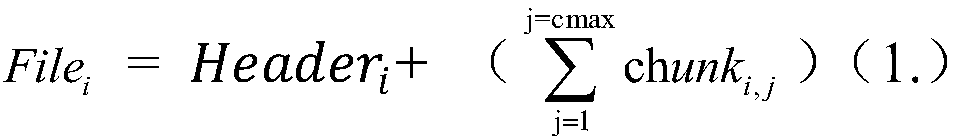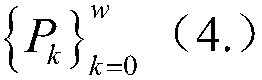Pseudo random permutation based data encryption method in OPC UA edge computation
A technology of edge computing and encryption method, applied in digital transmission systems, secure communication devices, secure communication through chaotic signals, etc. It can solve problems such as small memory capacity, slow CPU speed, and limited power.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0024] The technical scheme that the present invention solves the problems of the technologies described above is:
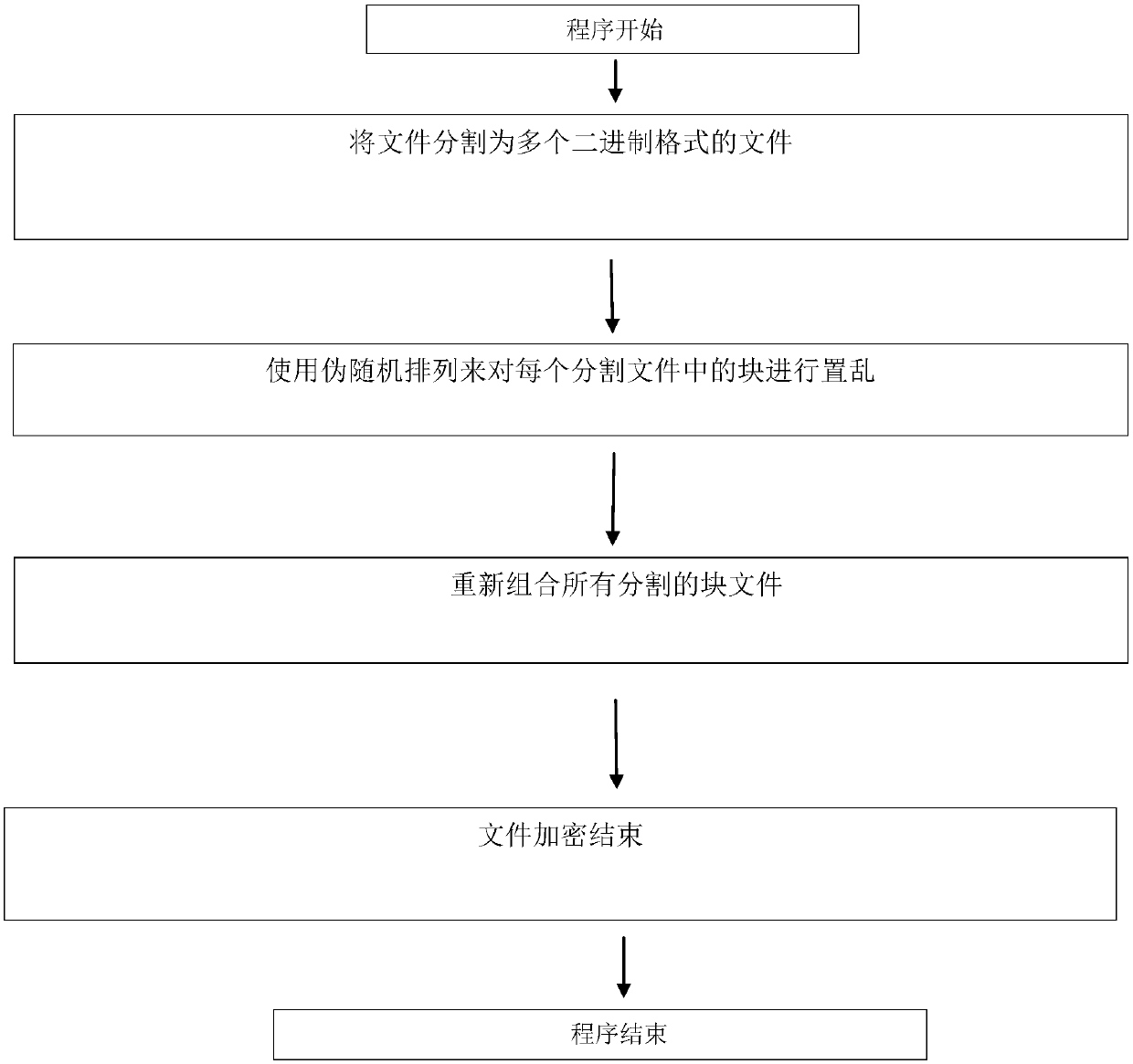
[0025] The present invention proposes a chaotic system-based pseudo-random permutation (PRPM) to realize lightweight encryption of data in edge computing of OPC UA, and mobile users need an encryption method to protect their data privacy. One of the encryption methods that can be considered a security method is the Advanced Encryption Standard (AES). However, mobile devices have limited resources, such as limited power, slow CPU speed, small memory capacity, etc., and it is impossible to use the AES encryption method for each file when each file needs to be uninstalled / downloaded. (Traditi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com