Container mirror hierarchical encryption storage method based on Device Mapper
An encrypted storage and mirroring technology, which is applied in the container field, can solve the problems of sensitive data residual security and other issues, and achieve the effect of improving application security and realizing storage security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to better understand the present invention, the present invention will be described in detail below in conjunction with the accompanying drawings.
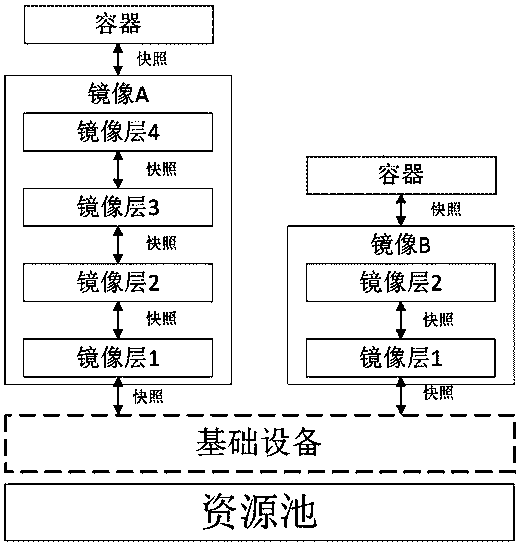
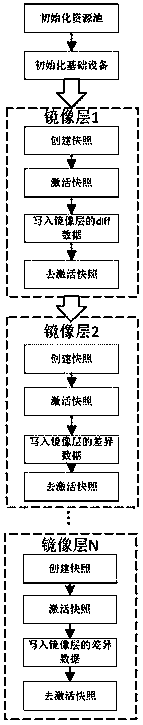
[0026] Such as figure 2 As shown, in the existing mirror layered storage, the snapshot of the first layer of the mirror is created from the basic device, and the subsequent mirror layers are created based on the snapshots of their parent mirror layers. The newly created snapshot already contains all the content of the parent layer, and then writes the content of the current mirror layer on this basis to form a new complete snapshot of the mirror layer.
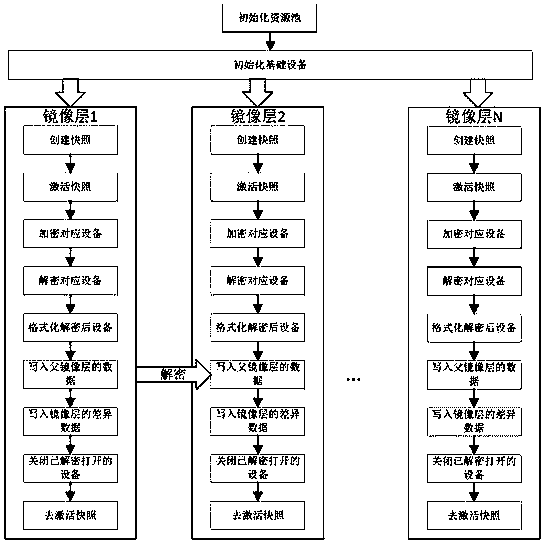
[0027] Such as image 3 As shown, the Device Mapper-based container image layered encryption storage method of the present invention, for image layer 1,
[0028] s11. Initialize the resource pool;
[0029] s12. Initialize the basic equipment;
[0030] s13. Create a snapshot corresponding to image layer 1;
[0031] s14, activate the snapshot;
[0032] s15. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com