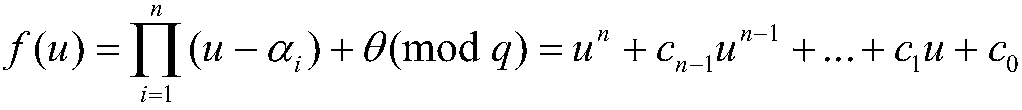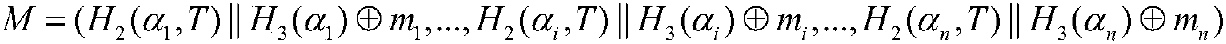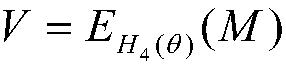Real anonymous certificateless multi-message multi-receiver signcryption method
A multi-receiver, certificate-free technology, applied to public keys for secure communication, user identity/authority verification, key distribution, and can solve problems such as poor practicability
Active Publication Date: 2018-02-09
XIDIAN UNIV
View PDF4 Cites 22 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0003] In order to overcome the shortcomings of poor practicability of the existing certificateless multi-message multi-receiver si
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a real anonymous certificateless multi-message multi-receiver signcryption method, and the method is used for solving a technical problem that a conventional certificateless multi-message multi-receiver signcryption method is poor in practicality. The technical scheme is that the method comprises the steps: enabling a user to select a secret value as a part of a private key, calculating a part of a public key through the secret value, and then enabling a part of the public key and the identity information of the user to be transmitted to a KGC (key generation center); enabling the KGC to generate verification parameters of the corresponding part of the private key and the corresponding part of the public key, and then transmitting the parameters to the user througha safety cahnnel; verifying the validity of the corresponding parts of the private key and public key after the user receives the corresponding parts of the private key and public key: continuing to calculate a public key and a private key of the user if the validity passes the verification and disclosing the public key, or else stopping the operation. The signcryption process does not comprise the identity information of a transmitter and a receiver, and the method achieves the overall encryption of a plurality of different messages to be transmitted. Only an authorized receiver can decrypt aciphertext message, so the method is high in practicality and is high in efficiency.
Description
technical field [0001] The invention relates to a non-certificate multi-message multi-receiver signcryption method, in particular to a truly anonymous non-certificate multi-message multi-receiver signcryption method. Background technique [0002] In the document "Zhou Yanwei, Yang Bo, Zhang Wenzheng. Anonymous certificateless multi-receiver signcryption mechanism. Electronic Journal, 2016, 44(8): 1784-1790." An anonymous certificateless multi-message multi-receiver Signcryption method. This method has the following disadvantages: the ciphertext information of this method does not include the identity information of the recipient, but the attacker can judge whether an identity is a legitimate recipient's identity through the ciphertext parameters and public parameters; the signcryption algorithm is designed in the ellipse On the curve, but the elliptic curve has more number multiplication operations, resulting in low operation efficiency in the encryption process; the anonym...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L9/08H04L9/30H04L9/32
Inventor 庞辽军许婷婷贾生盼魏萌萌李慧贤
Owner XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com