Method and device for realizing VoLTE IMS registration
A technology of successful registration and registration request message, applied in security devices, wireless communication, transmission systems, etc., can solve the problems of low VoLTEIMS registration success rate and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
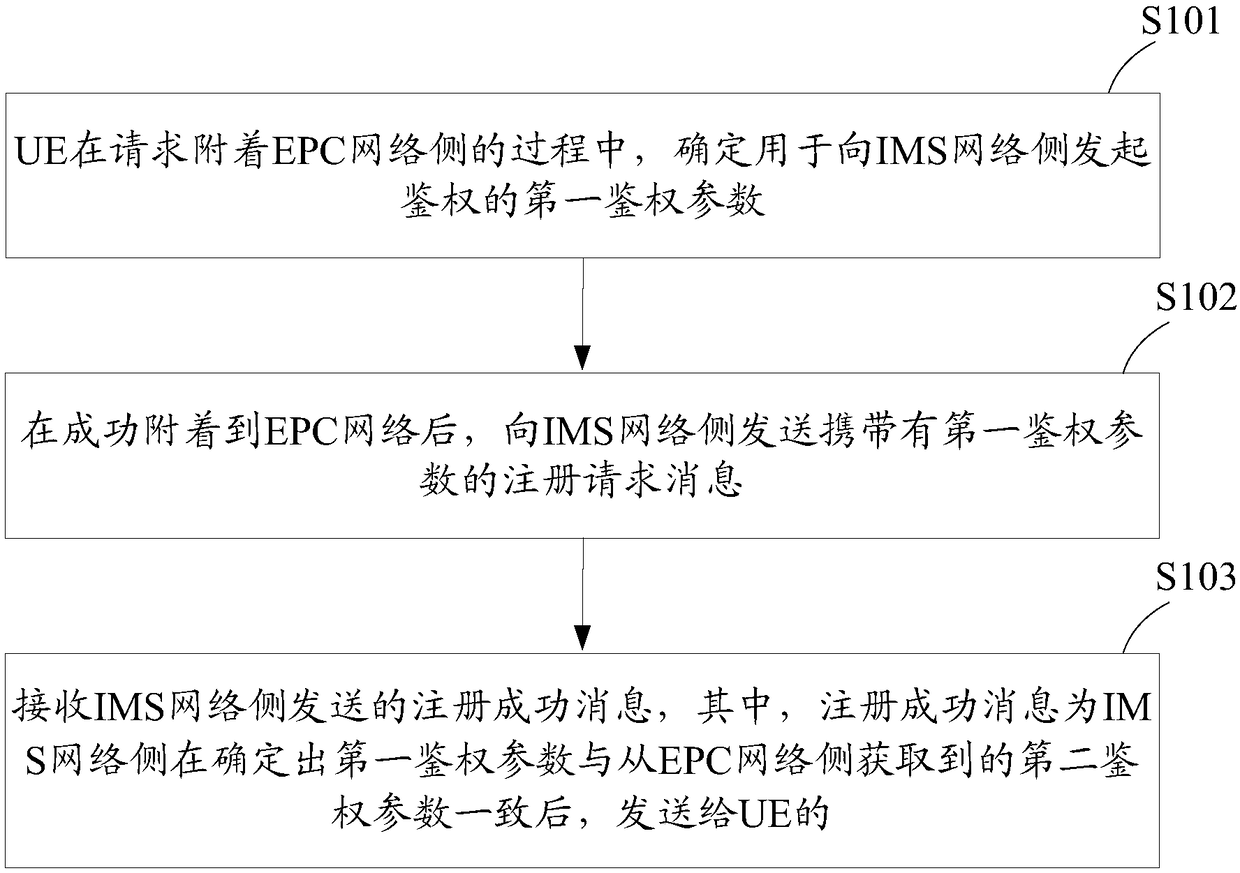
[0049] like figure 1 As shown, it is a flowchart of a method for implementing VoLTE IMS registration provided by Embodiment 1 of the present application, including the following steps:
[0050] S101: During the process of requesting to attach to the EPC network side, the UE determines a first authentication parameter for initiating authentication to the IMS network side;
[0051] Specifically, the first authentication parameter for initiating authentication to the IMS network side may be determined in the following manner: after sending the attach request message to the EPC network side, receiving the four-tuple authentication vector sent by the EPC network side The authentication request, and according to the four-tuple authentication vector, calculate the number of responses, and determine the number of responses as the first authentication parameter for initiating authentication to the IMS network side.
[0052] S102: After successfully attaching to the EPC network, send a...
Embodiment 2
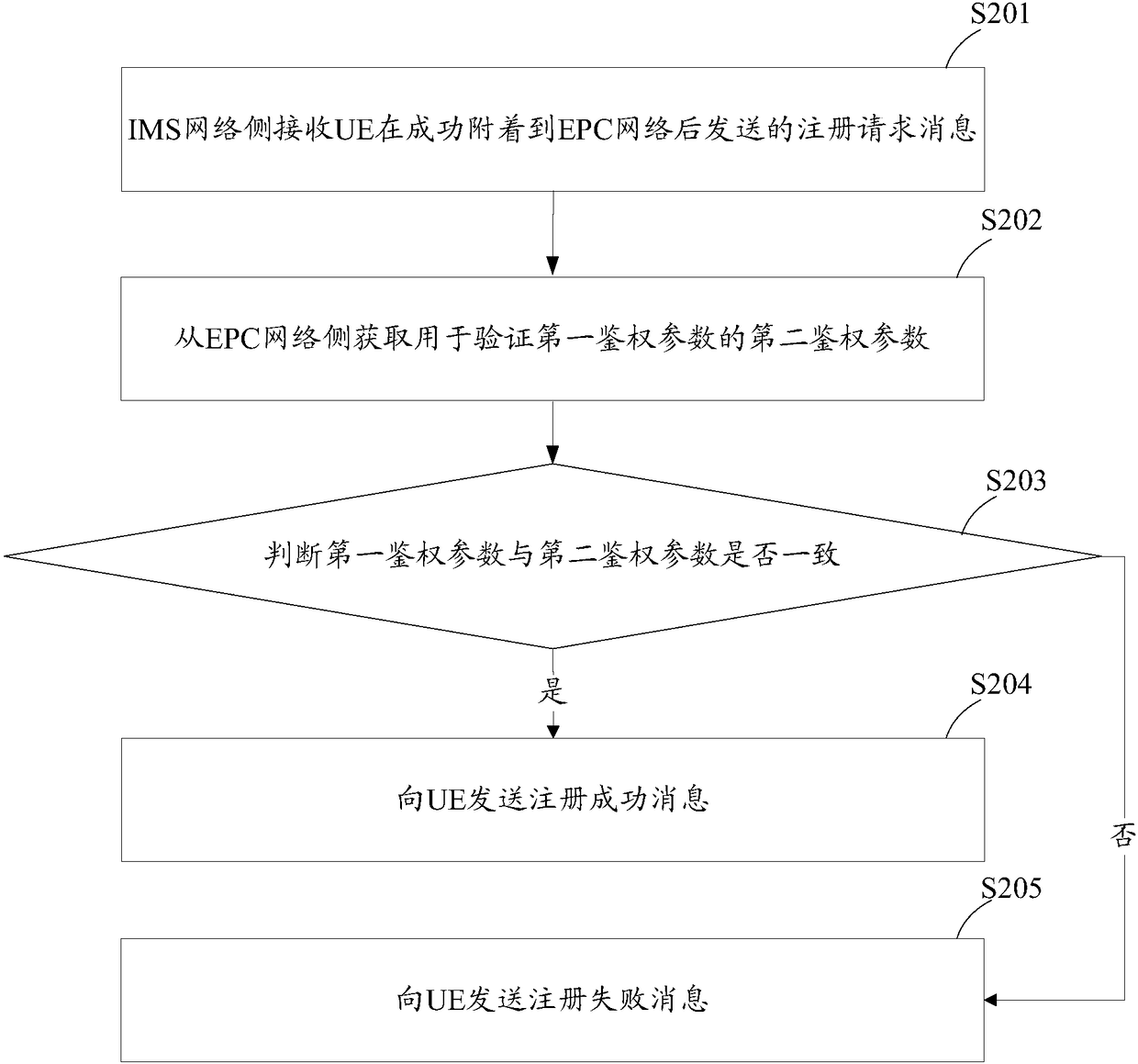
[0056] like figure 2 As shown, the flow chart of the method for implementing VoLTE IMS registration provided by Embodiment 2 of the present application includes the following steps:
[0057] S201: The IMS network side receives a registration request message sent by the UE after successfully attaching to the EPC network, wherein the registration request message carries a first authentication parameter for initiating authentication to the IMS network side, and the first authentication parameter It is determined by the UE during the process of requesting to attach to the EPC network.
[0058] S202: Obtain a second authentication parameter used to verify the first authentication parameter from the EPC network side.
[0059] Specifically, the IMS network side may send a multimedia authentication request MAR message to the EPC network side, for requesting to obtain authentication information used to verify the first authentication parameter, and may subsequently receive the second...
Embodiment 3
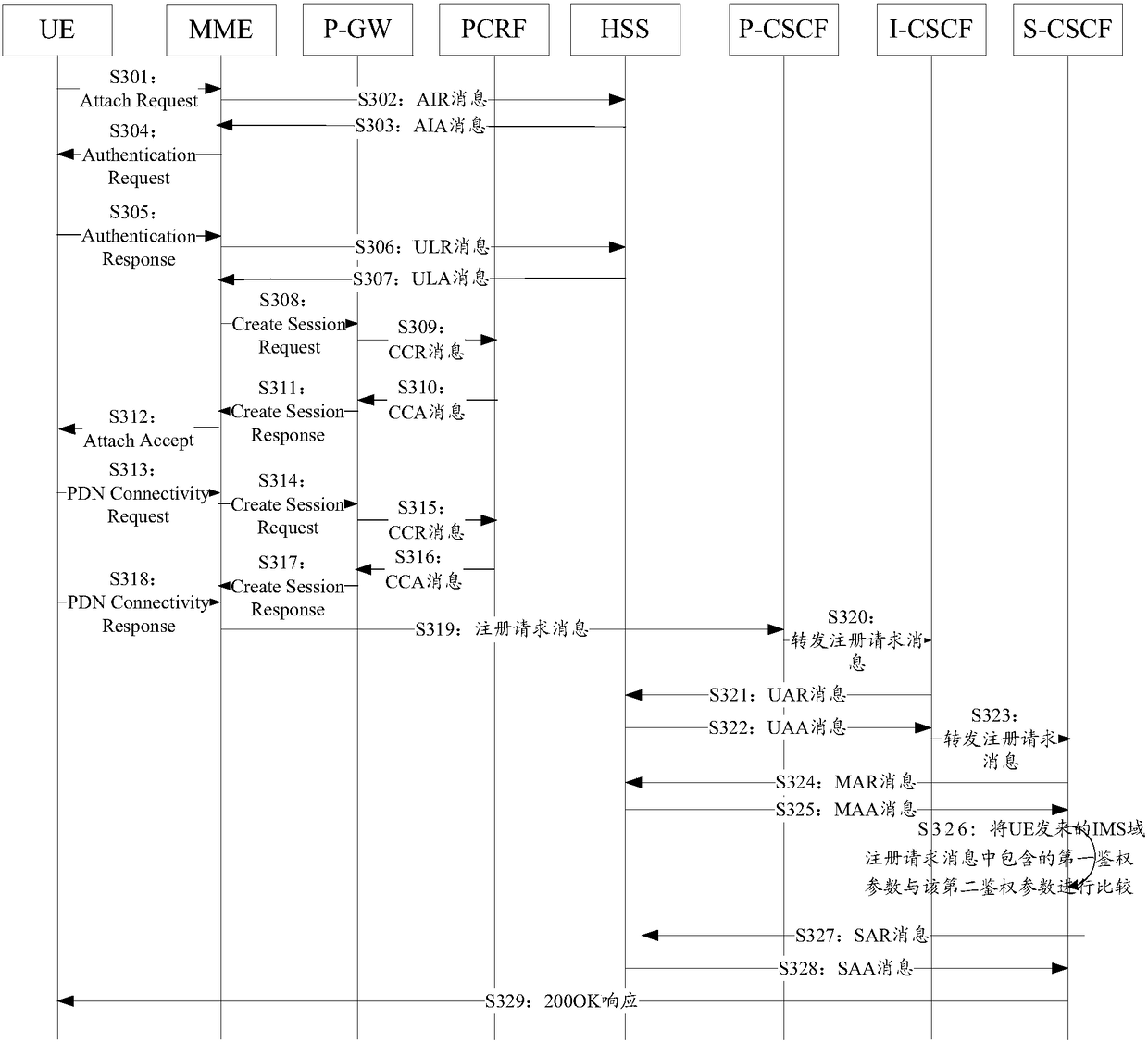
[0065] refer to image 3 , in order to better illustrate the solution proposed by the embodiment of the present application, the process of UE attaching to the EPC network and registering in the IMS network will be described in detail in Embodiment 3 of the present application.
[0066] The process of UE attaching to the EPC network:
[0067] S301: The UE sends an Attach Request (Attach Request) message to a Mobile Management Entity (Mobile Management Entity, MME) through the eNodeB, wherein the Attach Request message carries user identity information, such as an International Mobile Subscriber Identification Number (International Mobile Subscriber Identification Number , IMSI), etc., and the user's ability to access the core network, attachment type and other information.
[0068] S302: If the MME does not have an authentication set locally, the MME sends an Authentication Information Request (AIR) message to a Home Subscriber Server (HSS) to request authentication data.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com