Permission control method and device, storage medium, and computer equipment
A technology of permission control and permission set, applied in transmission systems, electrical components, program/content distribution protection, etc., can solve problems such as the reduction of program process security, and achieve the effect of improving security defense and avoiding viruses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Hereinafter, the present application will be described in detail with reference to the drawings and embodiments. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
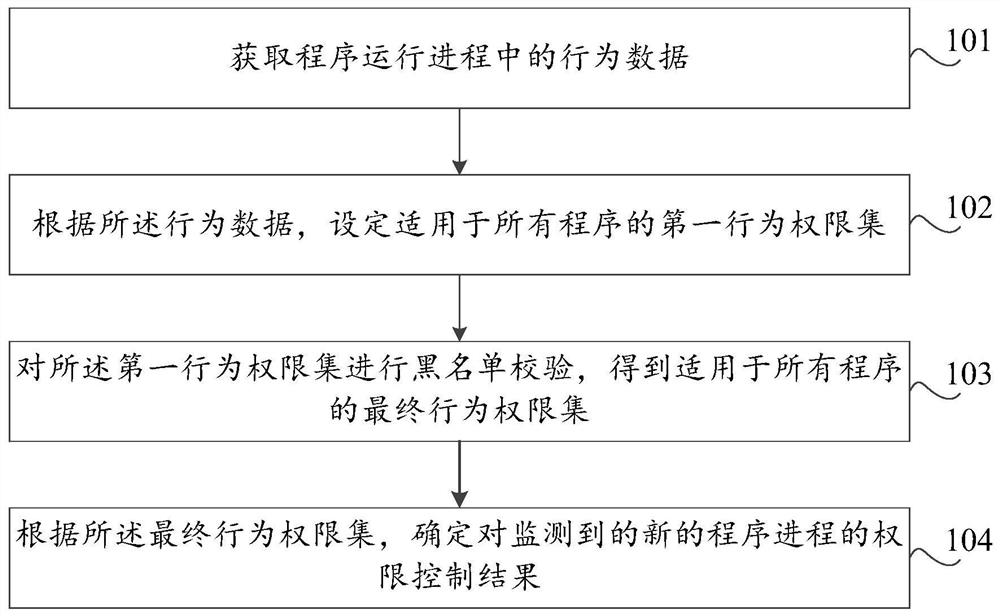
[0025] In this embodiment, a permission control method is provided, such as figure 1 As shown, the method includes:
[0026] Step 101, acquiring behavior data during program running.
[0027] During the running of the program, the running process of the program will be displayed in the task manager, and a large amount of behavior data in the running process can be obtained according to the running process of different programs. The running process of the program includes the system process for the system program and the application process for the application program. A system program may include multiple programs, each of which corresponds to a system process, and an application program may a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com