A method and system for obtaining device usage authority based on the Internet of Things
A technology of permission acquisition and Internet of Things, applied in transmission systems, electrical components, etc., can solve problems such as the inability to protect the owner's private information and the inability to guarantee the security of transferred information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
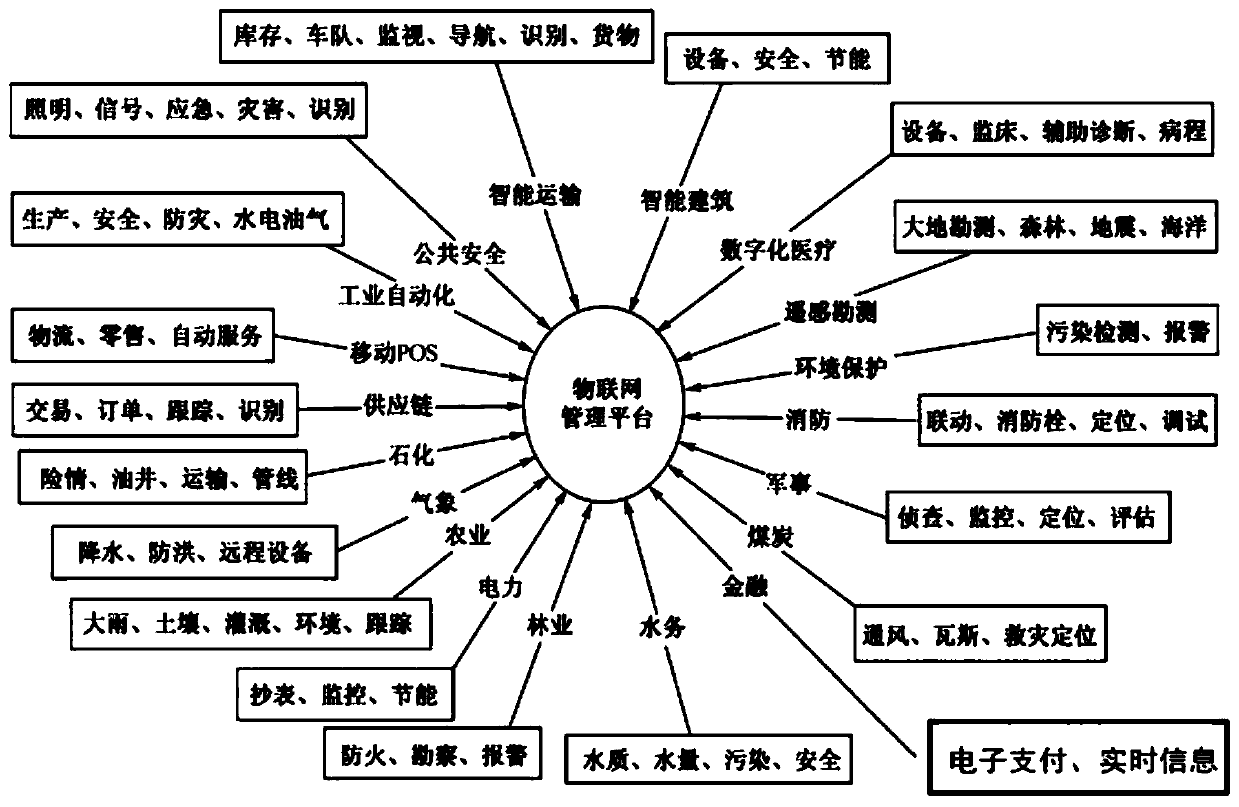
[0055] figure 1 A schematic diagram showing the distribution of various devices in the Internet of Things system in the prior art, such as figure 1 As a management platform, the Internet of Things shown in can be applied in many aspects such as intelligent transportation, construction, medical care, environmental protection, public safety, mobile POS, supply chain, agriculture, forestry, water affairs, and finance. In terms of public security, the Internet of Things can uniformly receive security information transmitted by all parties through the management platform, and connect various security equipment to the Internet of Things management system through the Internet. The networked management system dispatches nearby related equipment to deal with potential safety hazards.
[0056] When applied to various public resources in the city, each user in the city can use the equipment he owns as a public resource for everyone to use, so as to save resources and maximize the use of...
Embodiment 2
[0090] Figure 5 It shows a flow chart of a method for obtaining device usage authority based on the Internet of Things provided by the second embodiment of the present invention; Figure 5 As shown, the method for obtaining device usage authority based on the Internet of Things includes:
[0091] Step S51, receiving the authentication information sent by the server, the owner information and the equipment information in normal state;
[0092] In this step, the server first checks and judges the agent, and when the agent meets the preset conditions, it is determined to be a legal agent; only the legal agent has the agency authority, and sends the authentication information to the legal agent end. The server counts various devices under normal use in the Internet of Things system within a certain range, as well as the owner information of the devices, and integrates these information and sends them to the agent with agency authority. The authentication information includes: ...
Embodiment 3
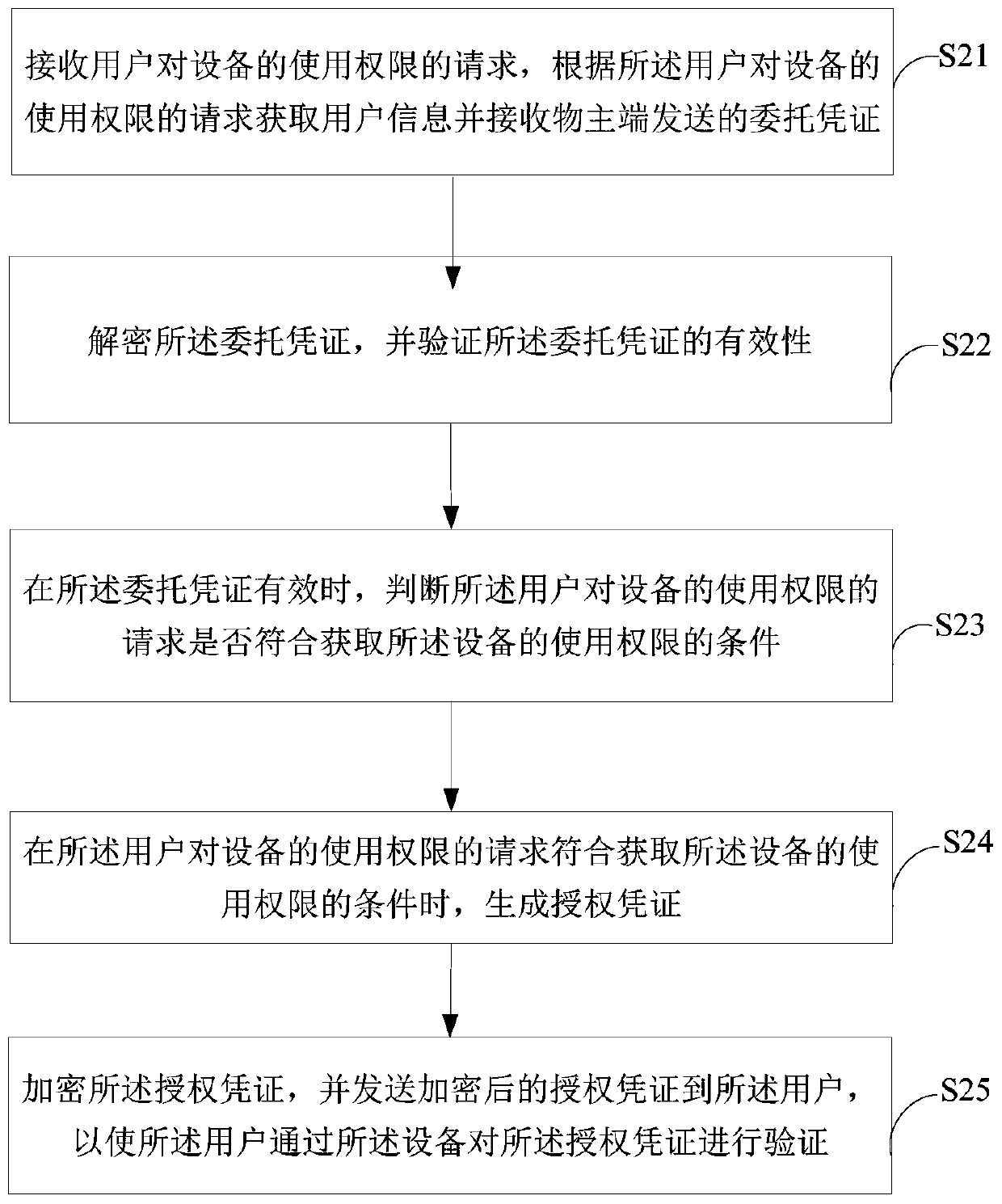
[0102] Image 6 It shows a flow chart of a method for obtaining device usage authority based on the Internet of Things provided by the third embodiment of the present invention; Image 6 As shown, the method for obtaining device usage authority based on the Internet of Things includes:
[0103] Step S61, receiving the authentication information sent by the server, the owner information and the equipment information in normal state;
[0104] Step S62, receiving the user's request for the use right of the device, obtaining user information according to the user's request for the use right of the device, and receiving the entrustment certificate sent by the owner;
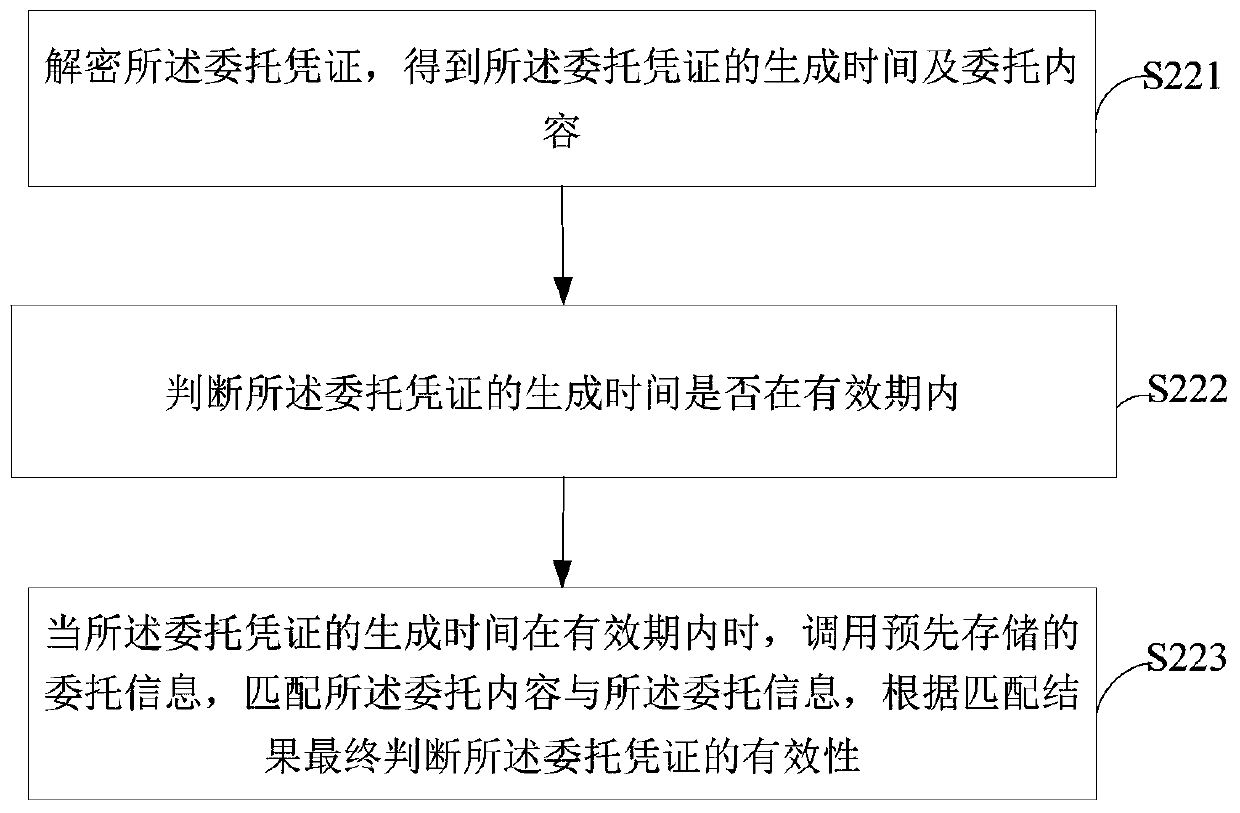
[0105] Step S63, decrypting the entrusted certificate, and verifying the validity of the entrusted certificate;
[0106] Step S64, when the entrustment credential is valid, determine whether the user's request for the device use right meets the conditions for obtaining the device use right;
[0107] Step S65, when ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com