Data processing method, data sending method, and risk identifying method and device
A data processing device and data processing technology, applied in data processing applications, electrical digital data processing, special data processing applications, etc., can solve problems such as the increase in risk identification processing time, so as to avoid the increase in processing time, reduce storage overhead, and solve Effects of Data Transfer Issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
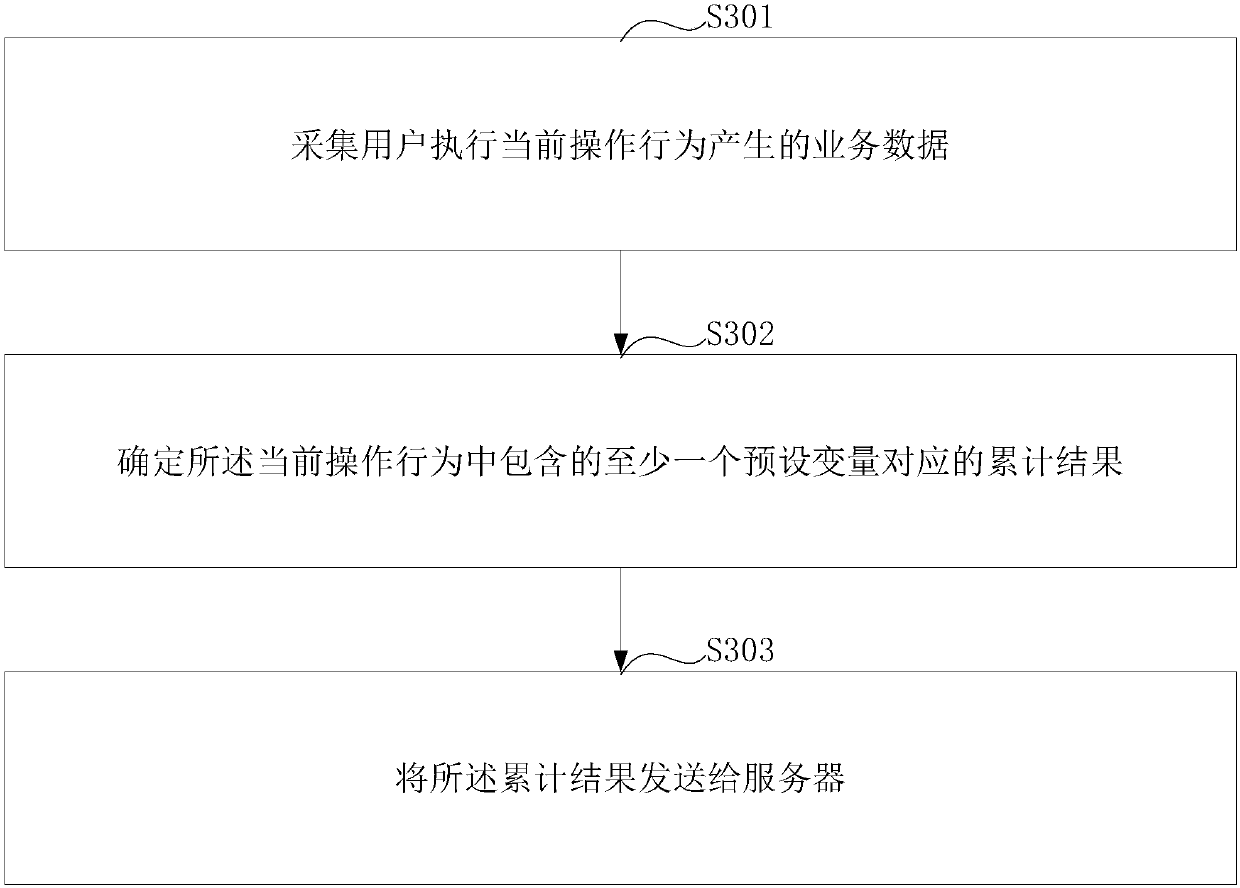
[0054] figure 1 It is a flow chart of a data processing method provided by the embodiment of this application. The execution subject of the data processing method may be a client, and this article introduces the technical solution by taking the client as an execution subject as an example. The data processing method comprises the steps of:
[0055] S101: Collect service data generated by the user performing the current operation behavior.
[0056] Since the user will generate business data when using the client to perform the operation behavior, the data content of the business data generated by different operation behaviors is also different. When business data is generated, it can be stored in the storage unit of the client in real time; the data processing method described in the embodiment of the application can also be started in real time, and the data obtained after processing can be stored in the storage unit; it can also be stored in the client. The business data i...
Embodiment 2
[0126] At present, there is still such an existing technology: the client collects the business data generated by the user in the process of using the client, and transmits the collected business data to the server. The business data is calculated to obtain the value of a certain variable, and the calculated value of the variable is used as the input of the risk identification model for risk identification. In the above prior art, since the user's business data is generated along with the user's operation behavior on the client, generally the amount of business data collected by the client will continue to increase. Therefore, sending a large amount of business data collected by the client to the server will inevitably cause a large consumption of network transmission resources. Aiming at the above problems, the present application also proposes a data sending method to solve the problem in the prior art that a large amount of business data collected by the client is transmitt...
Embodiment 3
[0140] Based on the same inventive concept, the accumulated results of the above preset variables can be applied to the scenario of risk identification. Figure 4 It is a schematic flowchart of a risk identification method provided in the embodiment of this application. The execution subject of this embodiment of the application is a server. The risk identification method includes the following steps:
[0141] S401: Receive the cumulative result sent by the terminal device.
[0142] The cumulative result is at least one preset variable object included in the current operation behavior performed by the user on the terminal device, and is obtained through the data processing method described in Embodiment 1.
[0143] As mentioned above, the preset variable can be, for example: the decay time (decay sum) of the user's browsing behavior on the same page, or the decay count of the user's browsing behavior on the same page (decay count), or the user's browsing behavior on the same...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com