Safety verification method and device and mobile terminal
A technology for security verification and mobile terminals, which is applied in the field of devices and mobile terminals, and security verification methods, and can solve problems such as inability to meet mobile terminal security verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
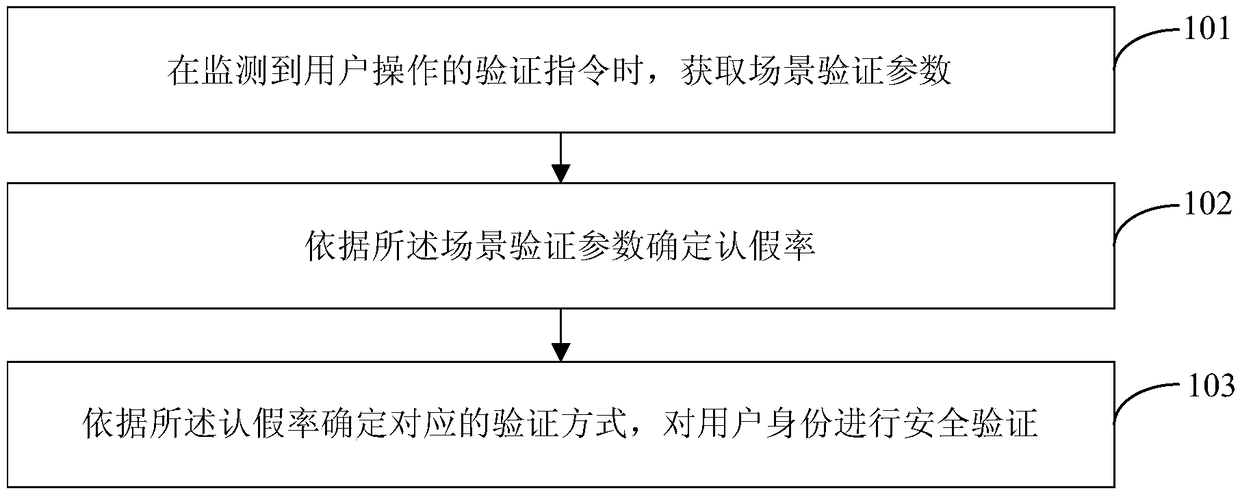
[0027] refer to figure 1 , shows a flow chart of steps of a security verification method provided by an embodiment of the present invention, the security verification method can be applied to a mobile terminal, and may specifically include the following steps:
[0028] Step 101: Obtain scene verification parameters when a verification instruction operated by a user is detected.
[0029] The password protection method in the embodiments of the present invention can be applied to mobile terminals, and the mobile terminals can include mobile electronic devices such as mobile phones and PADs.
[0030] The scene verification parameter may include at least one of a time parameter, a location parameter, an application type parameter and a payment amount parameter.
[0031] It can be understood that any one of the above parameters may be selected as the scene verification parameter, or a combination of various parameters may be selected, which is not limited in this embodiment of the...
Embodiment 2
[0063] refer to figure 2 , shows a flow chart of steps of a security verification method provided by an embodiment of the present invention, the security verification method can be applied to a mobile terminal, and may specifically include the following steps:
[0064] Step 201: Collect at least one piece of vital sign information of the user after receiving the user's verification input instruction.
[0065] In the embodiment of the present invention, the verification entry instruction can be an instruction for the user to click on a certain biometric entry (such as fingerprint entry, etc.), or it can be the user's input of biometric voice information, and the system can perform real-time monitoring. When entering an instruction, at least one vital sign information of the user is collected.
[0066] When the user enters a certain vital sign information, a button that requires the user to enter other vital sign information can pop up on the display screen of the mobile termi...
Embodiment 3
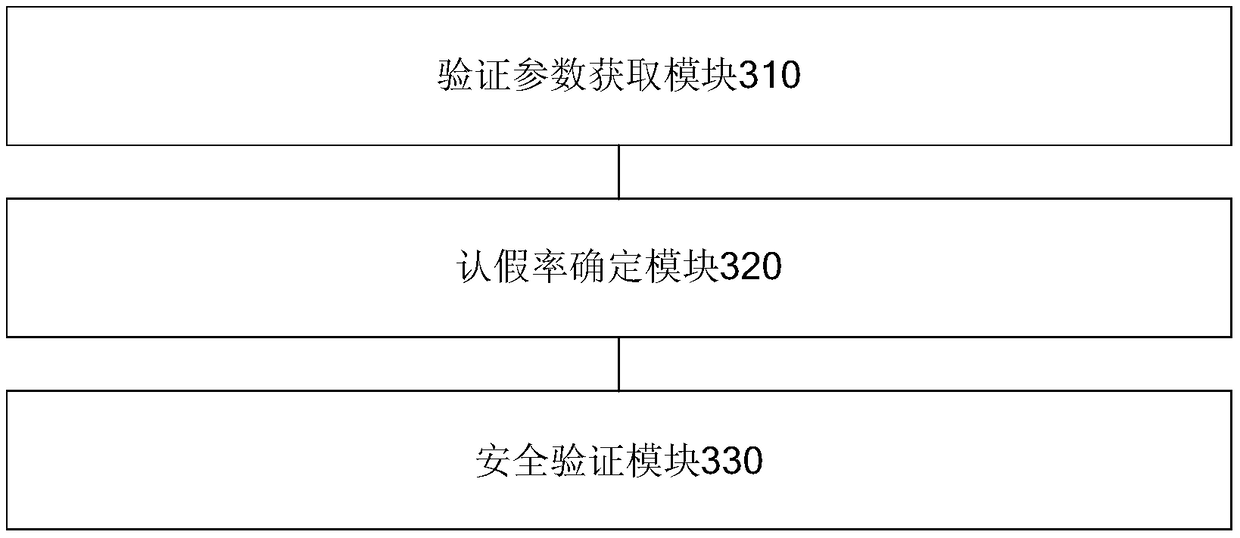
[0102] refer to image 3 , which shows a schematic structural diagram of a security verification device provided by an embodiment of the present invention, which may specifically include:
[0103] The verification parameter acquisition module 310 is used to obtain the scene verification parameters when monitoring the verification instruction of the user operation; the false recognition rate calculation module 320 is used to determine the false recognition rate according to the scene verification parameters; the security verification module 330 is used for A corresponding verification method is determined according to the false recognition rate, so as to perform security verification on the identity of the user.
[0104] Preferably, the scene verification parameters include at least one of time parameters, location parameters, application type parameters and payment amount parameters.
[0105] Preferably, the false recognition rate determination module 320 includes: a safety f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com