Threat traceability method and device for malicious software
A malicious software and event technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of active defense that cannot trace threats and consume network resources, and achieve the effects of avoiding secondary attacks, reducing network resources, and high processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
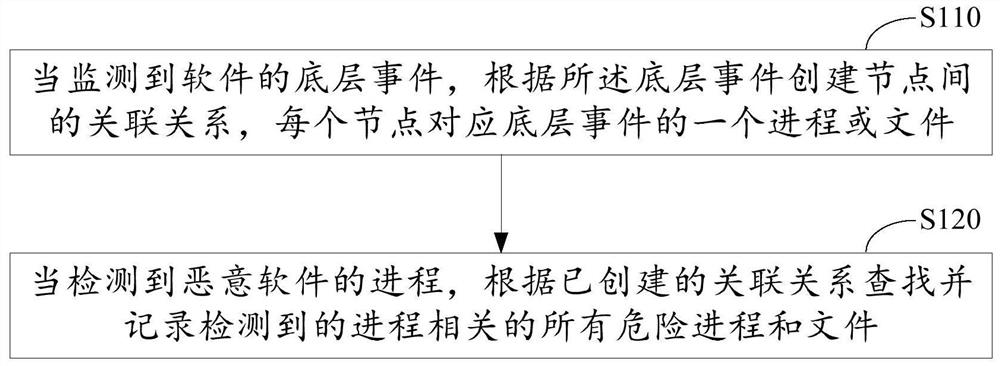
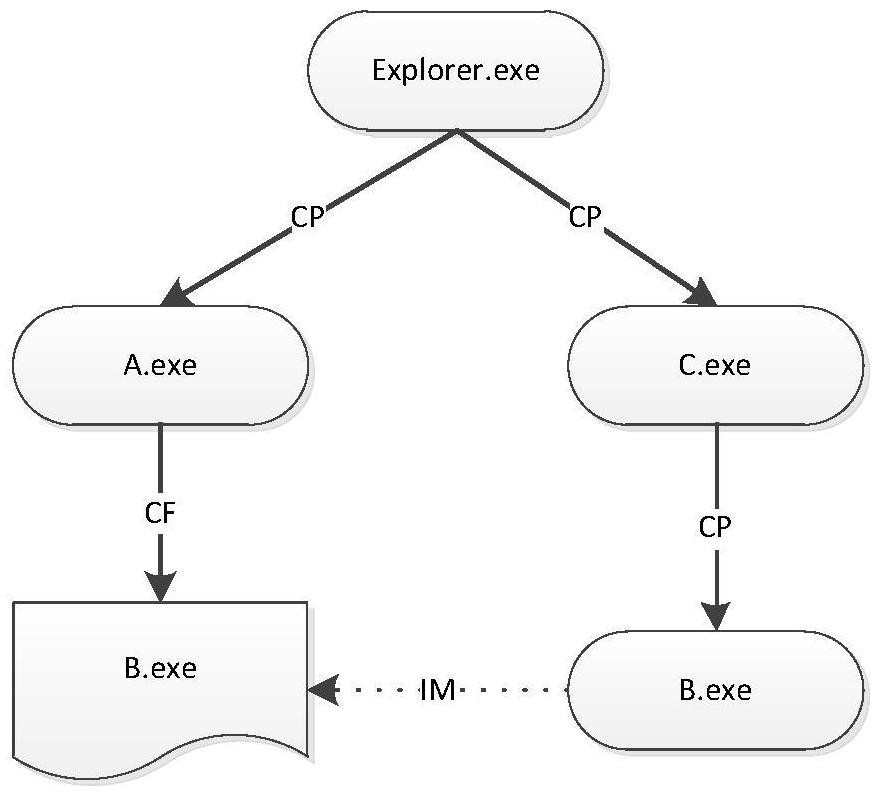
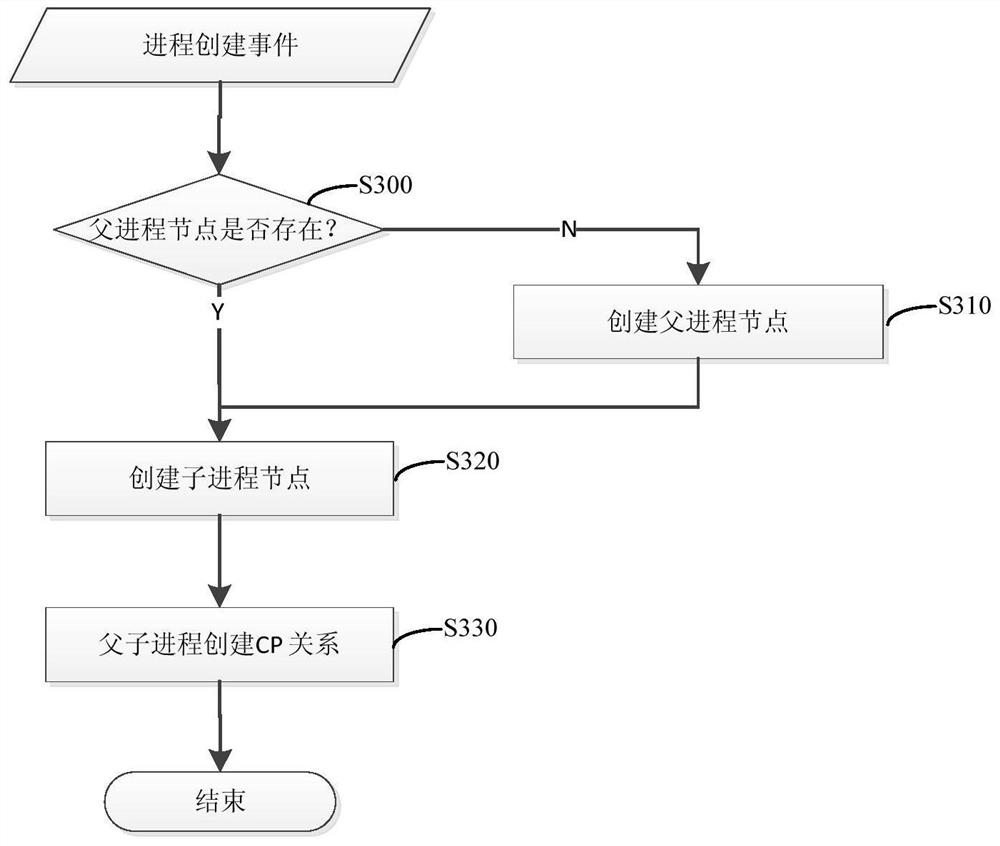
[0027]It should be mentioned before it discussed exemplary embodiments in more detail, some exemplary embodiments are described as a process or method depicted as a flowchart. While the flowchart describes the operations described in order, many of them can be implemented in parallel, concurrently or simultaneously. In addition, the order in which each operation can be rearranged. The processing can be terminated when its operation is completed, but may also have additional steps not included in the drawings. The process can correspond to methods, functions, procedures, subroutines, subroutines, and the like.
[0028]In the context, "Node", "Load Balancing Apparatus" is a computer device, which can perform a smart electronic device such as a predetermined processing and / or logic calculation by run a predetermined program or instruction, which can include processing. The device and the memory are executed by the processor to perform a pre-depoxing process in the memory, or execute a p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com