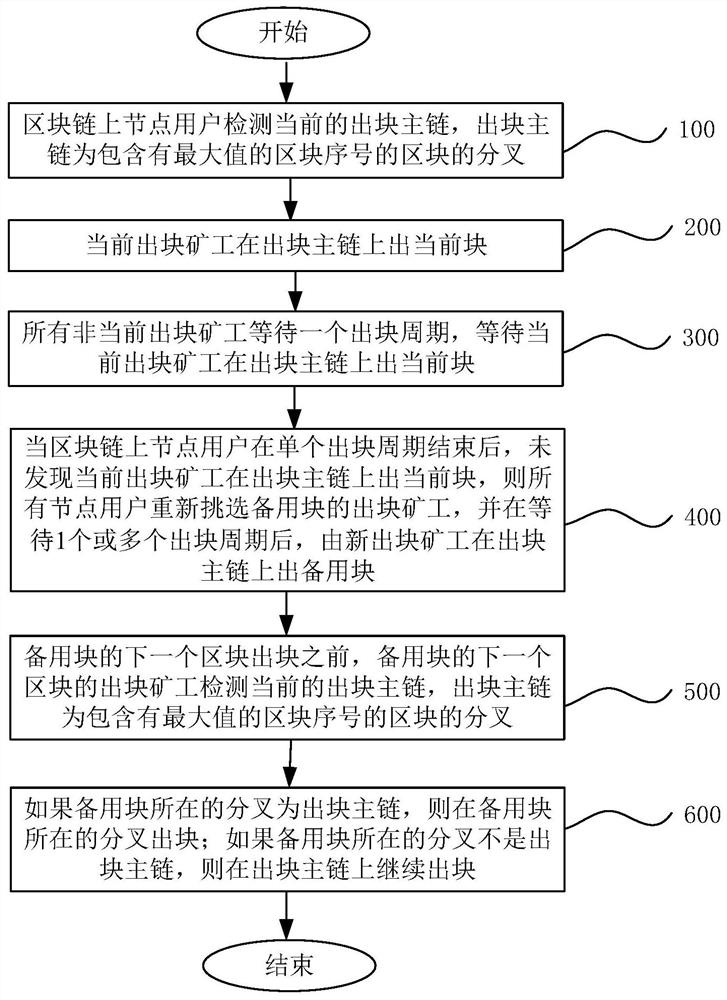
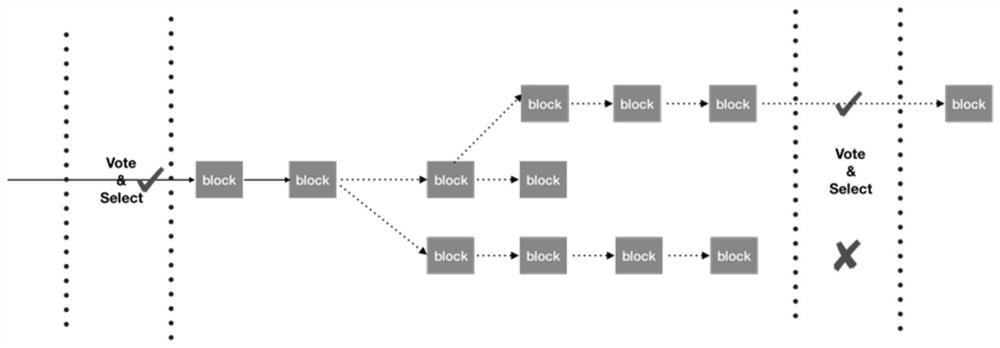
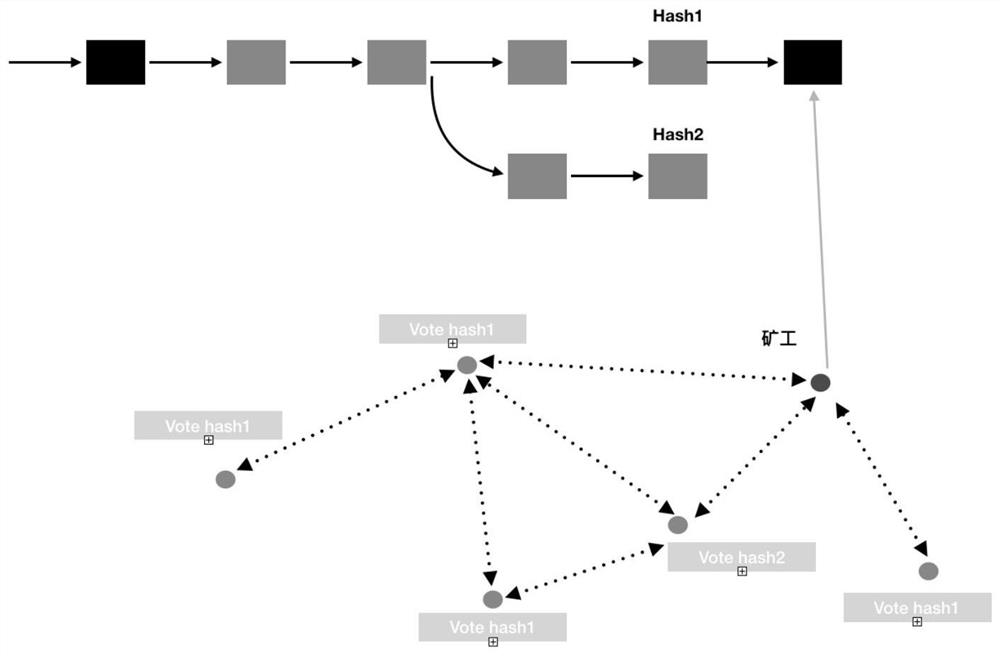
[0023] In order to make the purpose, technical solution and advantages of the present invention clearer, the technical solution of the present invention will be clearly and completely described below in conjunction with specific embodiments of the present invention and corresponding drawings.
[0024] In the description of the present invention, the certification center (CA—Certificate Authority), as an authoritative, reliable, and impartial third-party organization, is specially responsible for issuing and managing the digital certificates required by all entities participating in transactions on the chain. As an authority, it manages keys effectively, issues certificates to prove the validity of keys, and links public keys with certain entities (consumers, merchants, banks). It is responsible for generating, distributing and managing the digital certificates required by all parties involved in the exchange of information on the Internet, and is therefore at the heart of secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com