Network anomaly detection method based on traffic data sample statistics and balanced information entropy estimation
A technology for traffic data and network anomalies, applied in transmission systems, electrical components, etc., can solve the problems of short data collection time and inability to use directly, and achieve the effect of facilitating subsequent calculation processing, strong applicability, and reducing the degree of deviation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
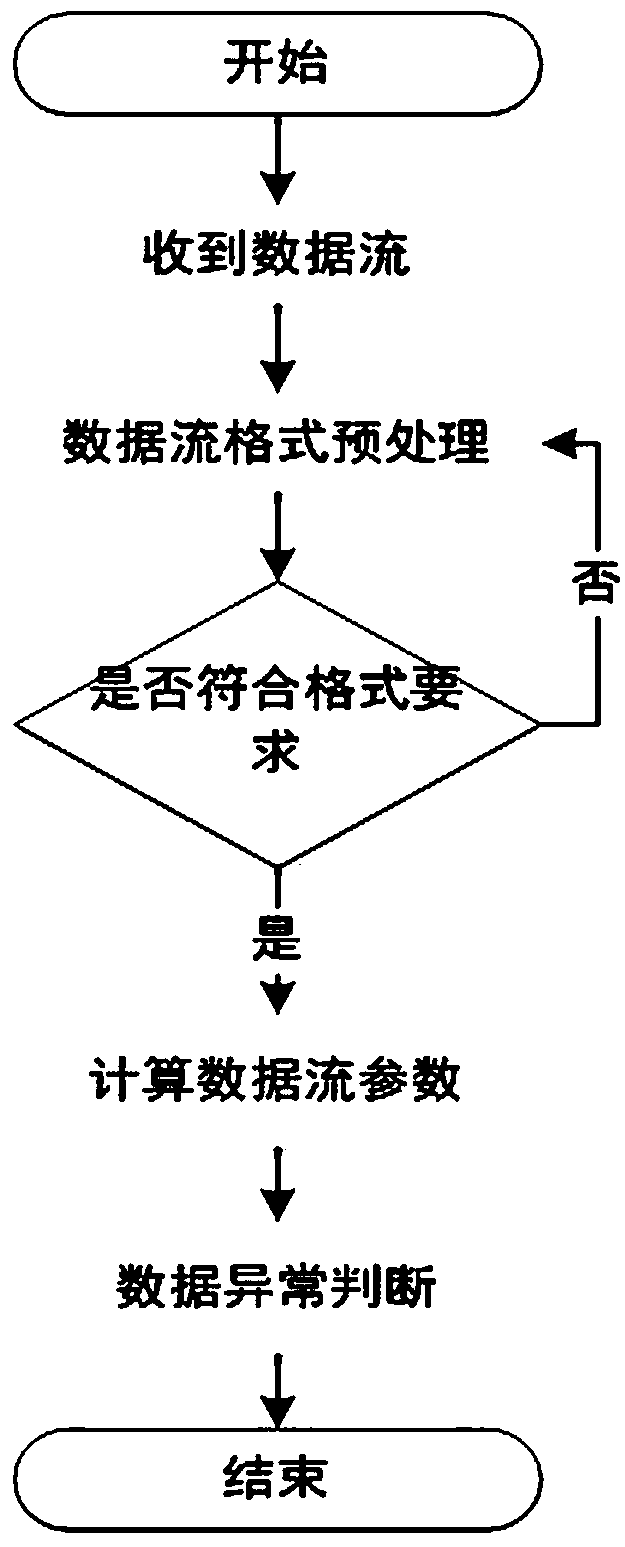
[0052] As one of the most basic implementations of the present invention, this embodiment discloses a network anomaly detection method based on flow data sample statistics and balanced information entropy estimation, such as figure 1 shown, including the following steps:
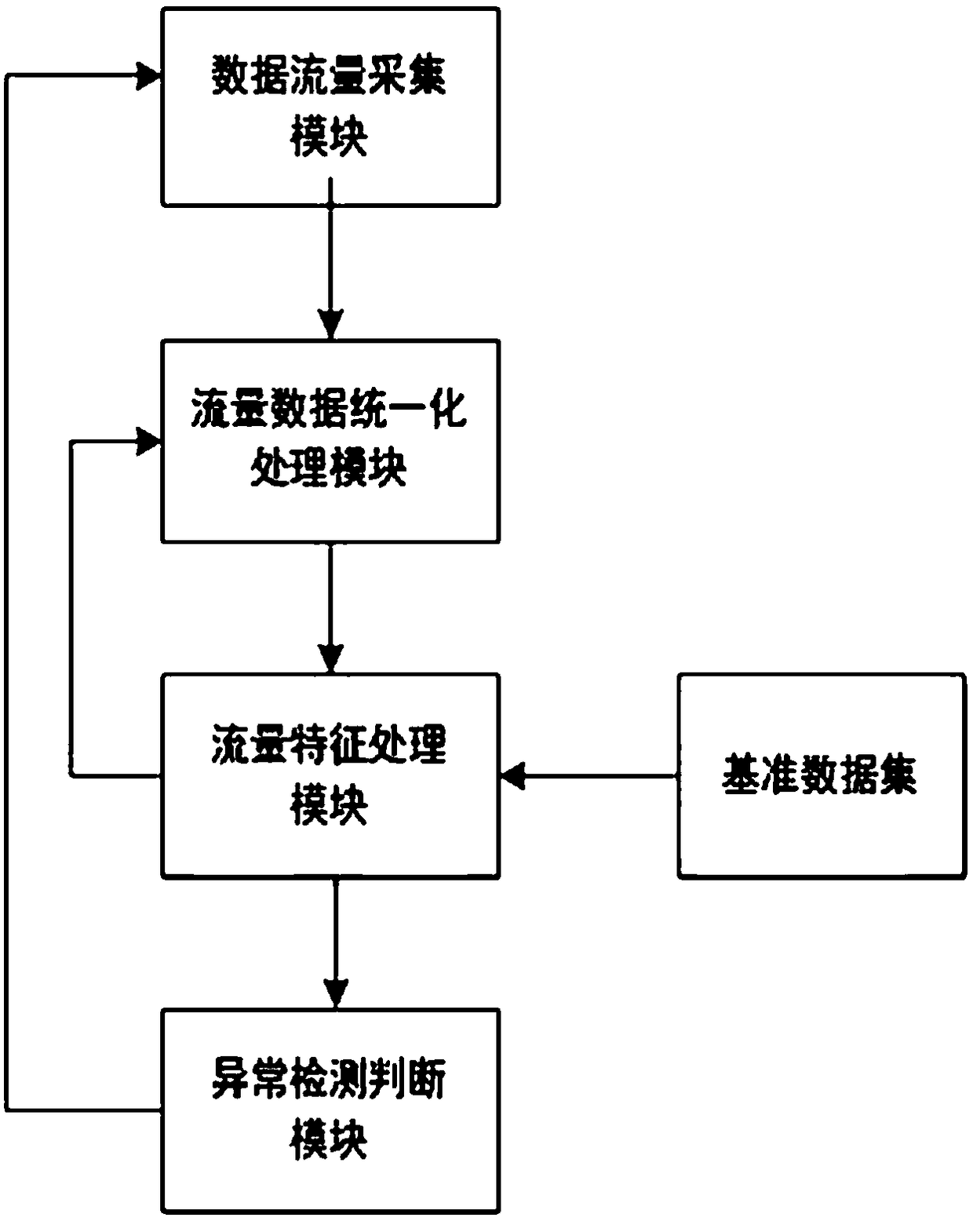
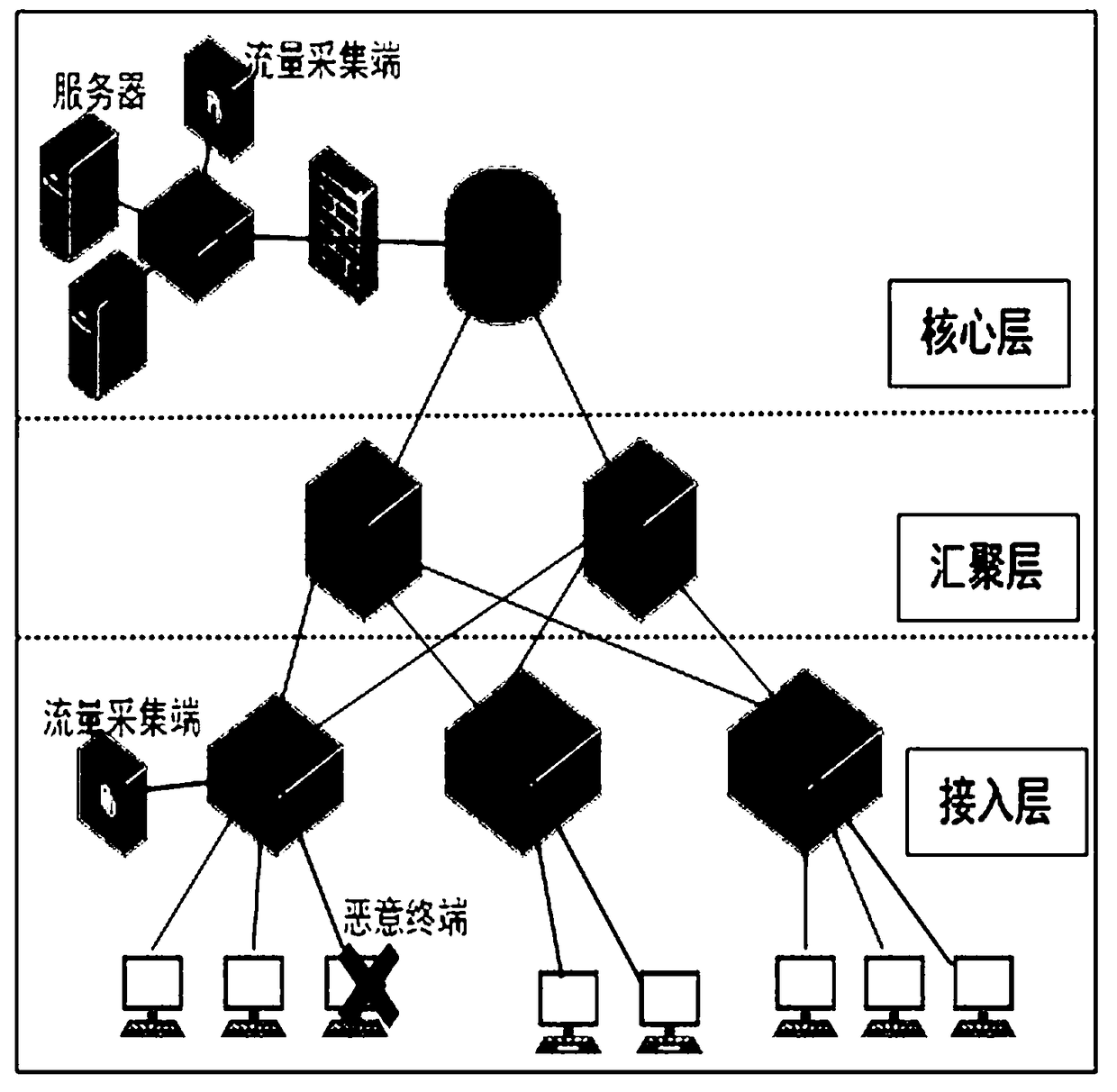
[0053] Traffic data collection, collect the traffic data of the core layer ingress and egress ports and the access layer ingress and egress ports where malicious terminals are located, and collect public benchmark data at the same time;
[0054] Unify the data format, and unify the data obtained by collecting traffic data into JSON format;
[0055] Data feature analysis, using the information entropy balance estimation method to estimate the overall distribution information for the traffic data features after the data format is unified;
[0056] Network anomaly judgment, based on the information obtained from the analysis of network traffic data characteristics, adopts the method of K-S statistical test to ...
Embodiment 2
[0059] As one of the most basic implementations of the present invention, this embodiment discloses a network anomaly detection method based on flow data sample statistics and balanced information entropy estimation, such as figure 1 shown, including the following steps:
[0060] Flow Data Collection
[0061] Collect the traffic data of the core layer ingress and egress ports and the access layer ingress and egress ports where the malicious terminal is located, and at the same time collect public benchmark data; the traffic data acquisition is to use open source tools TCPtrace, Wireshark, Ethereal, Snort or commercial software and hardware systems Cisco Netflow, network One or more of time machine NTM and Huawei Netstream, collect and obtain the flow data of the core layer ingress and egress ports and the access layer ingress and egress ports where the malicious terminal is located, as well as public benchmark data by means of serial connection, bypass or port mirroring; The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com