Biometric feature recognition device and method
A biometric feature recognition and biometric technology, applied in character and pattern recognition, instruments, computer parts, etc., can solve the problem of data tampering or replacement, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
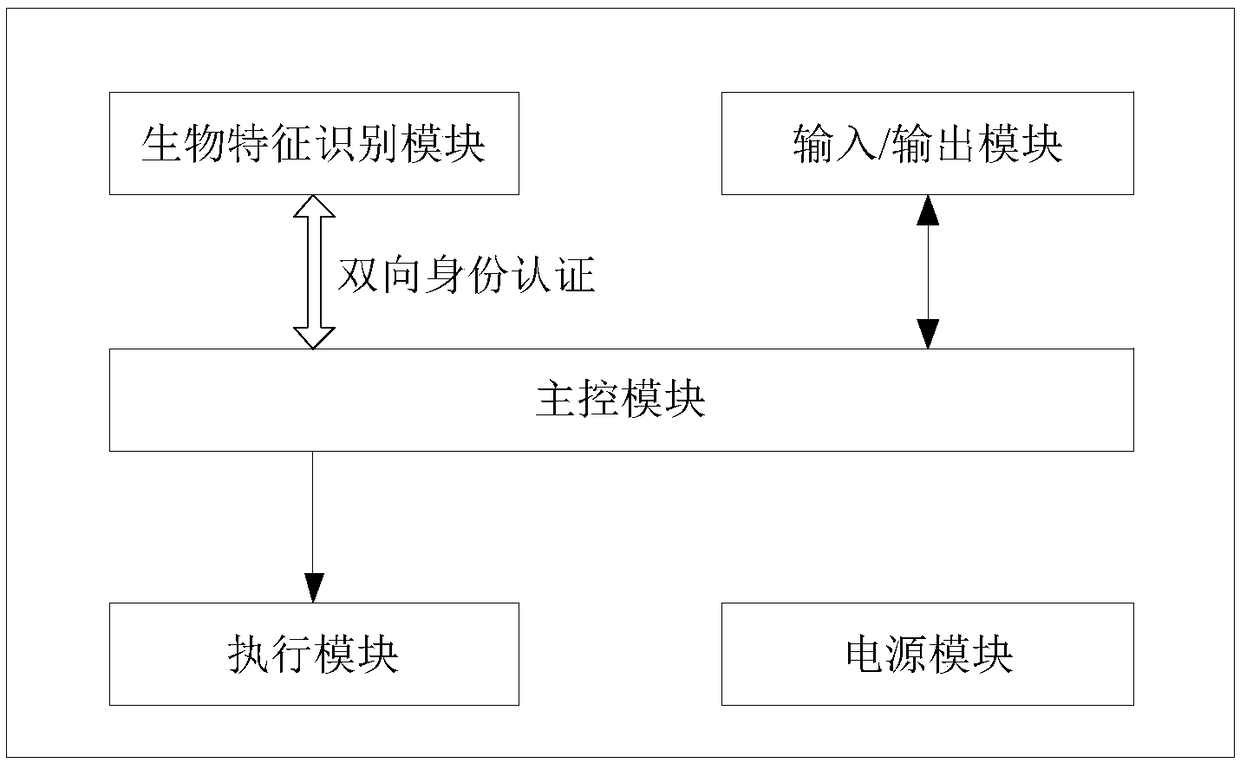
[0037] see figure 1 , the biometric identification device of this embodiment, including
[0038] The main control module is used to send control commands, receive various result instructions, generate keys, store keys, generate random numbers, encrypt operations, decrypt operations and random number checks;
[0039] The biometric identification module is used to receive control commands from the main control module, execute corresponding control commands and feed back biometric identification results to the main control module, store keys, generate random numbers, perform encryption operations, decryption operations, and random number inspections;
[0040] The execution module is used to receive the control command from the main control module, and execute the opening / closing of the mechanical or electronic switch;
[0041] The input / output module is used to realize the input of user information and operations, and the output of application information provided by the user; ...
Embodiment 2
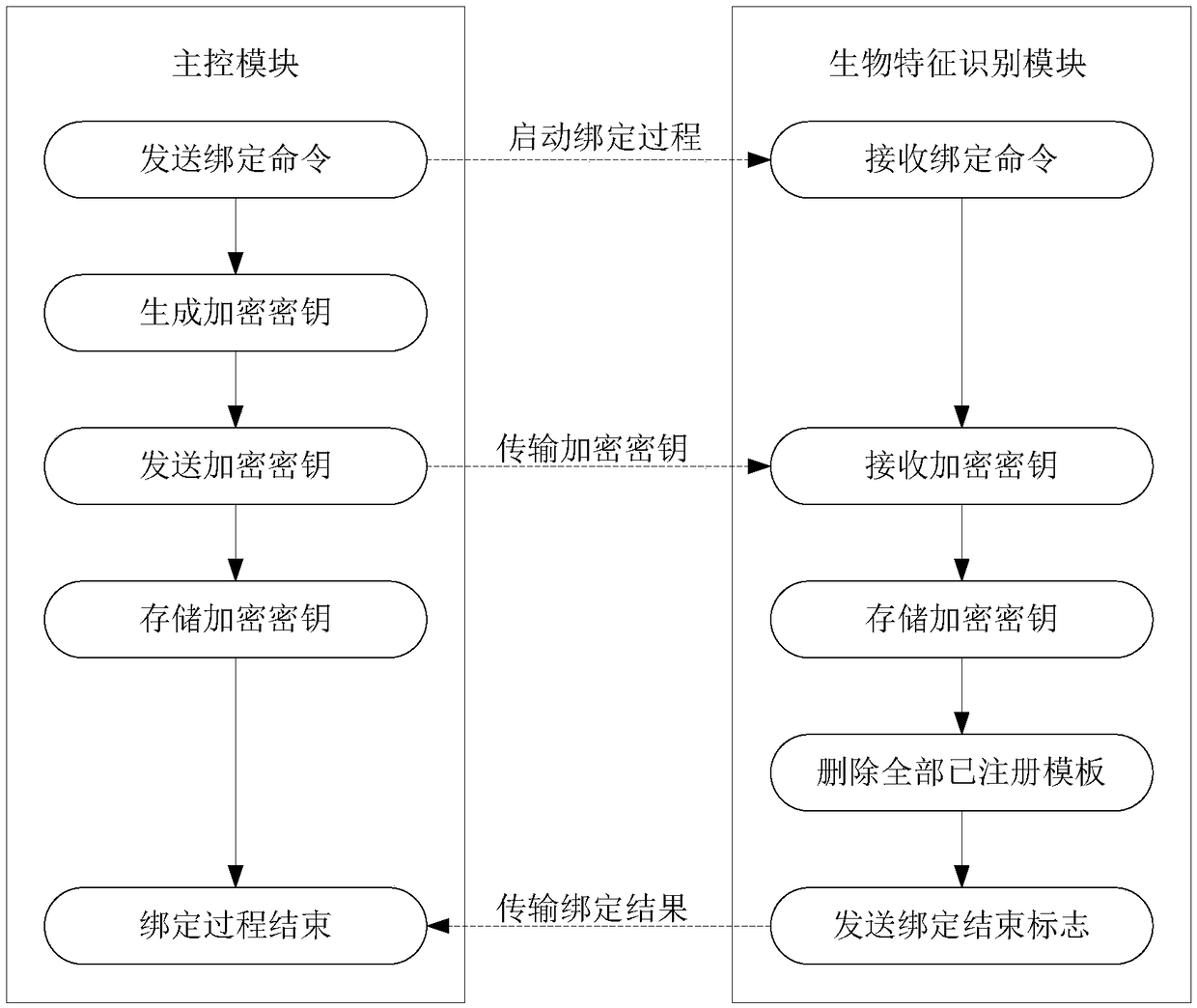
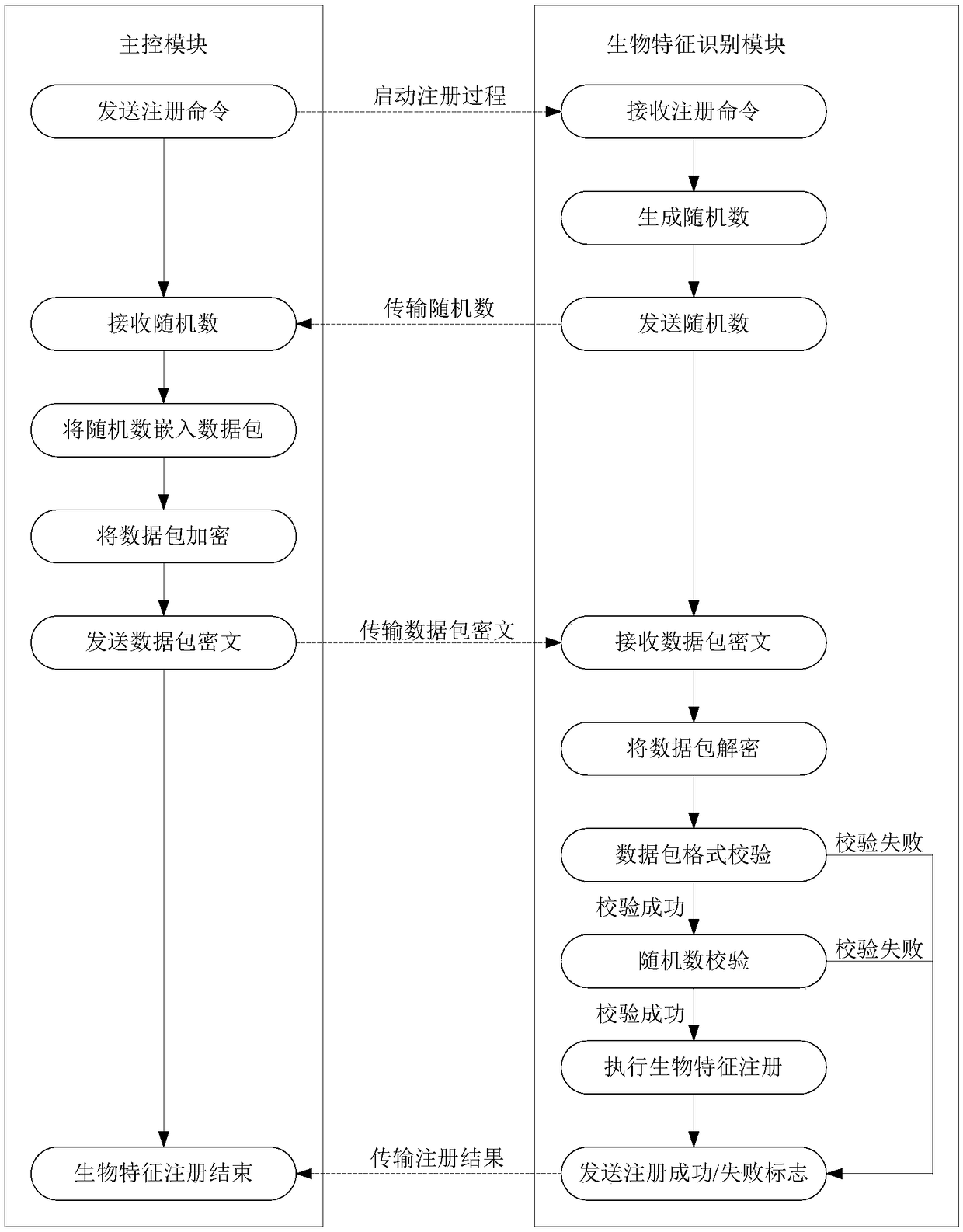
[0046] see Figure 2-4 , this embodiment provides a biometric identification method, using the biometric identification described in Embodiment 1, the steps are as follows:
[0047] 1) Before the biometric identification device is used for the first time, an identity binding operation is required. The main control module sends a binding command to the biometric identification module, and at the same time generates an encryption key for storage and transmits the encryption key to the biometric identification module; after receiving the binding command and the encryption key, the biometric identification module stores the encryption key , and send the binding success to the main control module. Identity binding operations can be repeated. If the main control module or the biometric identification module has not performed an identity binding operation, then store the key, if the main control module or the biometric identification module has performed an identity binding operati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com