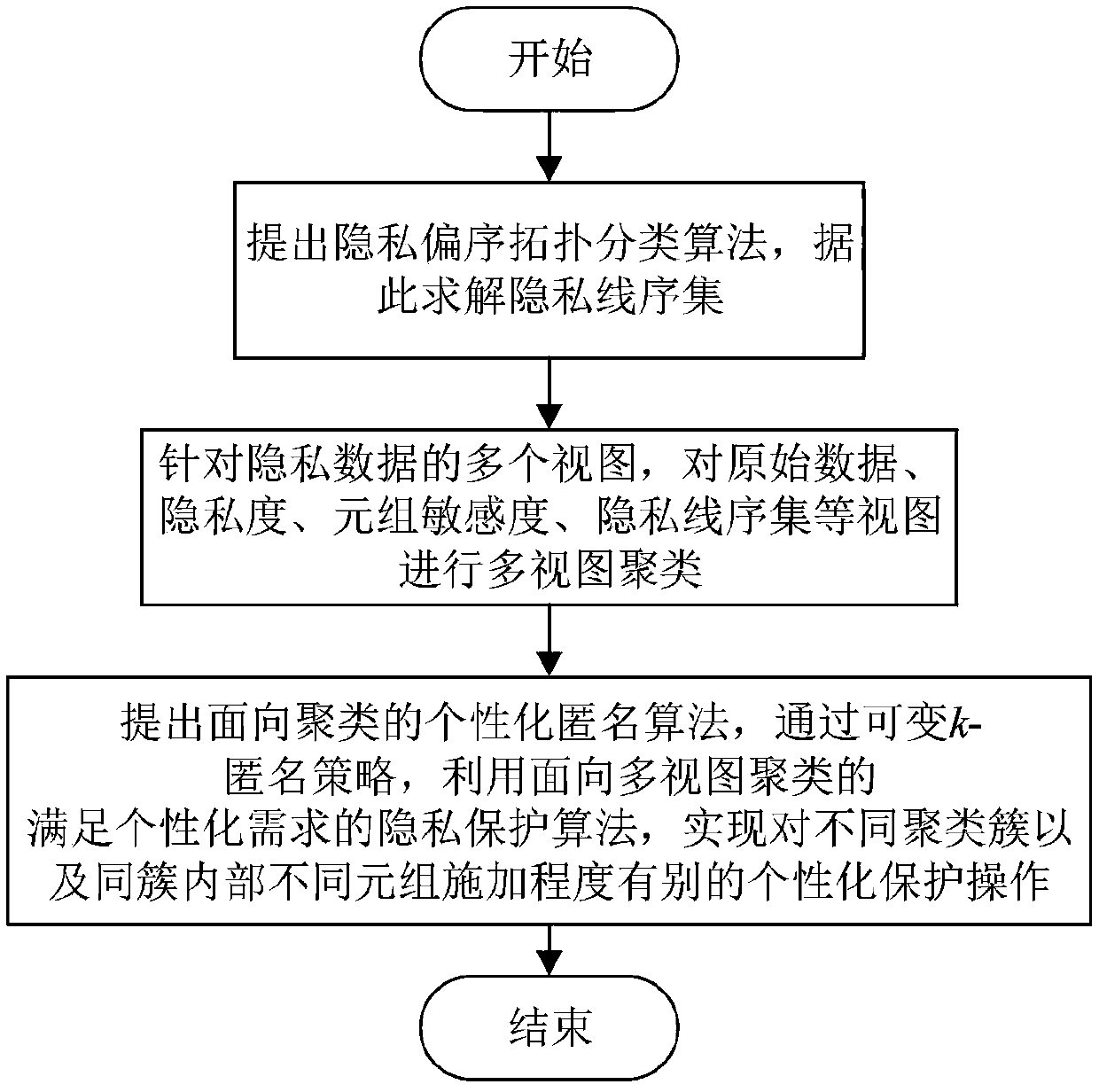
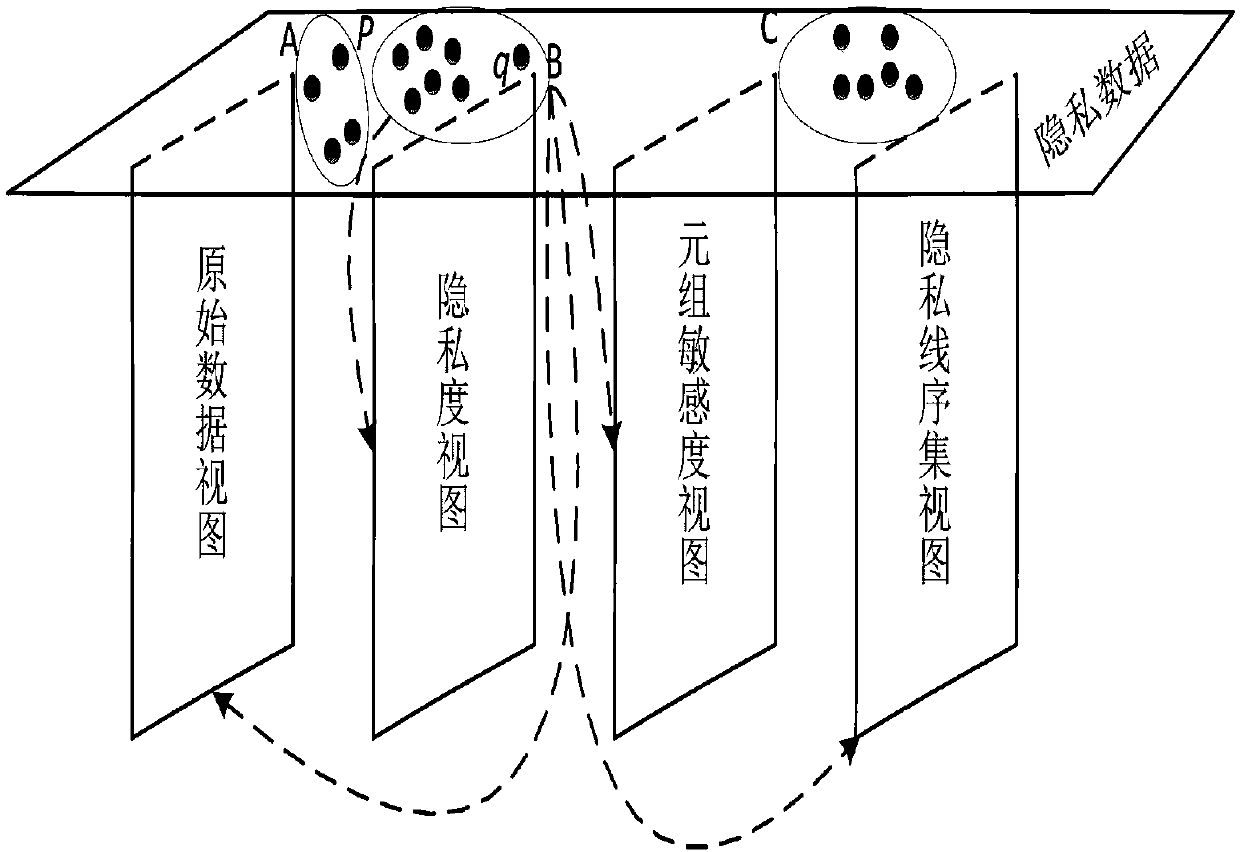
Multi-view clustering and mining oriented personal privacy protection method
A cluster mining and privacy protection technology, applied in the field of information security, can solve problems such as the need to improve the degree of personalization, large information loss, and privacy security issues that have not been involved in cluster mining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] For the original data model A=(A 1 ,A 2 ,...,A n ) under a piece of data is expressed as d=(a 1 ,a 2 ,...,a n ), where a i is the attribute of the data, if i exists, (i=1,2,...,n) makes a i If it is sensitive and does not want others to know, then this record d is called a piece of private data, and the quantitative expression of the sensitivity of the data producer to the private data item is called the degree of privacy. Given the original data pattern A=(A 1 ,A 2 ,...,A n ), the corresponding privacy mode is S=(S 1 ,S 2 ,...,S n ), then the privacy data model is defined as sequence pair , and a piece of privacy data under this model is expressed as n recombination d=(d 1 , d 2 ,...,d n ), where d i =i ,s i > is an ordered binary group, a i for attribute A i Corresponding to a raw data value, s i for a i corresponding degree of privacy. another note d j =(a j1 ,a j2 ,...,a jn ) is the original data mode A=(A 1 ,A 2 ,...,A n ) of the jth tup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com