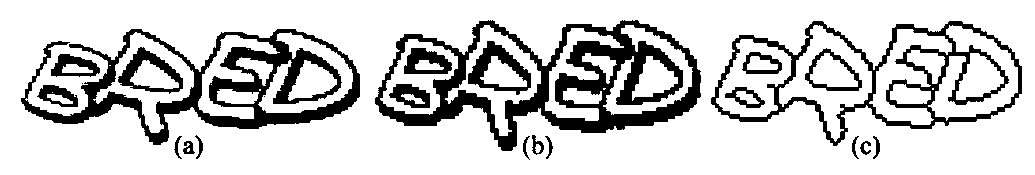Hollow verification code quick identification method
An identification method and verification code technology, applied in the field of verification code identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
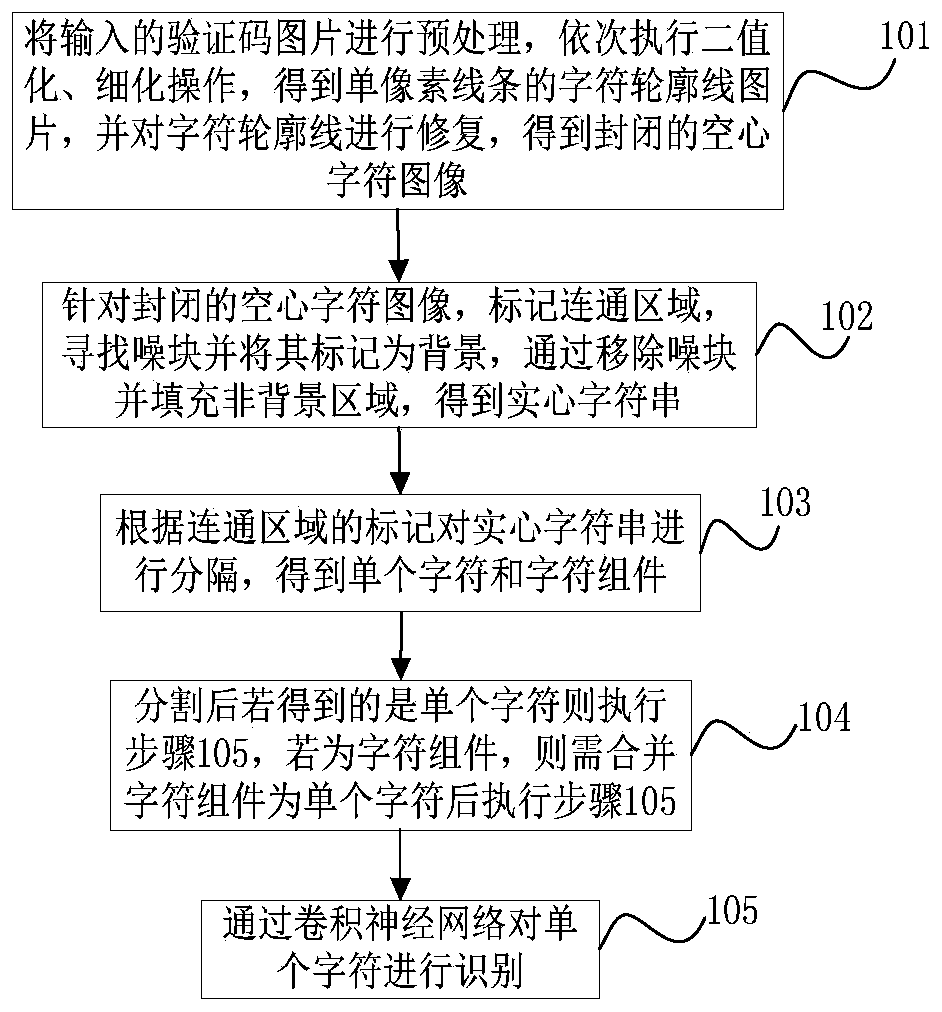
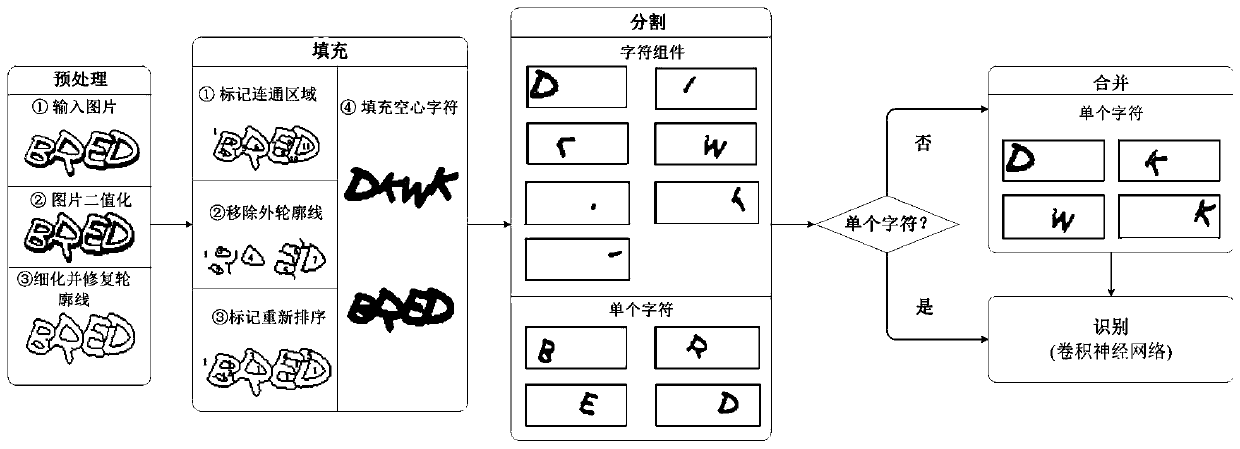
[0043] Embodiment two, see figure 2 As shown, a fast recognition method for hollow captcha consists of five stages: preprocessing, filling, segmentation, merging and recognition:
[0044] Preprocessing: convert the verification code image into a binary image, and then refine and repair the character outline.
[0045] Filling: First, mark all connected regions; then, use the inner and outer contour algorithm to find the noise block; next, mark the noise block as the background; finally, fill the non-background area to get a solid string.
[0046]Segmentation: Using the different connected region labels obtained in the filling stage, the solid string is segmented into most single characters and few character components.
[0047] Merging: The character components obtained in the segmentation stage are merged into a single character using the least nearest neighbor algorithm.
[0048] Recognition: Use Convolutional Neural Networks for Recognition.
[0049] The following five s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com