An identity authentication method, device and system
An identity authentication and unified technology, applied in the field of information security, can solve the problems of increasing system development costs and reducing the efficiency of identity authentication management, and achieve the effect of saving development costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
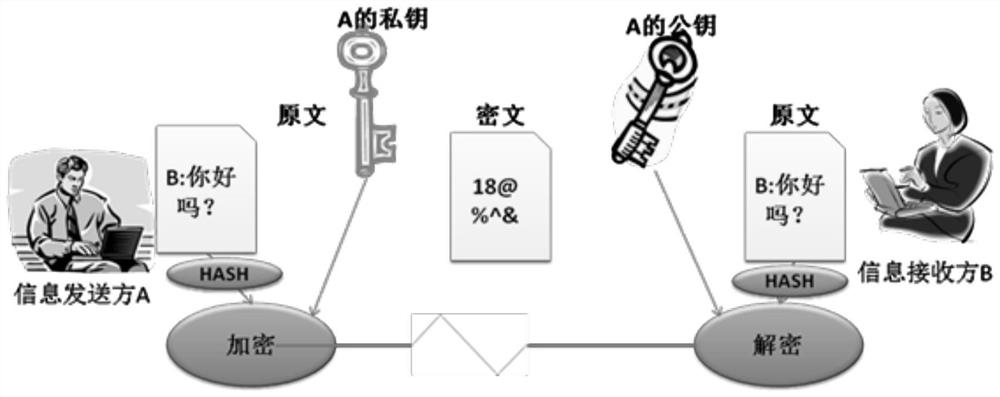
[0054] With the development of Internet technology and the continuous improvement of informatization level, the company builds more and more information systems to support its own business development. In each information system, user identity authentication is required to ensure business security. Therefore, in the system design stage, an identity authentication module is usually established for each system that requires identity authentication to meet the signature verification requirements of the system.
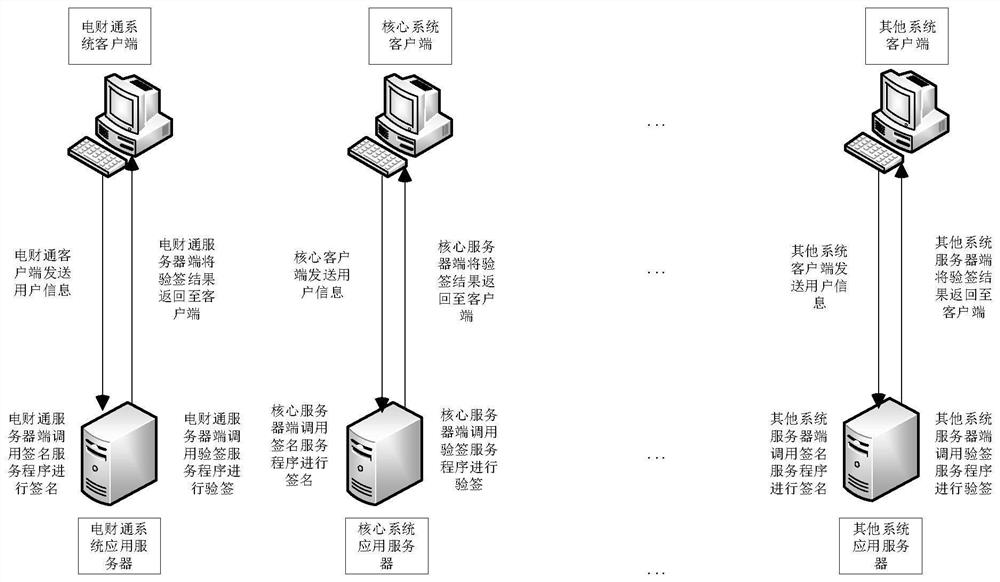
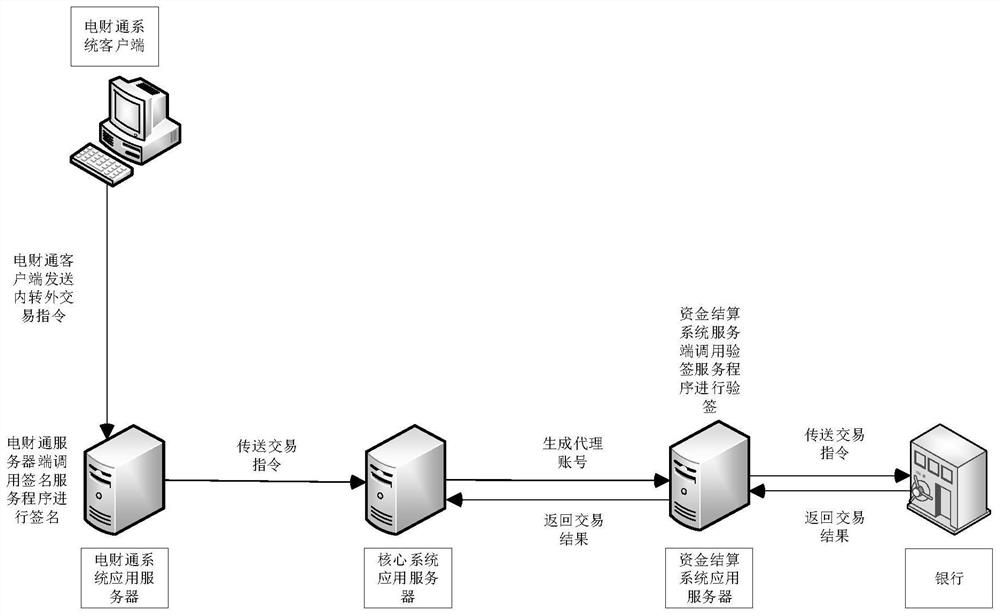
[0055] Assuming that a company involved in e-commerce has information systems such as Diancaitong system, core system, and fund settlement system, and deploys application servers for each system separately, the digital signature verification process when a user logs in to the information system is as follows: figure 2 shown.
[0056] When users of the company's information system (core system, Diancaitong system, etc.) log in to the information system (core system, Dianc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com