Switch port security protection method and apparatus based on TCP/IP
A technology of IP protocol and port security, which is applied in the field of communication, can solve problems such as excessively increasing manpower input costs, and achieve the effect of saving manpower costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
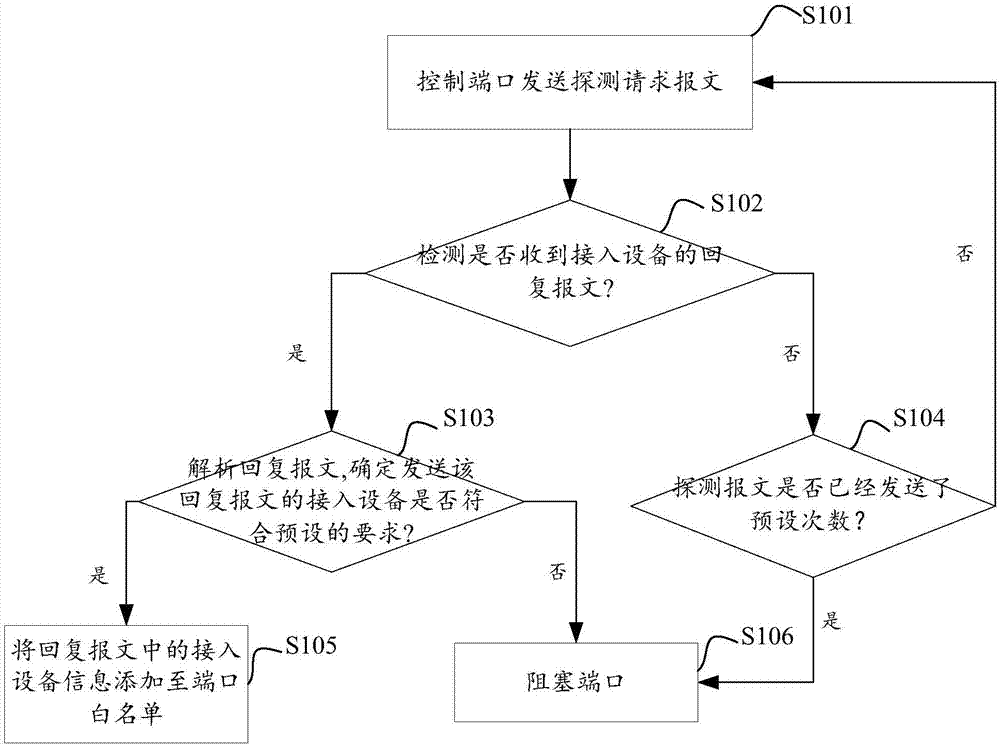
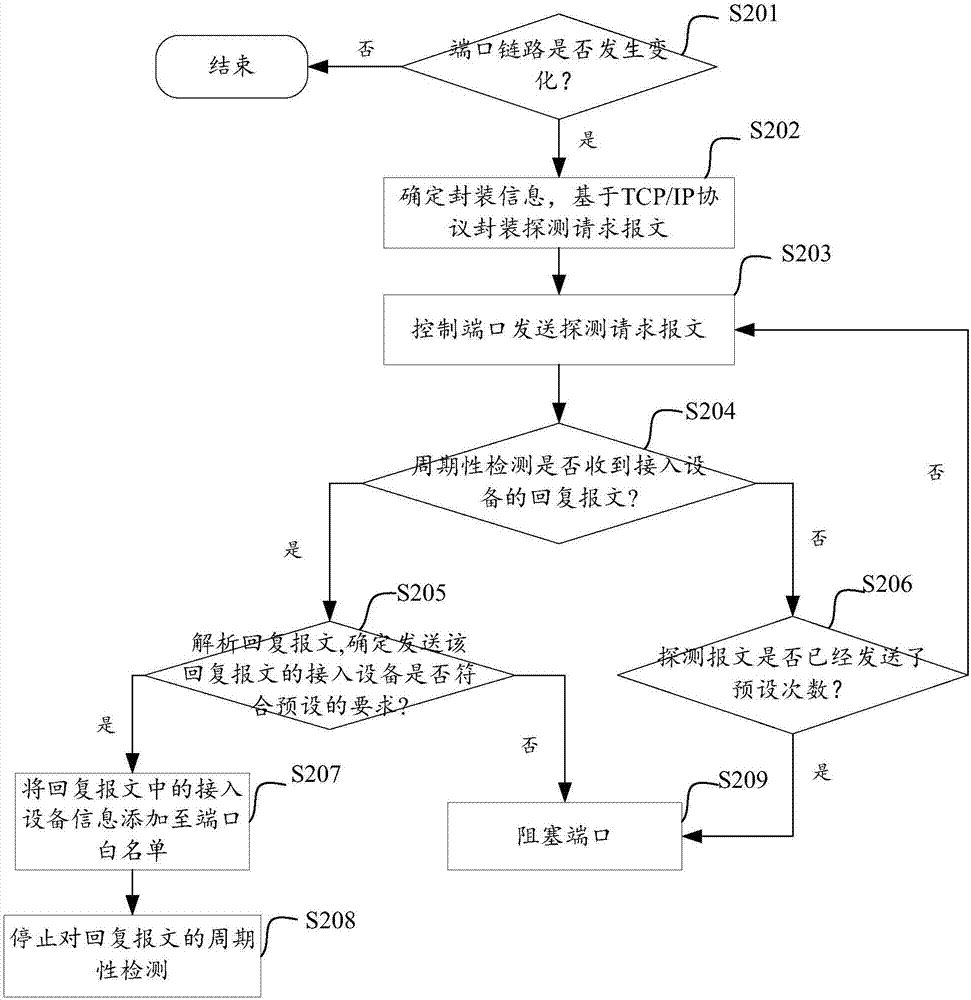
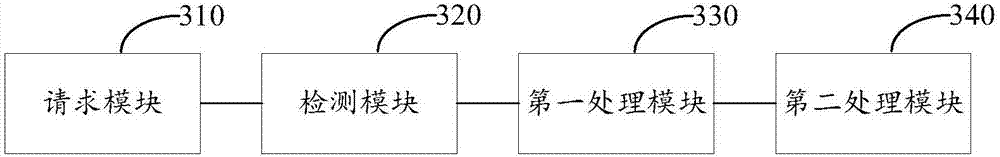
[0025] A switch is an important data-carrying tool in network applications. Users usually do not want strange devices to access the switch. The access of strange devices may affect the normal data transmission and reception, and even affect information security. For example, the user hopes that the access device of a certain switch is limited to traffic cameras in this area, so as to provide network data transmission services for traffic images in real time. If other devices are randomly connected to this switch, it will affect the normal transmission of video data and affect the security of traffic information.
[0026] One of the ways to protect the security of the switch is to identify and process the access device on the physical port of the switch. The existing technology sets an access control list for the port, which can also be called a white list. Add the MAC addresses of the devices that are allowed to connect to the switch to the white list. Normal data transfer. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com