APUF security authentication method based on polynomial reconstruction
A technology of polynomial reconstruction and security authentication, which is applied to secure communication devices and key distribution, can solve the problems of unsatisfactory PUF reliable implementation, PUF reliability decline, resource consumption increase, etc., to achieve resistance to machine learning attacks and high reliability And safety, the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Embodiments of the invention are described in detail below, examples of which are illustrated in the accompanying drawings. The embodiments described below by referring to the figures are exemplary only for explaining the present invention and should not be construed as limiting the present invention.
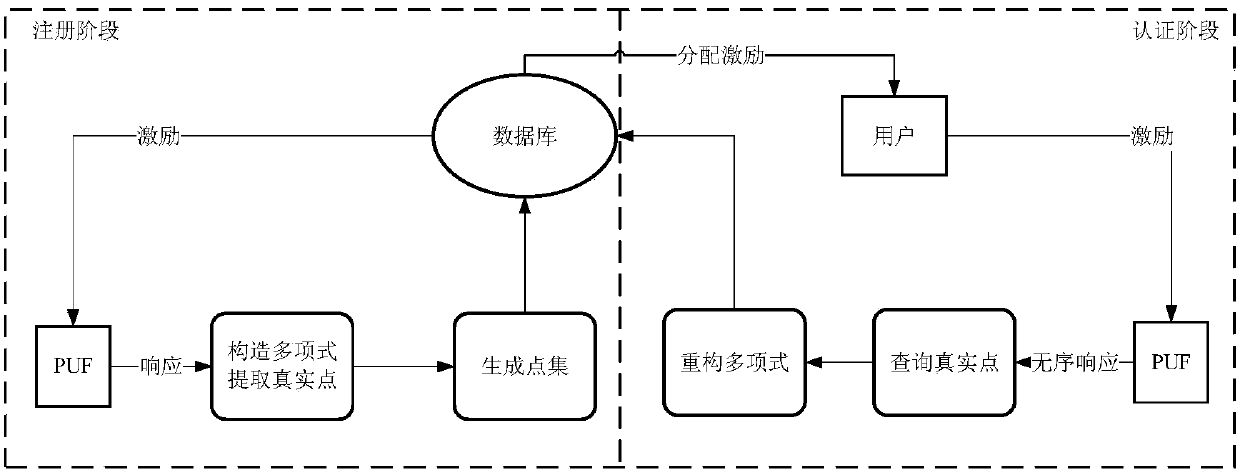
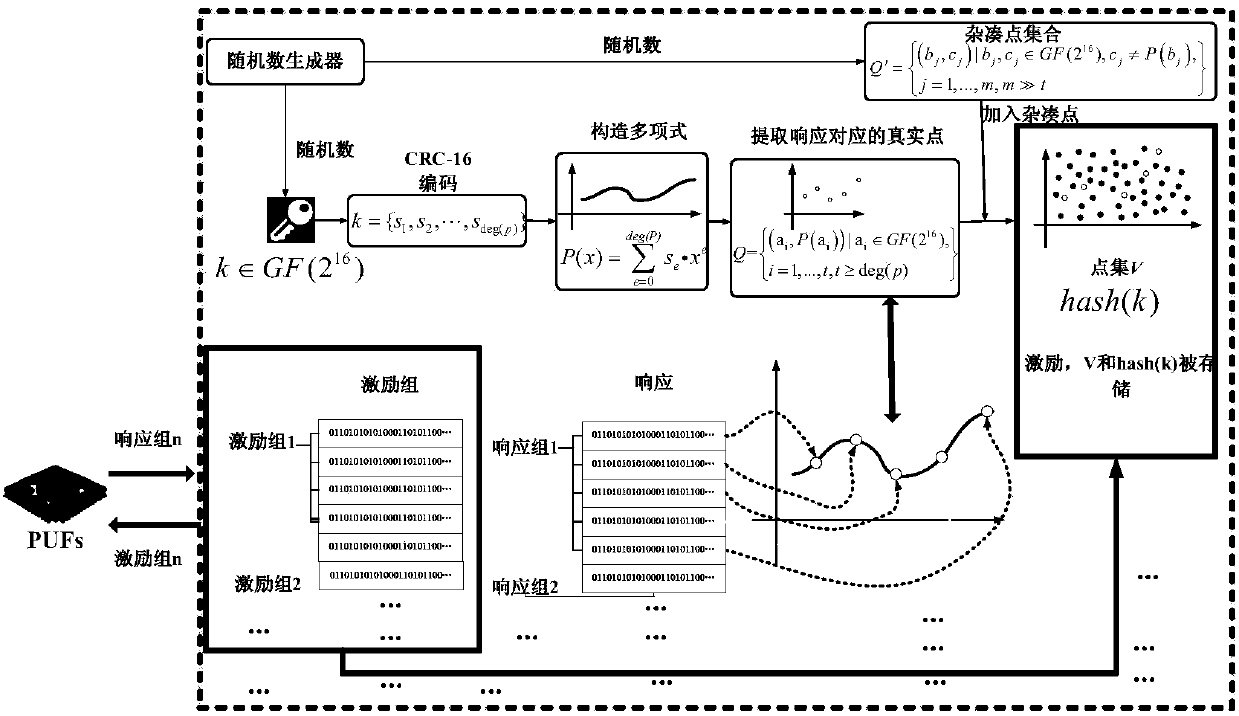
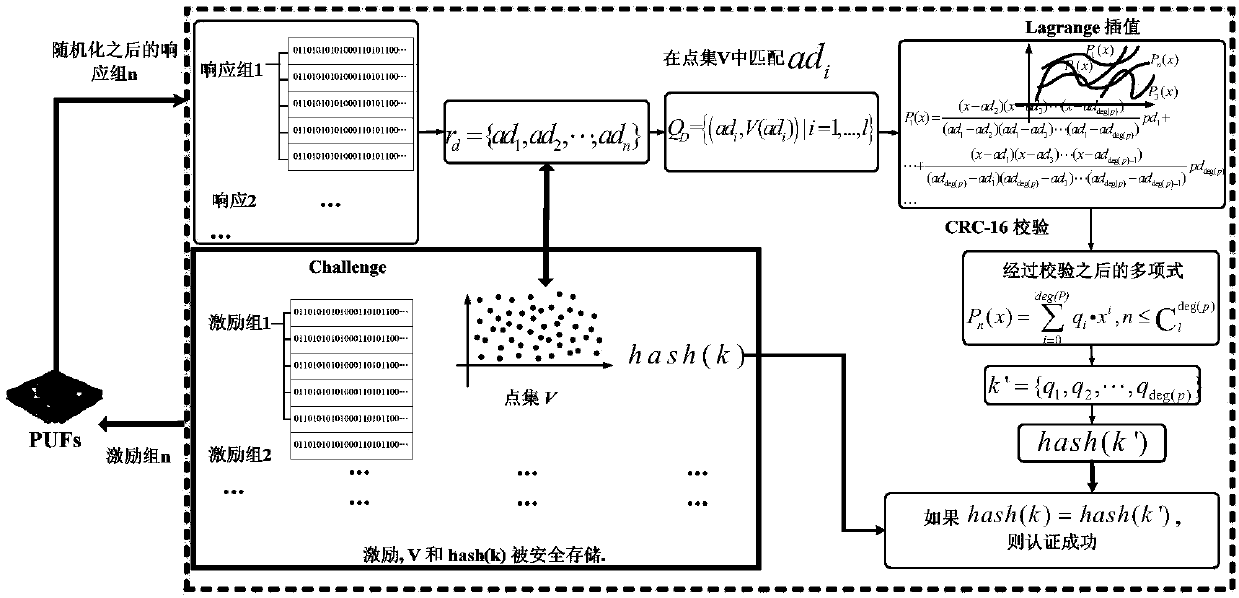
[0040] Such as figure 1As shown, an APUF security authentication method based on polynomial reconstruction is realized by the APUF security authentication system, and the whole system generally includes APUF modules and polynomial building blocks. The server randomly generates a large number of incentives, and at the same time generates a random number. Stimuli are used in the APUF module to generate the corresponding stimuli used as abscissas. Random numbers are used for polynomial coefficients after CRC-16 checking. Using the excitation as the abscissa, find all the real points in the polynomial, and add a large number of hash points to form a point set. Store the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com