Method, device and storage medium for cooperative signature based on sm2 algorithm
An algorithm, a technology for signing messages, applied in the fields of information security and cryptography, can solve problems such as forged signatures, and achieve the effect of protecting integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0120]Embodiments of the present invention provide a collaborative signature method, device and storage medium based on the SM2 algorithm to solve the technical problem in the prior art that signature messages are easily forged.
[0121] The technical solution in the embodiment of the present application is to solve the above-mentioned technical problems, and the general idea is as follows:
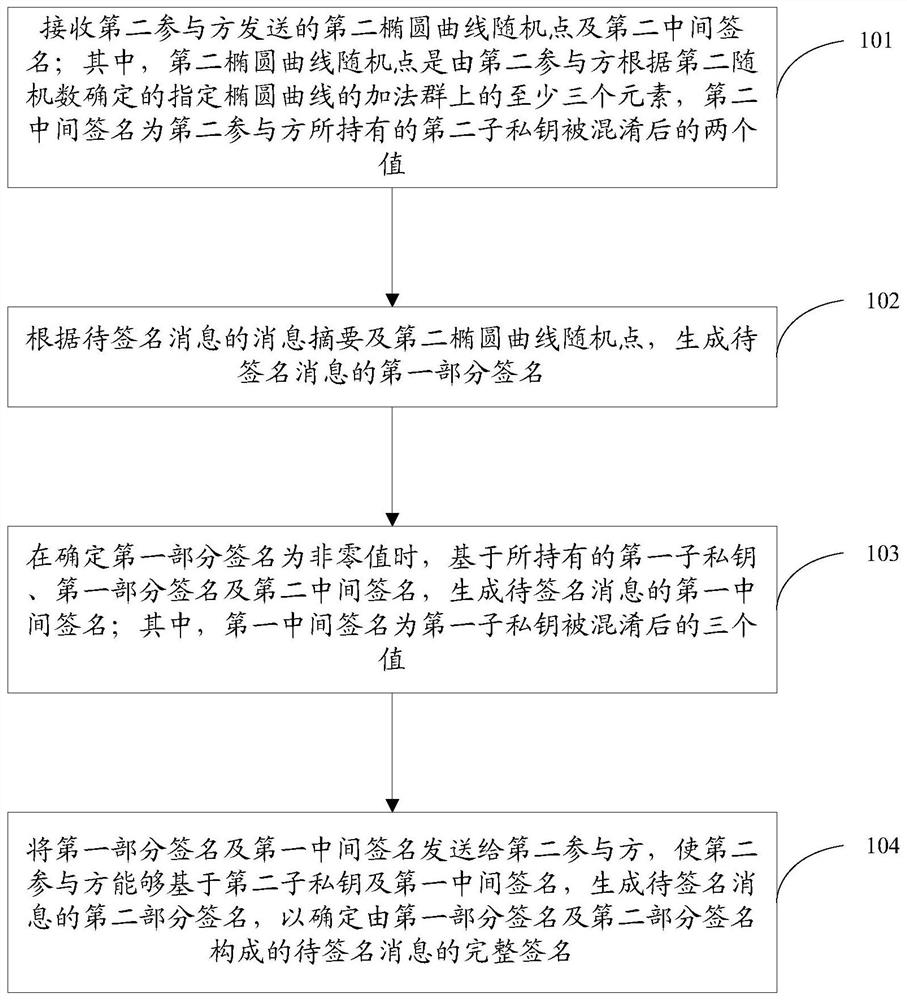
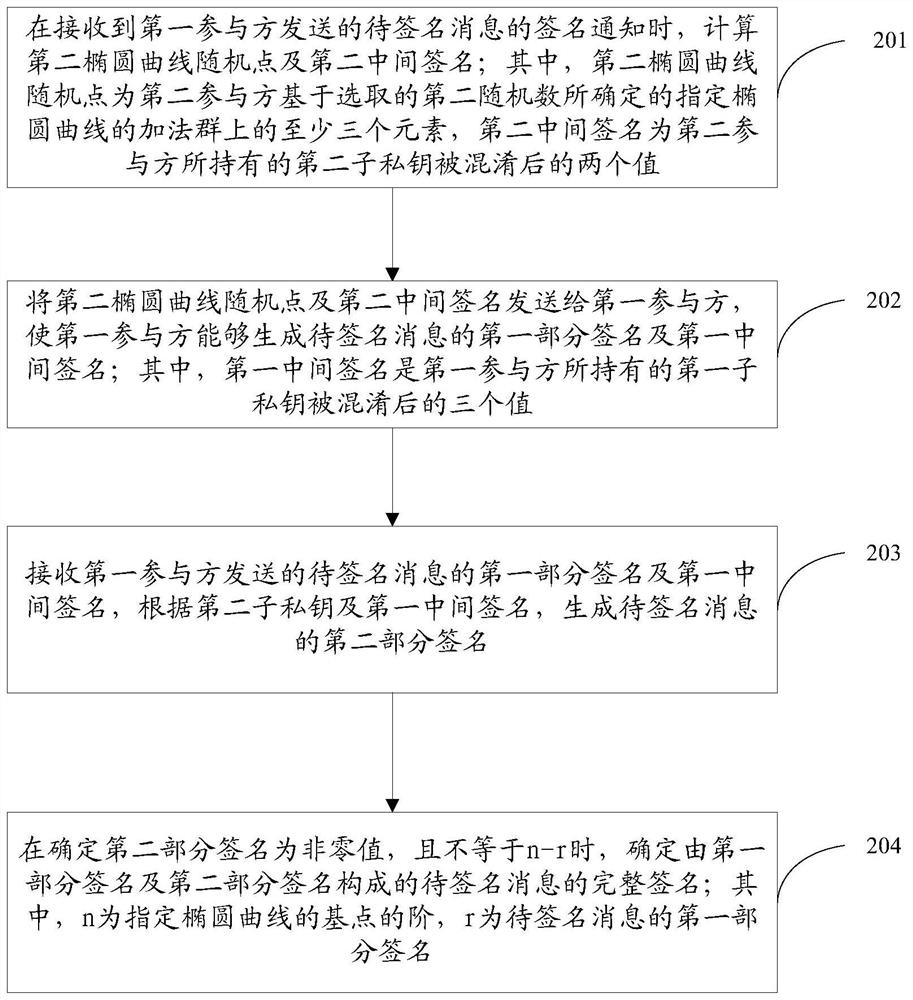
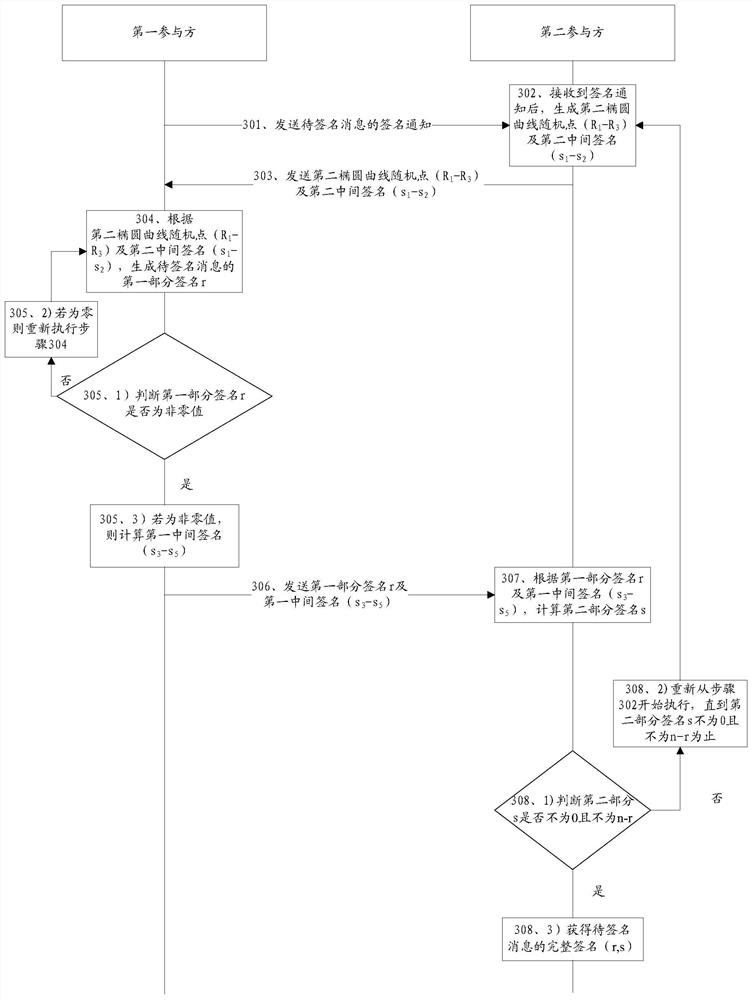
[0122] A method for collaborative signature based on the SM2 algorithm is provided, including: receiving a second elliptic curve random point and a second intermediate signature sent by a second participant; wherein, the second elliptic curve random point is generated by the second participant according to the second At least three elements on the additive group of the specified elliptic curve determined by the random number, the second intermediate signature is the two values after the second sub-private key held by the second participant is confused; according to the message digest of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com