A continuous integration method based on vulnerability scanning platform
A vulnerability scanning and continuous integration technology, which is applied in the fields of platform integrity maintenance, instrumentation, electronic digital data processing, etc., can solve the problems of high incidence of security incidents and the inability of the vulnerability scanning platform to quickly respond to product releases, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] A continuous integration method based on a vulnerability scanning platform, including a continuous integration platform, a vulnerability scanning platform and a Jenkins server:
[0031] Step S100): the continuous integration platform calls the continuous integration interface of the vulnerability scanning platform to establish vulnerability scanning rules and scanning tasks, calls the Jenkins interface of the Jenkins server to create projects, build projects and obtain construction results;
[0032] Step S200): The Jenkins server completes the automated testing of the missing scan task on the continuous integration platform through the PipeLine pipeline scheduling.
[0033] The continuous integration platform establishes vulnerability scanning rules and scanning tasks by calling the continuous integration interface of the vulnerability scanning platform; the continuous integration platform calls the Jenkins interface of the Jenkins server to create projects, build projec...
Embodiment 2
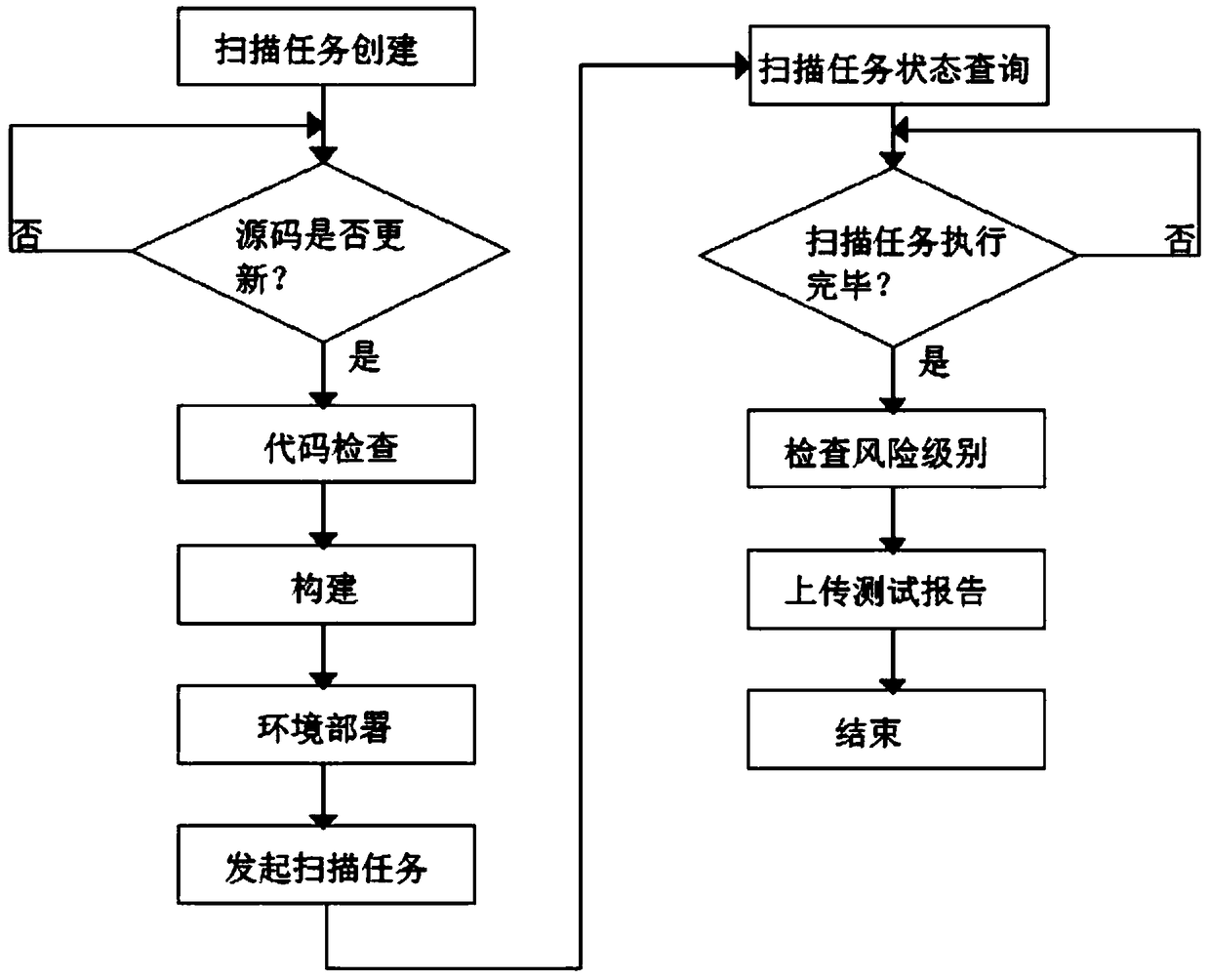
[0043] On the basis of Example 1, in conjunction with the attached figure 1 As shown, the step S200) specifically includes:
[0044] Step S210): the xml template of the Jenkins server defines the PipeLine pipeline;
[0045] Step S220): The build trigger is set to Poll SCM, and the source code is regularly checked and updated;
[0046] Step S230): Execute the construction action:
[0047] Step S231) environment deployment;
[0048] Step S232) Initiate a scan task by passing in the address of the vulnerability scanning platform and the scan task information in a parameterized manner, and return the task ID;
[0049] Step S233) According to the task ID returned in step S232), poll the scan task status until the task ends and check the risk level of the scan result;
[0050] Step S234) Upload the test report to the continuous integration platform.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com