Method and system for controlling requests for sensitive data
A technology for sensitive data and data, applied in the field of network security, it can solve the problems of not being able to prompt users for private data, and application functions cannot be completed, so as to achieve the effect of protecting privacy from being leaked.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the following embodiments specifically illustrate the method and system for controlling sensitive data requests of the present invention in conjunction with the accompanying drawings.
[0022] In this embodiment, the smart device 10 is a mobile phone. Of course, smart devices such as iPads and computers can also be used.
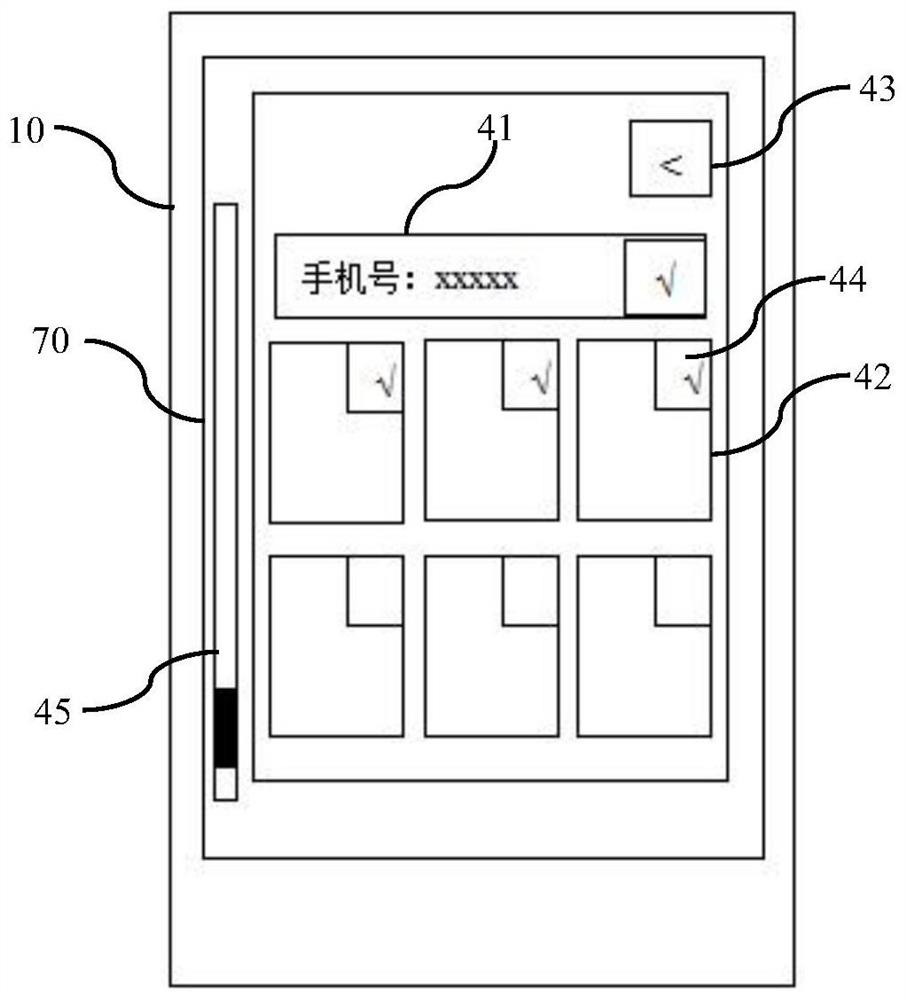
[0023] The method for controlling sensitive data requests includes: when an application program obtains sensitive data in the mobile phone 10, such as figure 1 As shown, an operation interface 30 appears on the display interface 20 of the application program, and the operation interface 30 displays sensitive data acquired by the application program. Sensitive data includes: image data, video data, audio data, user privacy data and device privacy data in text form. Among them, user privacy data refers to specific data bound...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com