Steganographic Algorithm Unknown Information Hiding Detection Method
A detection method and information hiding technology, applied in computing, computer parts, instruments, etc., can solve the problems of reduced detection accuracy, ignorance of dense image embedding algorithms, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] Firstly, the feature extraction method and learning algorithm used in the process of the method of the present invention are introduced.
[0034] DCTR (Discrete Cosine Transform Residual): By decompressing the JPEG image into the airspace, using the characteristics of the statistical histogram, the 8000-dimensional DCTR feature is obtained.
[0035] GFR (Gabor Filter JPEG Rich Model): Decompress JPEG images by using 2D Gabor filters with different scales and directions, and extract 17,000-dimensional features from the filtered images.
[0036] FLD (Fisher Linear Discriminant): The basic idea is to project the two types of sample sets into one direction as much as possible, so that the classes are separated as much as possible. divergence as large as possible.
[0037] K-means: It is a typical distance-based clustering algorithm, which uses distance as a similar evaluation index, that is, the closer the distance between two features is, the greater the similarity is, an...
Embodiment 2
[0048] Embodiment 2: This embodiment is basically the same as Embodiment 1, and the special features are as follows:
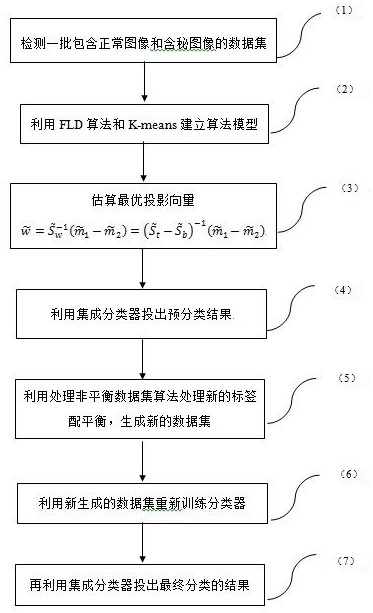
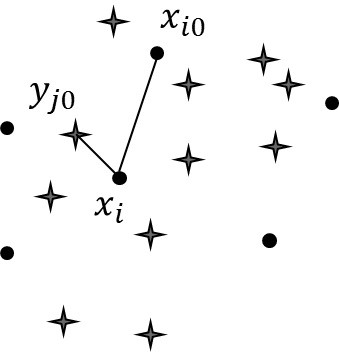
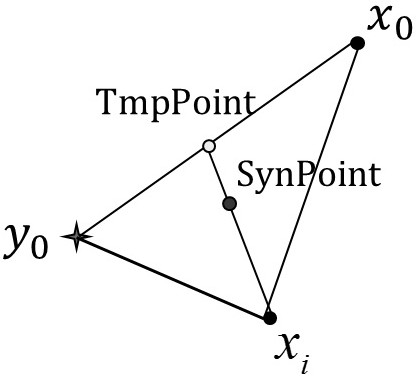
[0049] A batch of mixed images in the step 1) includes 800 normal images and 200 dense images as a test set. The steganographic algorithms used are J_UNIWORD and UERD. The steganographic algorithms used for the encrypted image are not known during the detection, and the image features are DCTR and GFR. see figure 2 is the distribution of the image dataset, Represents the features of normal images, ●Represents the features of secret images, normal images are used as majority class samples, and secret images are used as minority class samples, the closest to each minority class sample point is the majority class sample point, and this distribution will be used later Features add new data points for minority class samples.
[0050] Described step 2) utilizes FLD algorithm and K-means to establish algorithm model, obtains optimal projection vector
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com