A working method for locating a decentralized network security attack defense system
An attack defense system and network security technology, which is applied in the field of positioning decentralized network security attack defense system, can solve the problems of inability to attack defense and counterattack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
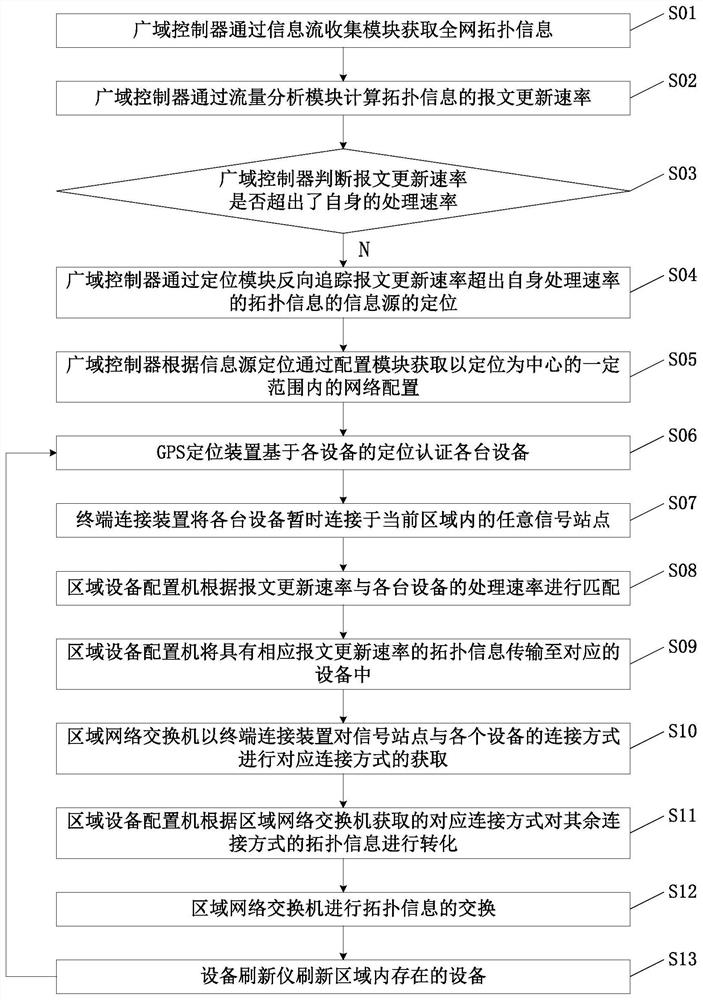
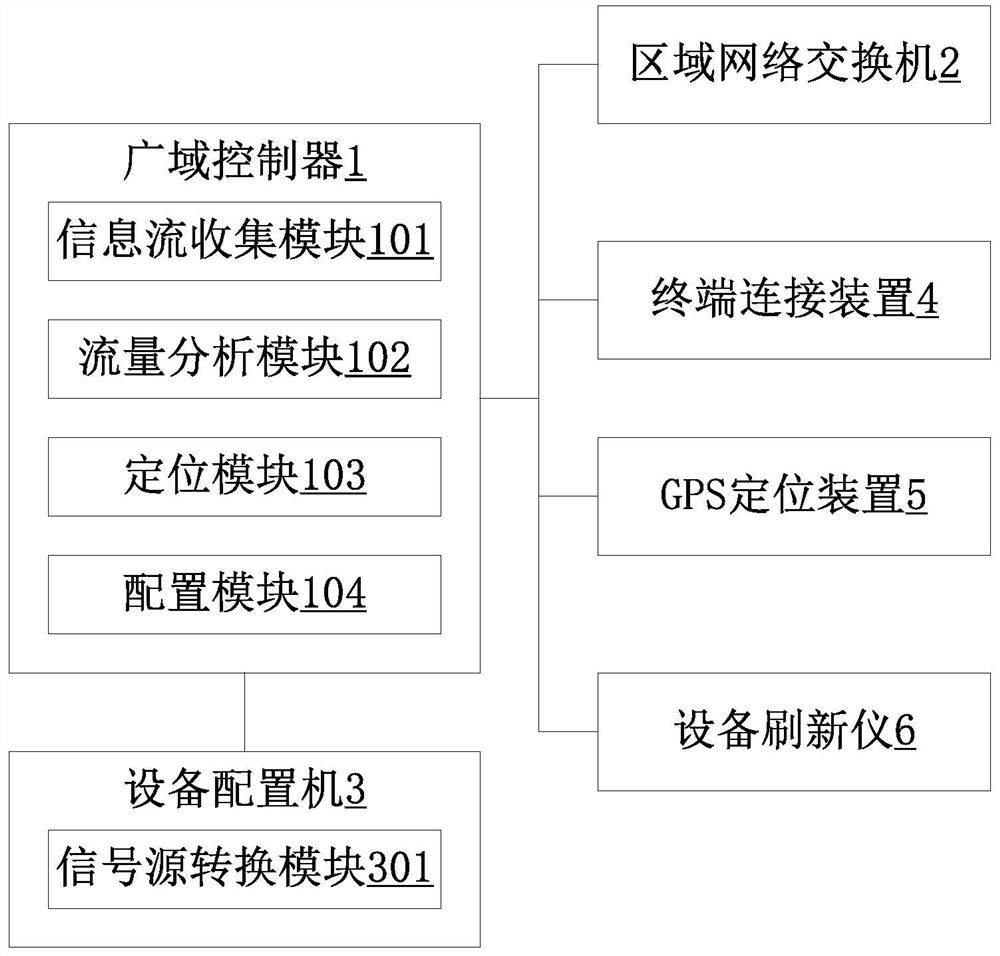
[0034]Referencefigure 1 ,figure 2. A working method for positioning a decentralized network security attack defense system for targeting an attack area and an attack area, the defense system comprising: comprising information flow collection module 101, a flow analysis module 102, a positioning module 103, and The Wide Area Controller 1 of the configuration module 104, the regional network switch 2, the regional device configurable machine 3, the terminal connection device 4, and the GPS positioning device 5 include the following steps:
[0035]S01: The Wide Area Controller 1 acquires all net topology information through the information flow collection module 101;
[0036]S02: The Wide Area Controller 1 calculates a message update rate of the topology information by the traffic analysis module 102;
[0037]S03: The Wide Area Controller 1 determines whether the message update rate exceeds its own processing rate, if yes, then proceeds to step S04;
[0038]S04: The Wide Area Controller 1 reverse ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com