RSA public key decomposition and decryption method and system
A public key, decomposed technology, applied in the field of information security, can solve the problems of high qubit number and high quantum control precision, and achieve the effects of high precision, good stability and easy implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
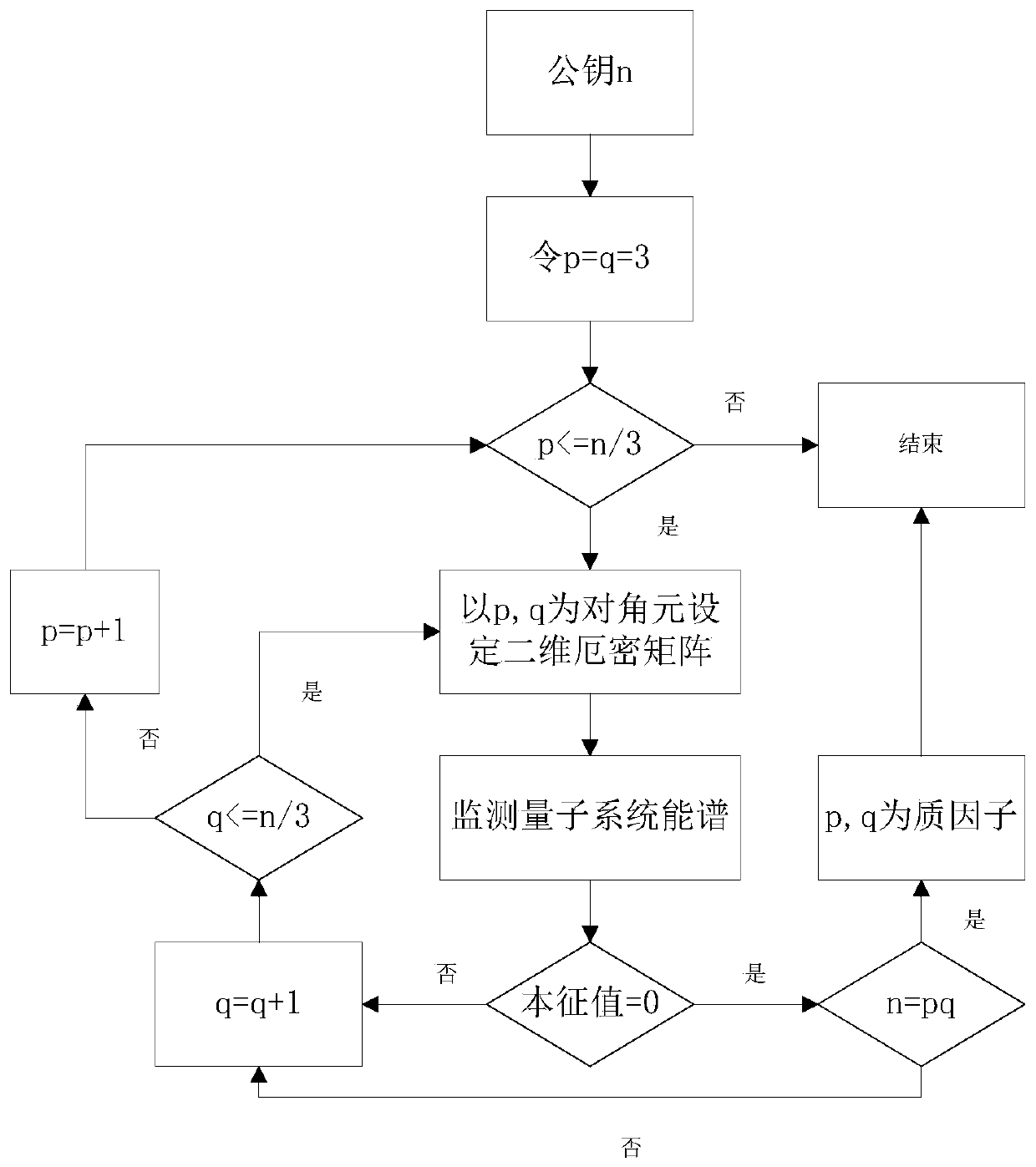
[0060] This embodiment provides a method for decomposing an RSA public key, such as figure 1 shown, including the following steps:
[0061] (1) Get the RSA public key n;
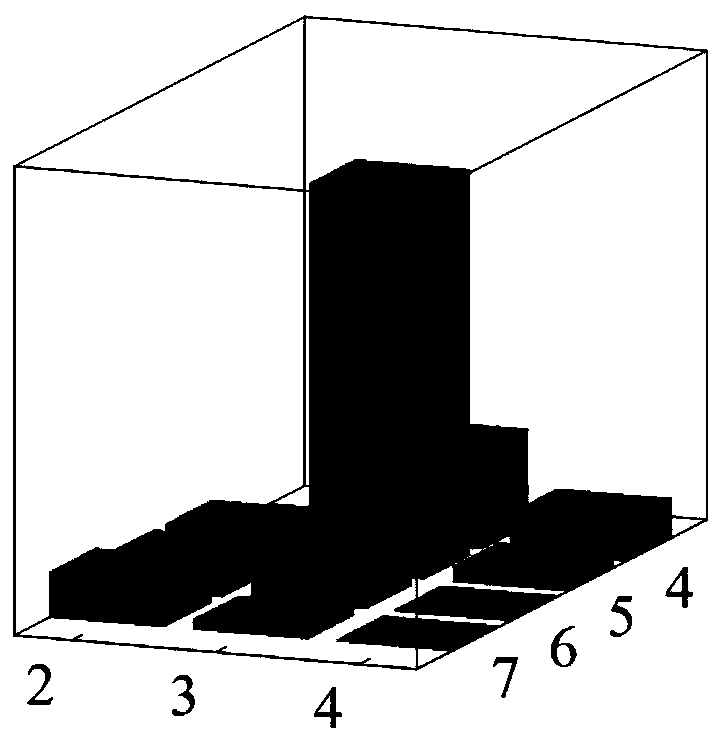
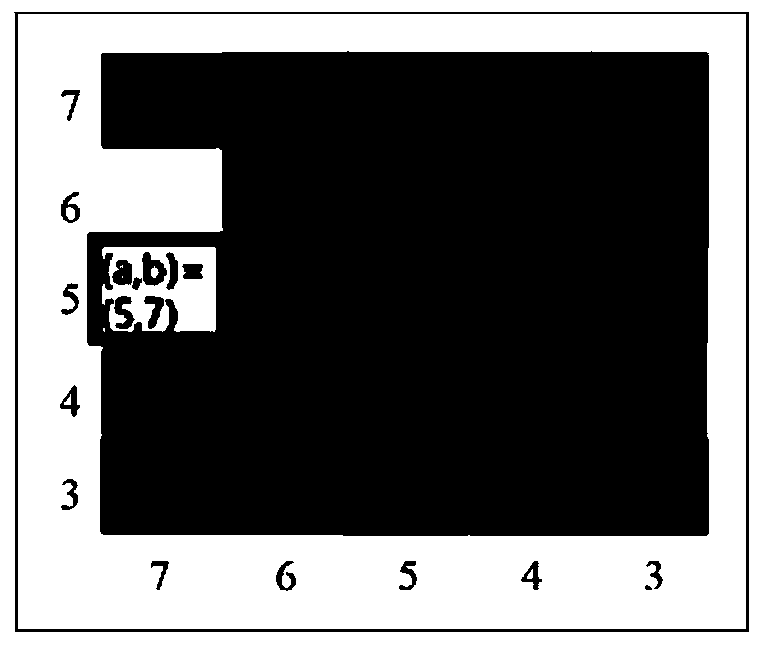
[0062] (2) Obtain a prime factor pair less than or equal to n / 3, and form a corresponding two-dimensional Hermitian matrix according to the prime factor pair and the public key n, and control the external quantum system Electromagnetic field, make the Hamiltonian of the quantum system be the two-dimensional Hermitian matrix, and measure the energy spectrum of the quantum system to see whether the eigenvalue of the two-dimensional Hermitian matrix is at x=0 (experimentally, there is a The maximum value of the resonance peak appears), if not, judge other prime factor pairs , if yes, then judge that the prime factor pair is obtained by decomposing the RSA public key n The two prime factors of are output. This step specifically includes:
[0063] (2.1) Set the initial value of the prime factor pair to ...
Embodiment 2
[0084] This embodiment discloses a kind of RSA public key decomposition system, comprising:
[0085] The public key acquisition module is used to obtain the RSA public key n;
[0086] The public key decomposition module is used to obtain a prime factor pair less than or equal to n / 3, and form a corresponding two-dimensional Hermitian matrix according to the prime factor pair and the public key n, while controlling The external electromagnetic field of the quantum system makes the Hamiltonian of the quantum system be the two-dimensional Hermitian matrix, and measure the energy spectrum of the quantum system to see whether the eigenvalue of the two-dimensional Hermitian matrix is at x=0, if not, then the Other prime factor pairs are judged, and if they are, then the prime factor pair is judged to be two prime factors obtained by decomposing the RSA public key n, and output.
[0087] Wherein, the public key decomposition module specifically includes:
[0088] The initial va...
Embodiment 3
[0098] This embodiment provides a kind of RSA decryption method, comprising:
[0099] (1) adopt the RSA public key decomposition method of embodiment 1 to decompose the RSA public key n, obtain two prime factors p, q;
[0100] (2) Calculate the private key d according to the prime factors p and q in the following way:
[0101] d=e -1 (mod(p-1)(q-1))
[0102] In the formula, e is an odd number that is relatively prime to (p-1)(q-1);
[0103] (3) Obtain the ciphertext data C to be decrypted, and use the following formula to decrypt the ciphertext data C into plaintext data M:
[0104] M=C d modn.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com