A processing method and device for cc attack
A processing method and attack-end technology, applied in the field of human network communication, which can solve the problems of authentication mechanism collapse and leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
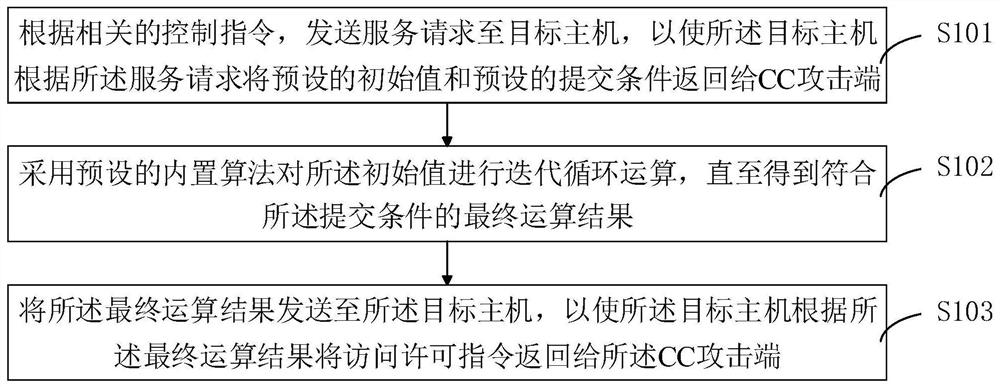
[0043] see figure 1 , figure 1 It is a schematic flowchart of a CC attack processing method provided by the first embodiment of the present invention.
[0044] A processing method for CC attack, comprising the steps of:
[0045] S101. Send a service request to the target host according to a related control instruction, so that the target host returns a preset initial value and a preset submission condition to the CC attack end according to the service request.
[0046] Wherein, the initial value is an initial condition that triggers the CC attack end to use a preset built-in algorithm to perform an iterative cycle operation on the initial value; the submission condition is set according to the initial value to verify each iteration The condition for looping over the results of an operation.
[0047] In this embodiment, the submission condition may be a unified static submission condition preset by the client, or a dynamic matching condition transmitted to the user client al...
no. 2 example
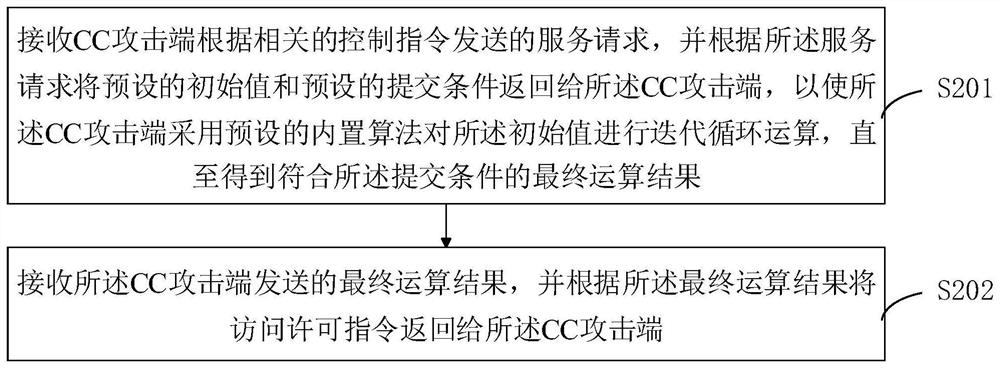
[0059] see figure 2 , figure 2 It is a schematic flowchart of a CC attack processing method provided by the second embodiment of the present invention.
[0060] A processing method for CC attack, comprising the steps of:
[0061] S201. Receive the service request sent by the CC attack end according to the relevant control instruction, and return the preset initial value and the preset submission condition to the CC attack end according to the service request, so that the CC attack end uses The preset built-in algorithm performs an iterative cycle operation on the initial value until a final operation result meeting the submission condition is obtained.
[0062] Wherein, the initial value is an initial condition that triggers the CC attack end to use a preset built-in algorithm to perform an iterative cycle operation on the initial value; the submission condition is set according to the initial value to verify each iteration The condition for looping over the results of an...
no. 3 example
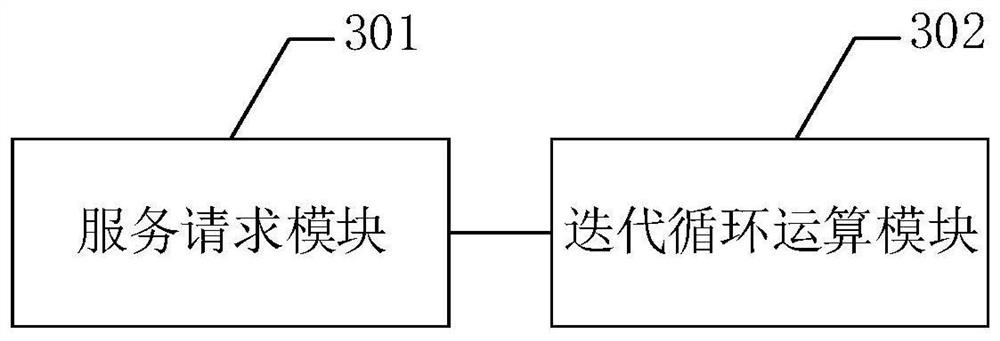
[0074] see image 3 , image 3 It is a schematic structural diagram of a CC attack processing device diagram provided by the third embodiment of the present invention.
[0075] A CC attack processing device, comprising:
[0076] The service request module 301 is configured to send a service request to the target host according to related control instructions, so that the target host returns preset initial values and preset submission conditions to the CC attack end according to the service request.
[0077] Wherein, the initial value is an initial condition that triggers the CC attack end to use a preset built-in algorithm to perform an iterative cycle operation on the initial value; the submission condition is set according to the initial value to verify each iteration The condition for looping over the results of an operation.
[0078] In this embodiment, the submission condition may be a unified static submission condition preset by the client, or a dynamic matching co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com