Credit-fraud detection model train method, credit-fraud detection method and device
A detection model and technology to be detected, applied in the field of information processing, can solve problems such as low efficiency, complexity, and large amount of information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
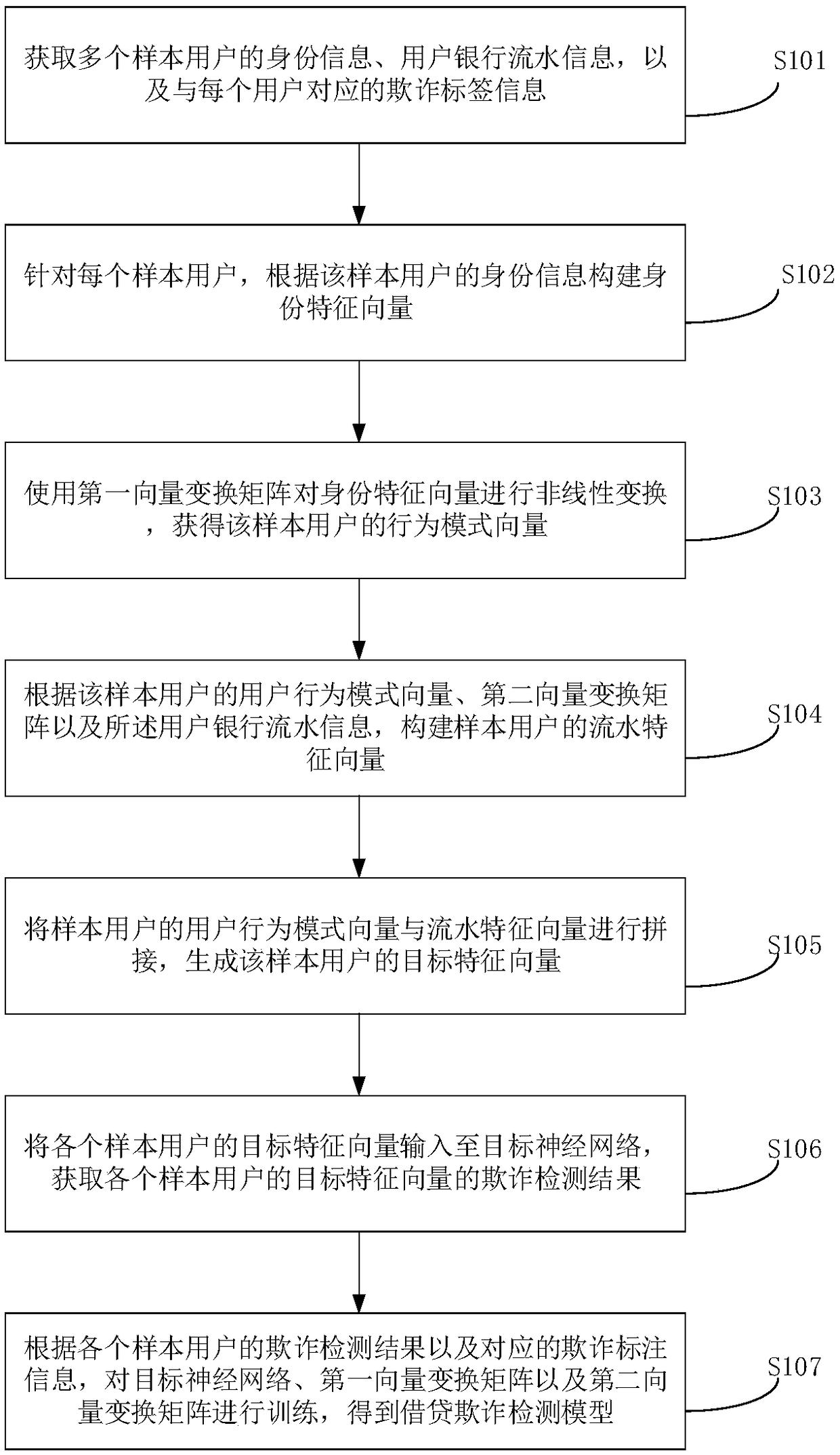
[0167] see figure 1 As shown, it is a flow chart of the loan fraud detection model training method provided in Embodiment 1 of the present application, the method includes steps S101 to S106, wherein:
[0168] S101. Obtain identity information of multiple sample users, user bank statement information, and fraud tag information corresponding to each user.
[0169] In the specific implementation, when the sample users are screened, they are screened from users who have initiated loan applications and have issued loans to them.
[0170] The user's identity information is related information used to characterize the user's identity. It is not just a single identity information such as ID number and name, but a user's identity based on a series of social attributes. For example, the identity information It can include: user education, occupation, region, gender, age, family relationship, credit information on other platforms, asset status, etc.
[0171] The user's bank statement ...
Embodiment 2
[0305] see Image 6 As shown, Embodiment 2 of the present application also provides a loan fraud detection method, the method comprising:
[0306] S601. Obtain the identity information of the user to be detected and the bank statement information of the user.
[0307] S602. Based on the identity information of the user to be detected, construct an identity feature vector of the user to be detected
[0308] S603. Construct a behavior pattern vector of the user to be detected according to the identity feature vector of the user to be detected and the first vector transformation matrix.
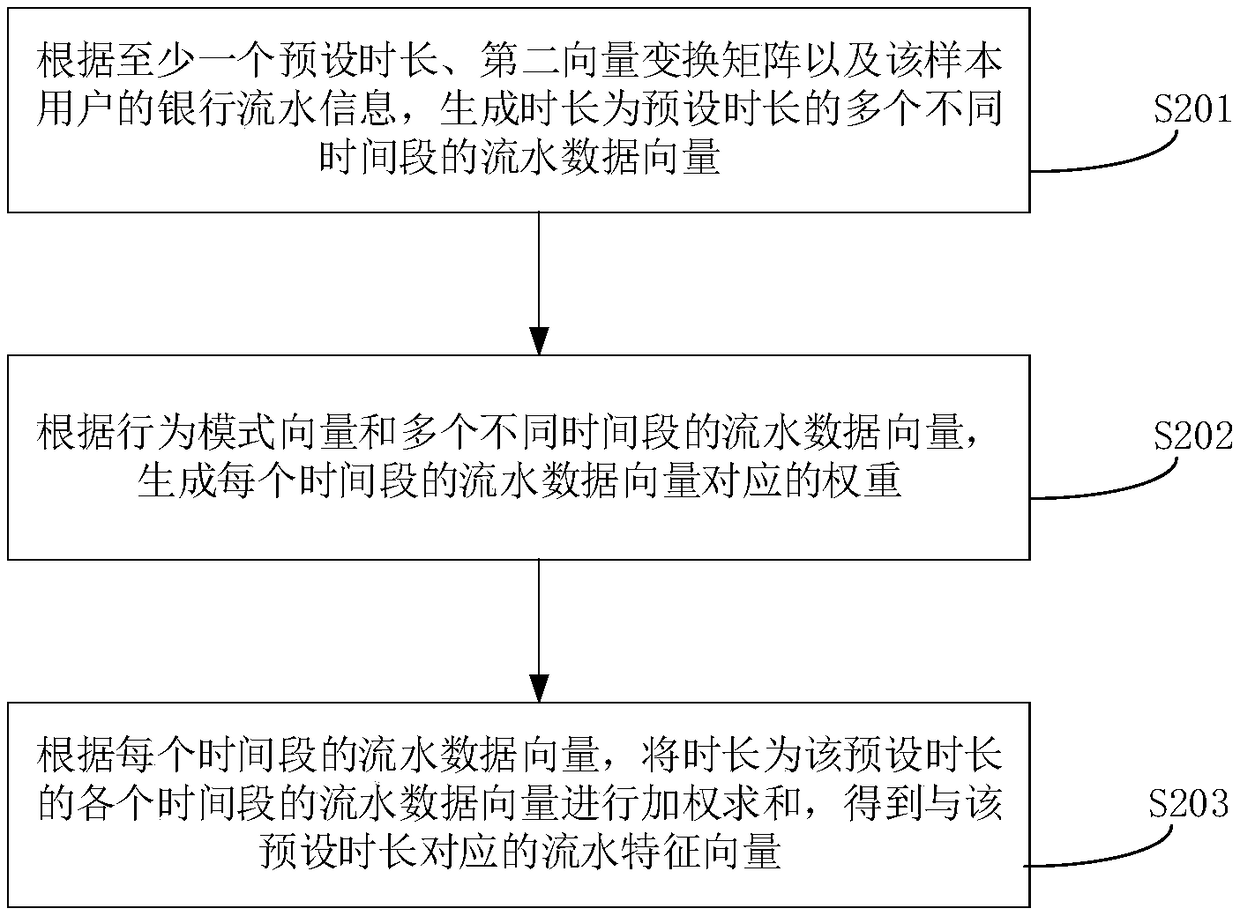
[0309] S604. According to the behavior pattern vector of the user to be detected, the second transformation matrix, and the bank statement information of the user, construct a flow feature vector of the user to be detected.
[0310] S605. Input the target feature vector of the user to be detected into the loan fraud detection model obtained through the loan fraud detection model training metho...
Embodiment 3
[0316] refer to Figure 7 As shown, it is a schematic diagram of a loan fraud detection model training device 700 provided in Embodiment 3 of the present application. A loan fraud detection model training device includes:
[0317] The first obtaining module 701 is used to obtain the identity information of a plurality of sample users, the user's bank statement information, and the fraud tag information corresponding to each user;
[0318] The first construction module 702 is configured to, for each sample user, construct an identity feature vector according to the identity information of the sample user, and use a first vector transformation matrix to perform nonlinear transformation on the identity feature vector to obtain the sample user behavior pattern vector;
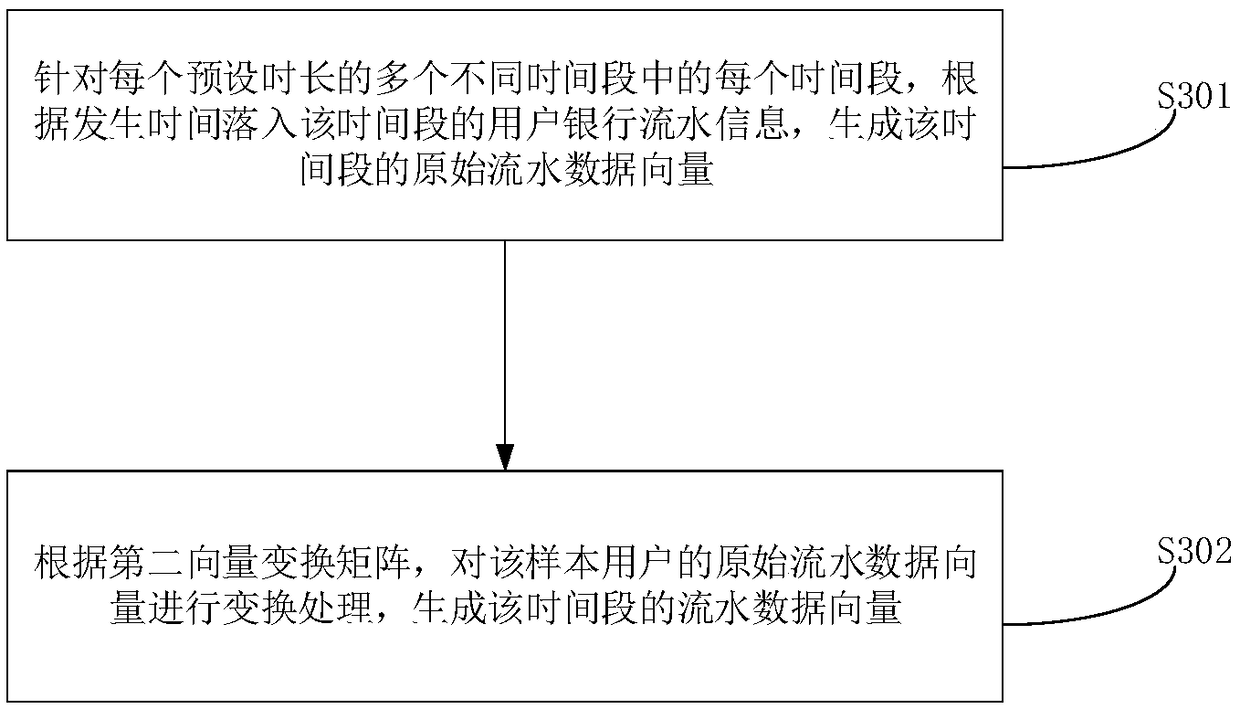
[0319] The second construction module 703 is used to construct the profile feature vector of the sample user according to the user behavior pattern vector of the sample user, the second vector transformation matri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com