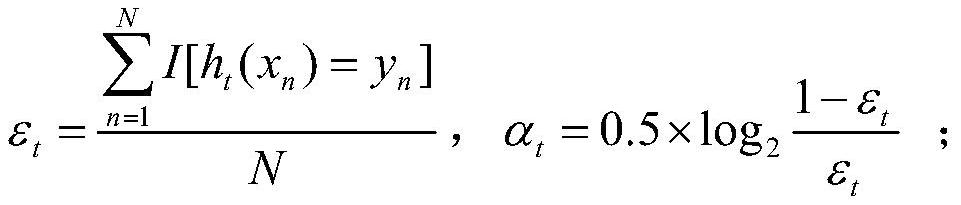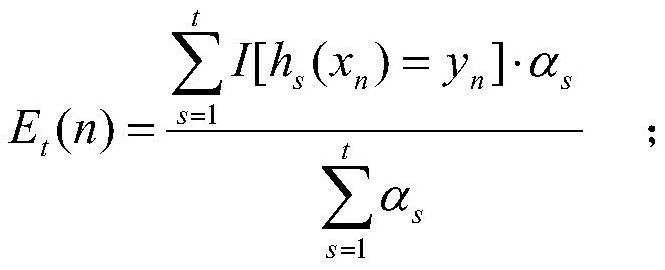Network Intrusion Detection Method Based on Data Mining
A technology of network intrusion detection and data mining, which is applied in digital data information retrieval, electronic digital data processing, special data processing applications, etc., can solve the problems of reduced classification accuracy, high computing overhead, and slow classification speed, and achieve reduced computing Overhead, the effect of increasing classification speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described below in conjunction with the accompanying drawings.
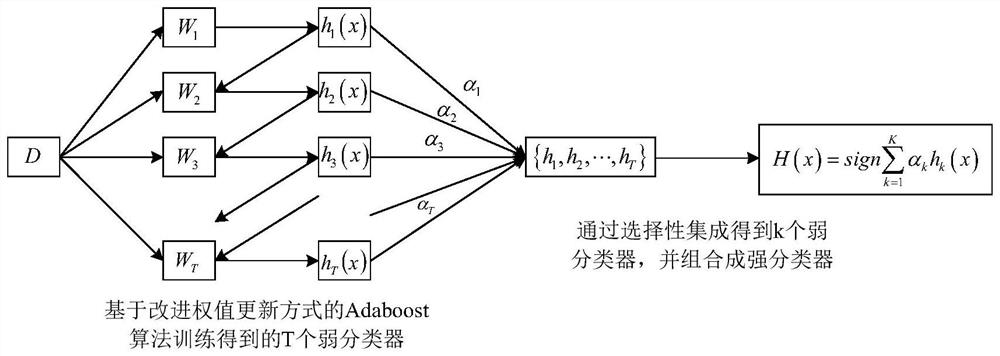
[0049] like figure 1 , a network intrusion detection method based on data mining, the specific steps are as follows:
[0050] Step (1) Use the Adaboost algorithm with the improved weight update method to train the weak classifier:
[0051] Step (1.1) Let the initial training set be D={(x 1 ,y 1 ),(x 2 ,y 2 ),...,(x N ,y N )}, N is the total number of samples in the training set; initialized weights of training samples: the initial weight of each training sample is 1 / N, and the initial weight vector is {1 / N,1 / N,…,1 / N }.
[0052] Step (1.2) train T weak classifiers. The training method of the t-th weak classifier is as follows, 1≤t≤T:
[0053] Step (1.2.1) randomly select N training samples from the initial training set D according to the sample weights, as the t-th weak classifier h t The training set D t ;
[0054] Step (1.2.2) According to the training set...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com