A WAF reverse proxy method base on online traffic mirroring bypass
A reverse proxy and mirroring technology, applied in the field of network security, can solve the problem that WAF system testing cannot achieve both simulation and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
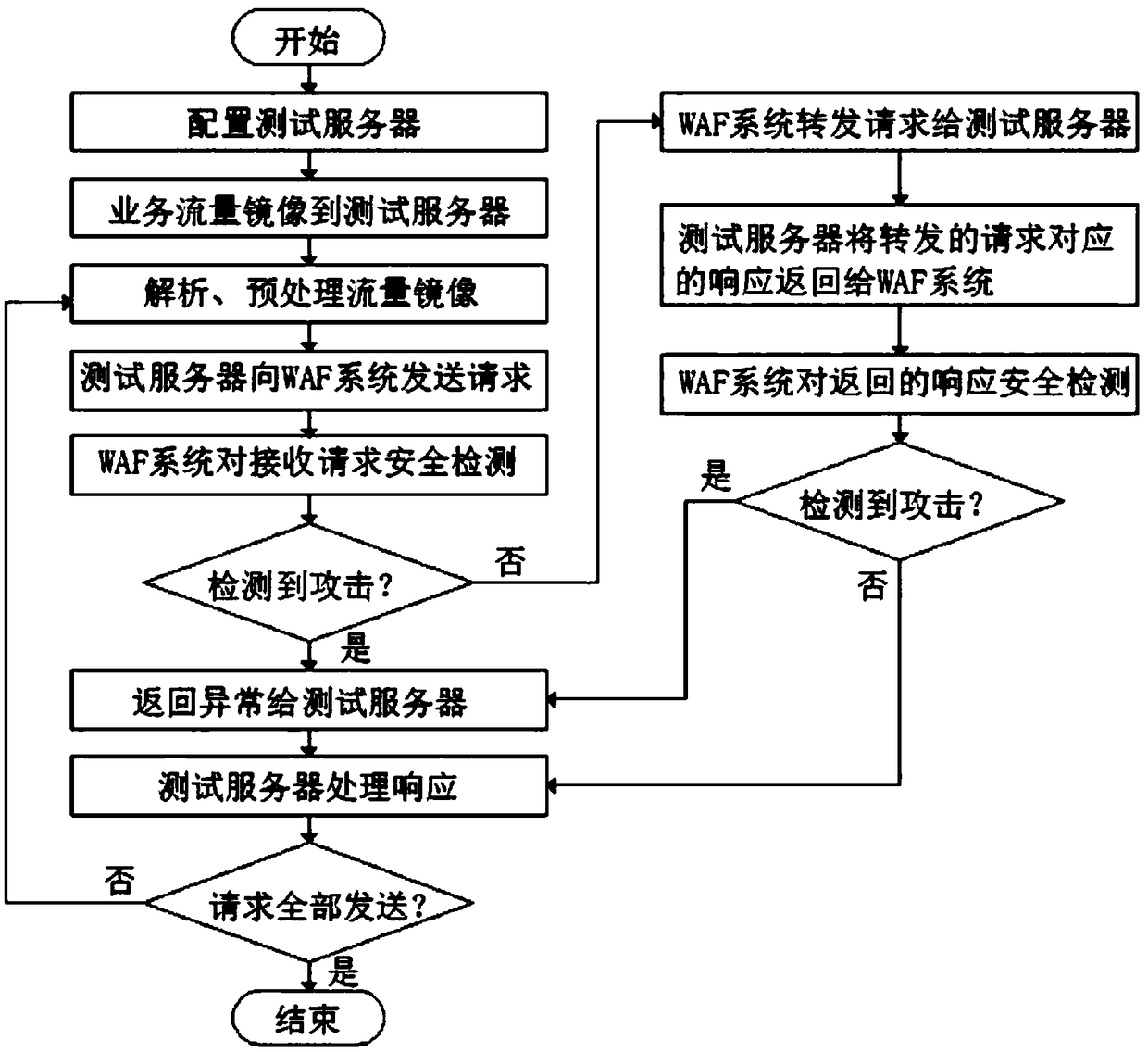
[0029] combined with figure 1 As shown, a method of bypassing WAF reverse proxy based on online traffic mirroring includes:
[0030] Step S100: configure a test server at the WAF system site;
[0031] Step S200: The test server mirrors the business traffic on the business server in real time:
[0032] Step S210: the user sends an http request to the load balancer;
[0033] Step S220: the load balancer forwards the http request to the service server;
[0034] Step S230: the business server mirrors the http request and the response to the http request to the test server through the network layer in real time by using a traffic mirroring program;
[0035] Step S300: The test server analyzes and preprocesses the requests and responses in the mirrored business traffic: preprocessing the requests includes assembling the TCP data packets of the same request, handling TCP out-of-order, packet loss, etc., and Add an xff header in the http header of the request to identify the real ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com