Identity authentication method adopting multiple authentication, identity verification equipment and identity authentication system
An identity authentication and multi-authentication technology, which is applied in the field of multi-authentication identity authentication methods, identity verification equipment and identity authentication systems, can solve the problems of easy copying or stealing of verification, inconvenient application, low security, etc., and reduce communication The number of applications, the speed of authentication, and the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
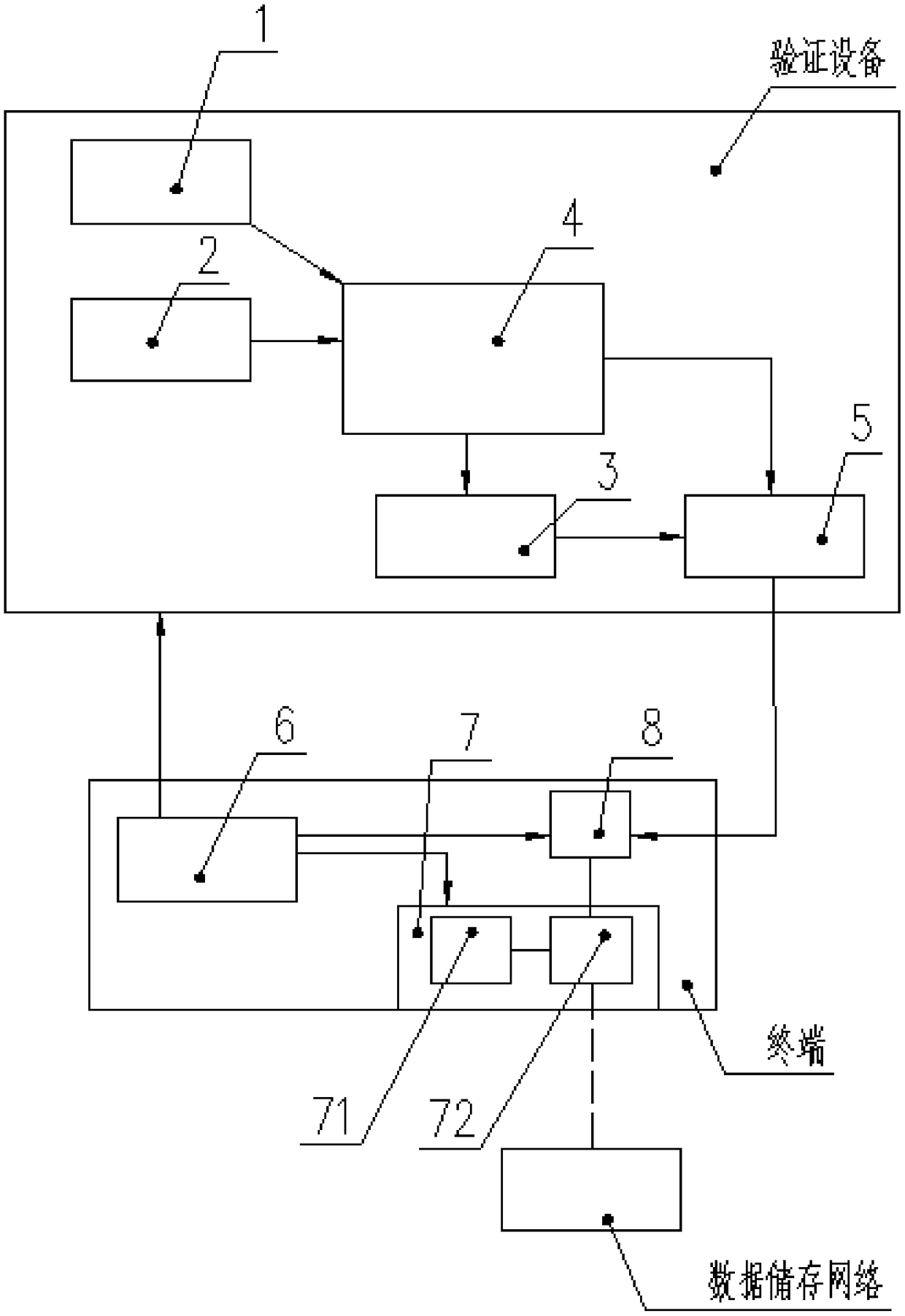
[0045] The multi-authentication identity authentication method of the present invention is combined with an identity authentication device to be set and applied in an identity authentication system.
[0046] Specifically, the identity authentication system includes a verification device 10 and a plurality of terminals 20, the verification device includes a biometric module 1 for obtaining external biological information, and a read-only storage unit 2 that records independent physical information. , a temporary storage unit 3, a processing unit 4 and a data transmission module 5; the output end of the biometric identification module 1 is connected to the first input end of the processing unit 4; the output end of the read-only storage unit 2 is connected to the The second input end of the processing unit 4; the first output end of the processing unit 4 is connected to the input end of the temporary storage unit 3, and the second output end of the processing unit 4 is connected ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com