Network attack defense method, device and system
A network attack and service system technology, which is applied in the field of network attack defense methods, devices and systems, can solve the problems of high complexity and poor flexibility in defense against DDoS, and achieve the effects of flexible modification or setting, reduced complexity, and reduced frequency access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
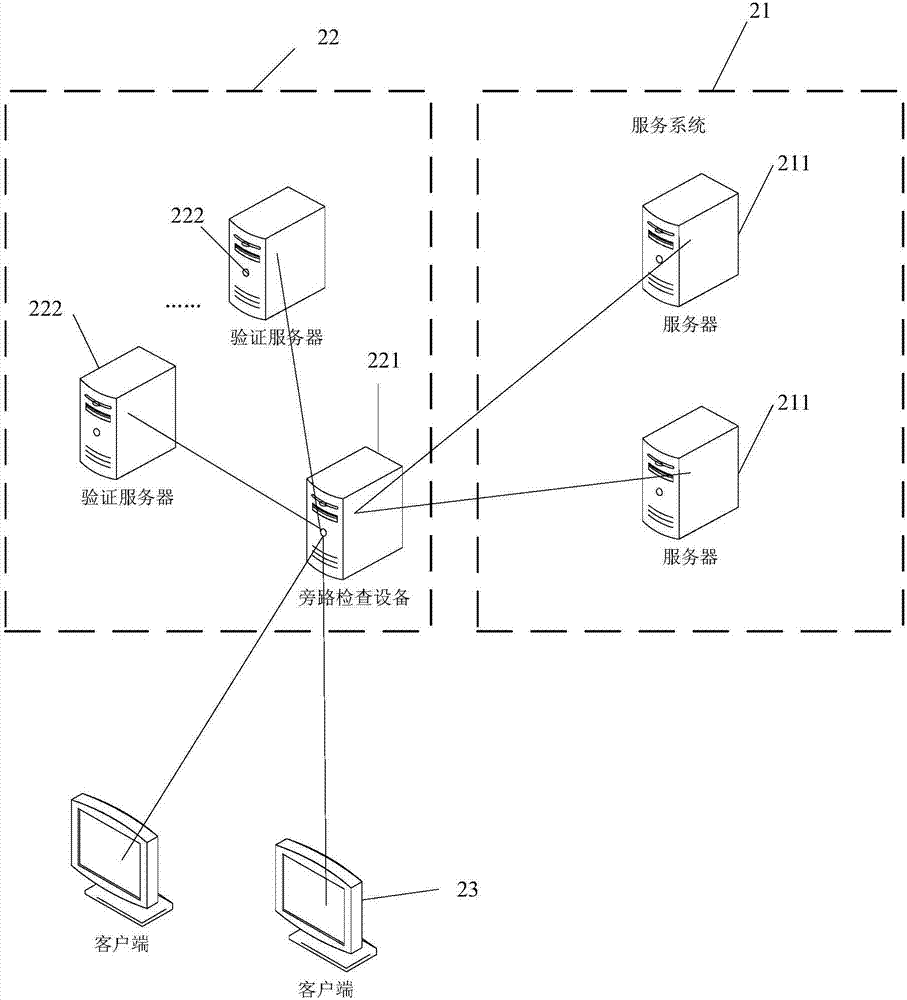
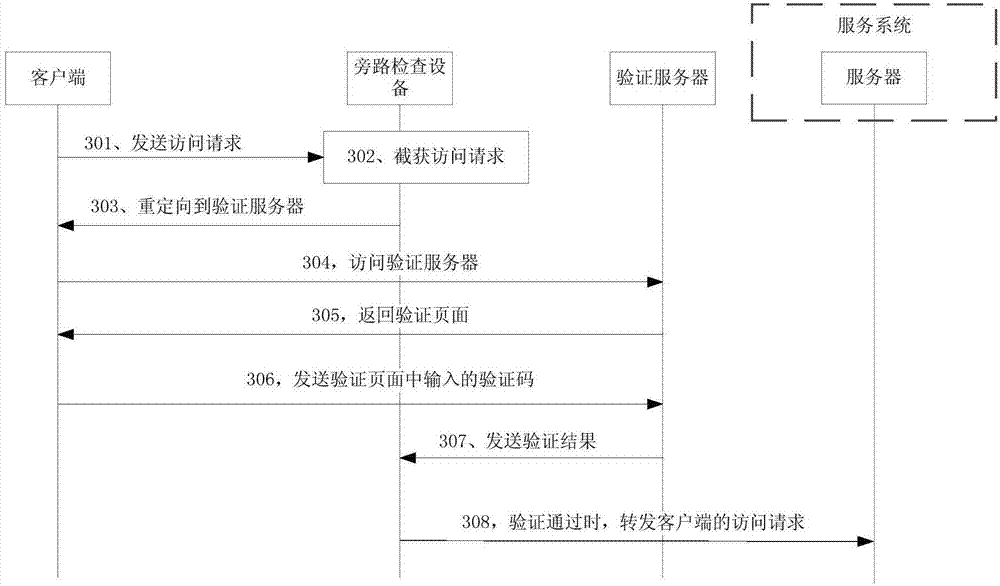
[0030] The solutions of the embodiments of the present application can be applied to attacking and defending servers in any service system, so as to reduce malicious access to servers in the service system such as DDoS attacks. Wherein, the service system may include one or more servers. For example, the service system may be a cloud platform that includes multiple servers. In this way, the solution of the embodiment of the present application may perform network attack defense on one or more servers in the cloud platform. As another example, the service system may be a server cluster that provides certain service services, and the server cluster may include multiple servers. In this way, the solution of the embodiment of the present application may carry out network attacks on one or more servers in the server cluster defense.
[0031] In the embodiment of the present application, the mentioned client may be a client accessing the service system, for example, the client may ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com