Operation code frequency-based malicious code visual analysis method
A technology of malicious code and analysis methods, applied in the direction of instrument, platform integrity maintenance, character and pattern recognition, etc., can solve problems such as lack of universality, dissimilar visual perception of image matrix, etc., to reduce time overhead and reduce computing overhead , the effect of reducing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
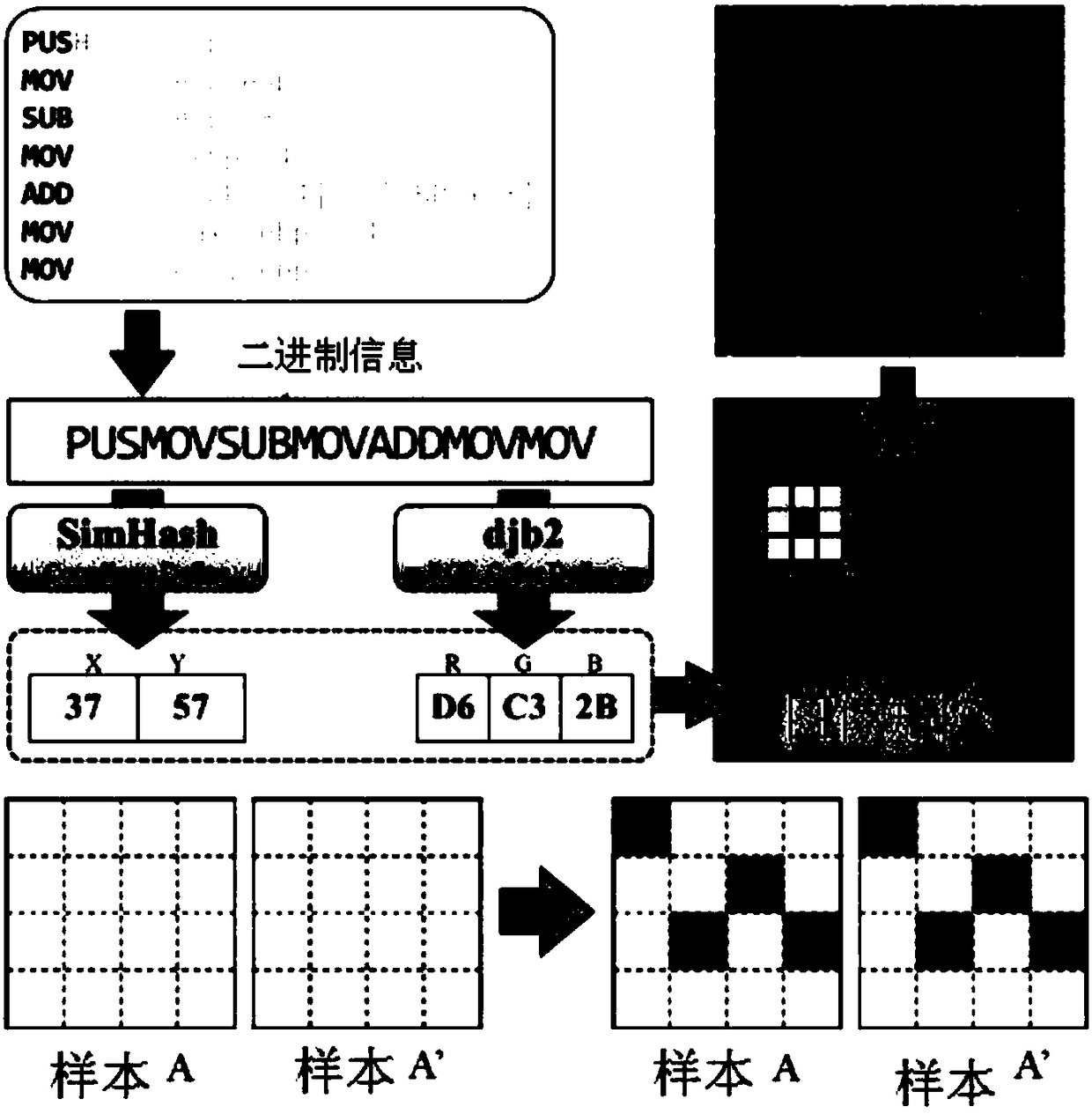
[0032] A method for visual analysis of malicious code based on opcode frequency, specifically:
[0033] Step 1: Extract the opcode character sequence (PUSH-MOV-JMP-PUSH-INC-XOR-POP-INC-XOR-MOVZX) of the malicious code (type 5 sample Fnda3PuqJT6Ep5vjOWCk), and convert each opcode character according to the corresponding relationship D Into a constant sequence (198-178-153-198-138-253-193-138-253-183...);
[0034] Let the conversion relationship between each opcode character and constant be D:
[0035]('AAA',0),('AAD',1),('AAM',2),('AAS',3),('ADC',4),('ADD',5),(' AND',6),('ARPL',7),('BOUND',8),('BSF',9),('BSR',10),('BSWAP',11),('BT' ,12),('BTC',13),('BTR',14),('BTS',15),('CALL',16),('CBW',17),('CDQ',18 ),('CLC',19),('CLD',20),('CLI',21),('CLTS',22),('CMC',23),('CMOVcc',24), ('CMP',25),('CMPSB',26),('CMPSD',27),('CMPSW',28),('CMPXCHG',29),('CMPXCHG8B',30),(' CPUID',31),('CS',32),('CWD',33),('CWDE',34),('DAA',35),('DAS',36),('DEC' ,37),('DIV',38),('DS',39),('ENTER',40),('ES'...
Embodiment 2
[0041] Adopt the malicious code visual analysis method based on the operation code frequency described in embodiment 1, generate the image of the 2nd type sample 7VE6hScuodxAvTp0Nrnk, 8026Dh4VpfjPekaCgAYQ, DIrEPtygG8SeLJ5mvq2a, as Figure 3-5 As shown, the present invention can obviously find subtle differences among malicious samples of the same family when analyzing malicious samples of the same family, which provides a basis for understanding the evolution of the variant of the family and grasping the development trend of the variant of the family.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com