Baseline construction and unknown abnormal behavior detection method oriented to system log
A technology of system log and detection method, applied in transmission systems, electrical components, etc., can solve the problem of weak robustness of abnormal points, and achieve the effect of avoiding the effect of abnormal points
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The method of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments of the present invention.
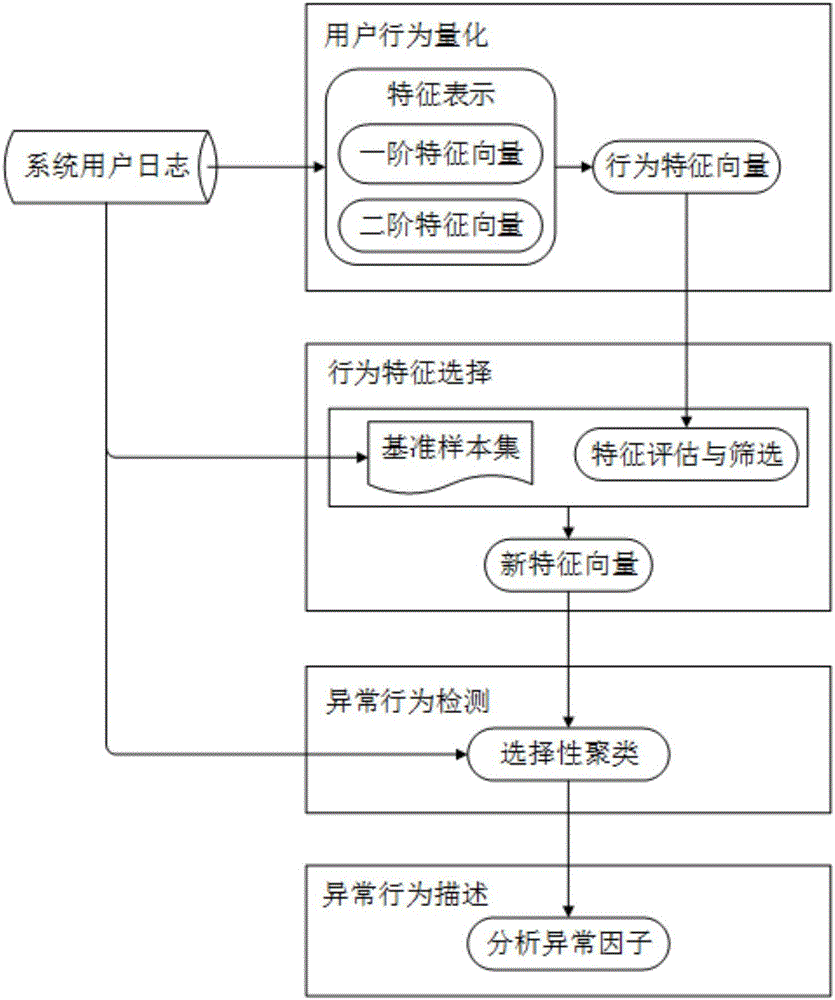
[0021] Such as figure 1 As shown, the present invention is a system log-oriented baseline construction and unknown abnormal behavior detection method, the specific implementation steps are as follows:
[0022] Step 1: Quantification of user operation logs
[0023] Abnormal behavior detection is mainly for information systems (such as 4A systems) or user operation logs of various devices. Operation types are defined and authorized by the system. User operation logs usually include elements such as user name, time, client IP, operation object, and operation result. In order to discover user behavior characteristics from logs and detect anomalies, it is necessary to quantify user behavior samples in logs into feature vectors. The user's behavior feature vector is mainly considered as the following first-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com