An encrypted tunnel communication method based on hip protocol
A communication method and protocol technology, which is applied in the field of network communication security, can solve the problems of being unable to integrate, unable to use the excellent characteristics of host identification HIP, and unable to realize self-reform, etc., and achieve the effect of wide application range and high degree of security and confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
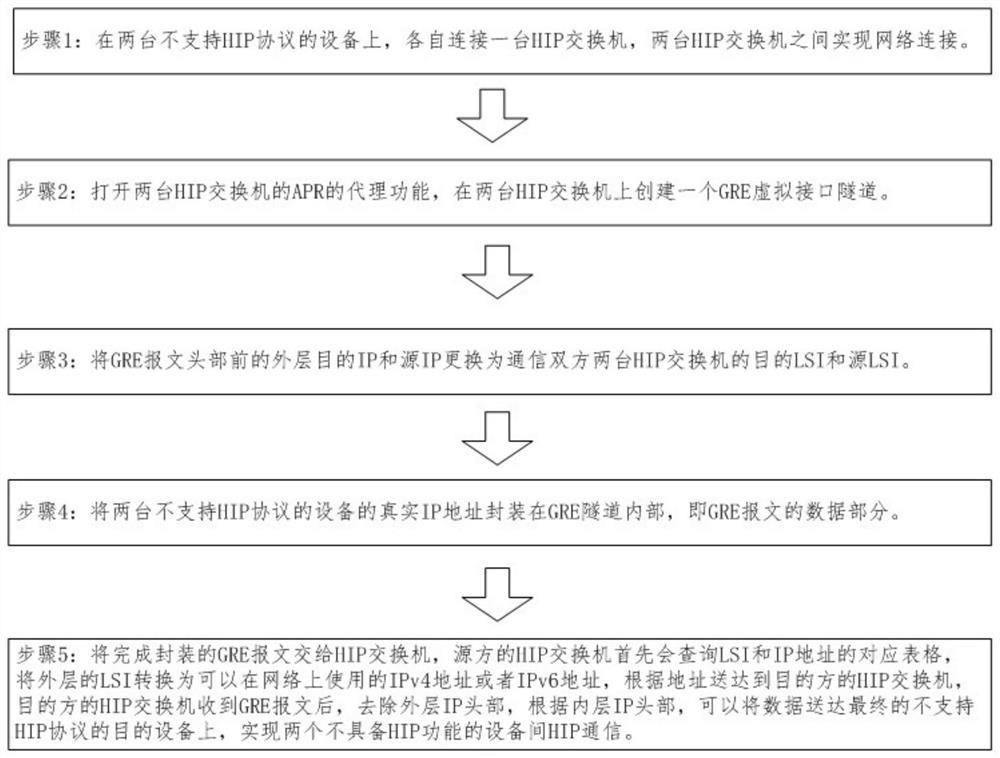
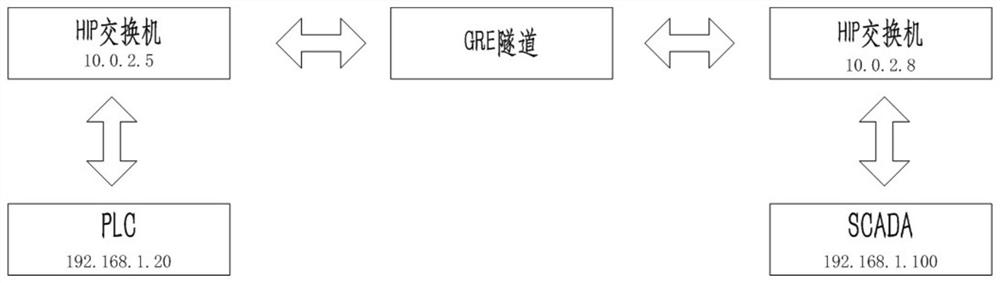
[0036] Such as figure 2 Shown: Two devices that do not support the host identification HIP protocol: programmable logic controller PLC (192.168.1.20) and data acquisition and monitoring control system SCADA (192.168.1.100); programmable logic controller PLC (192.168.1.20) Connect a host identification HIP switch (10.0.2.5), data acquisition and monitoring control system SCADA (192.168.1.100) connect a host identification HIP switch (10.0.2.8); open the address resolution APR of the two host identification HIP switches Proxy function, creating a general routing encapsulation protocol GRE virtual interface tunnel on two host identification HIP switches;
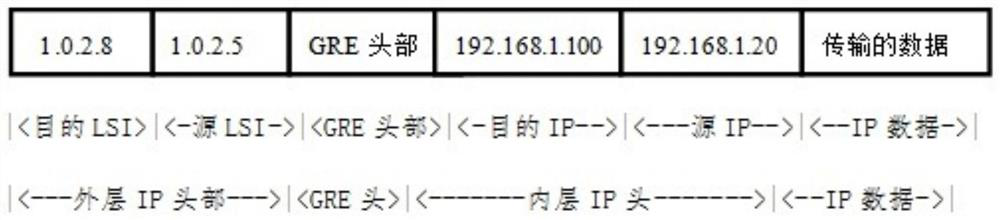
[0037] Such as image 3 Shown: Replace the outer layer destination IP and source IP before the general routing encapsulation protocol GRE message header with the destination local identifier LSI (1.0.2.8) and the source local identifier LSI ( 1.0.2.5); encapsulate the real IP address of the device programmable logic controll...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com