Method for detecting voice fraud replay attack by voice amplitude information and multiple phases
A technology of phase detection and replay attack, which is applied in speech analysis, instruments, etc., can solve problems such as ignoring phase information, and achieve the effects of easy implementation, improved results, and improved experimental results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further described in detail below in conjunction with specific embodiments, so as to better reflect the advantages of the present invention.
[0054] A method of using voice amplitude information and multiple phase detection voice fraud replay attacks, mainly comprising the following steps:
[0055] S1: Amplitude feature and phase feature extraction:
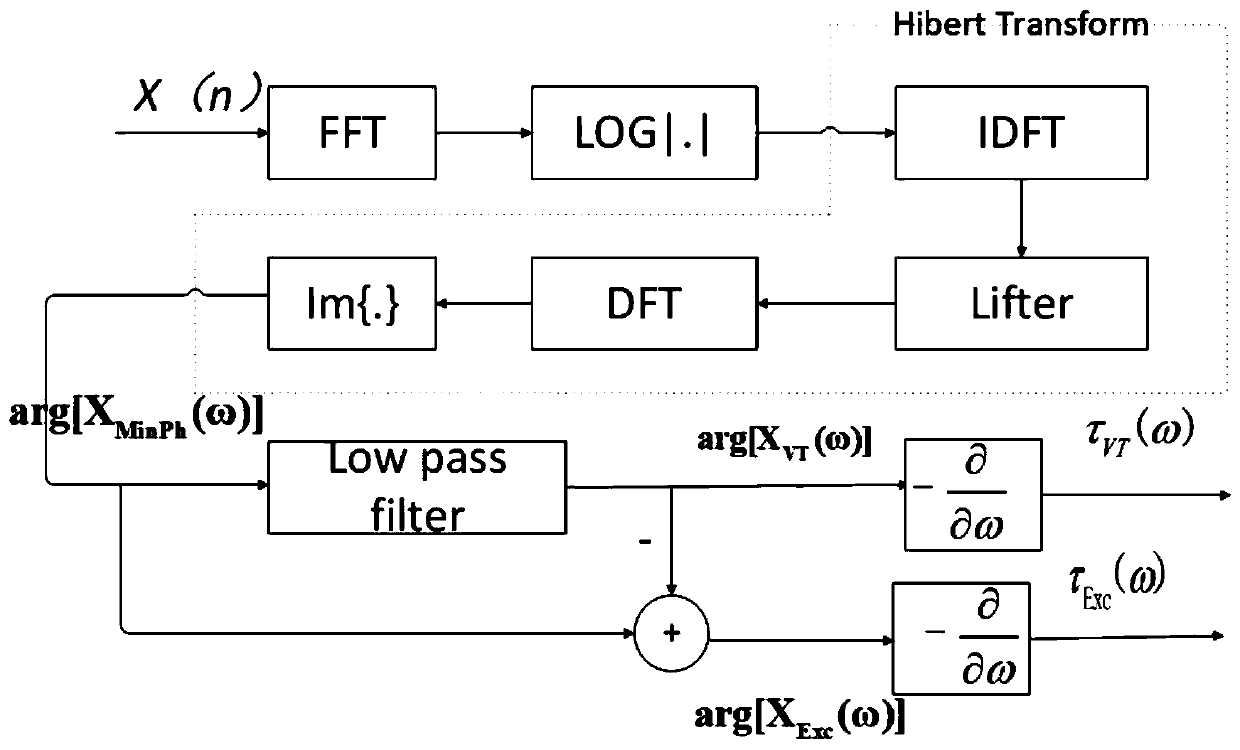
[0056] The amplitude feature is a CQCC feature, and the phase feature is a Mel-RP feature and an MPVT feature; wherein, the extraction of the amplitude feature is to convert the geometric space of the frequency bin into a linear space by using constant Q transform; the extraction of the phase feature mainly The phase spectrum is obtained through pre-emphasis, framing, windowing, and short-time Fourier transform, and then processed on this basis;
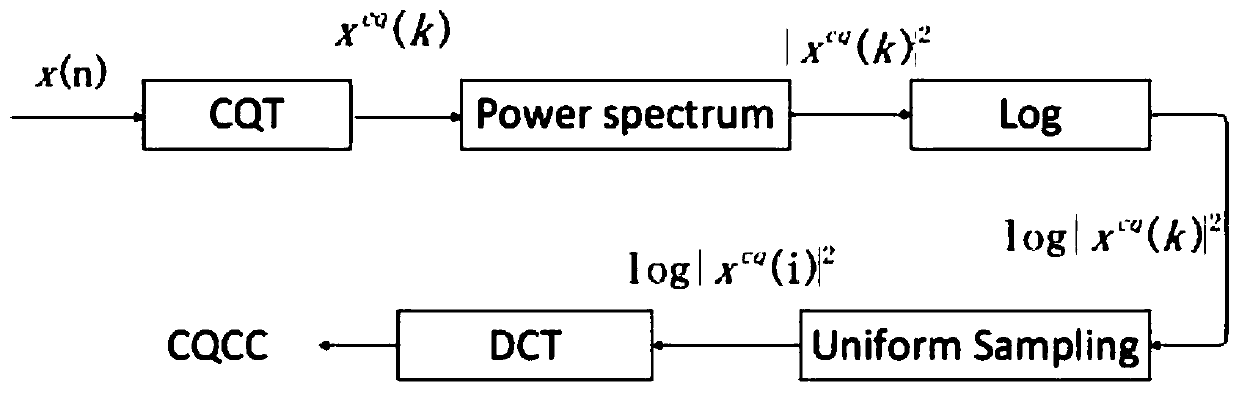
[0057] 1) CQCC feature extraction
[0058] The CQCC feature is a kind of amplitude feature. By using the constant Q transformation, the geometric...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com