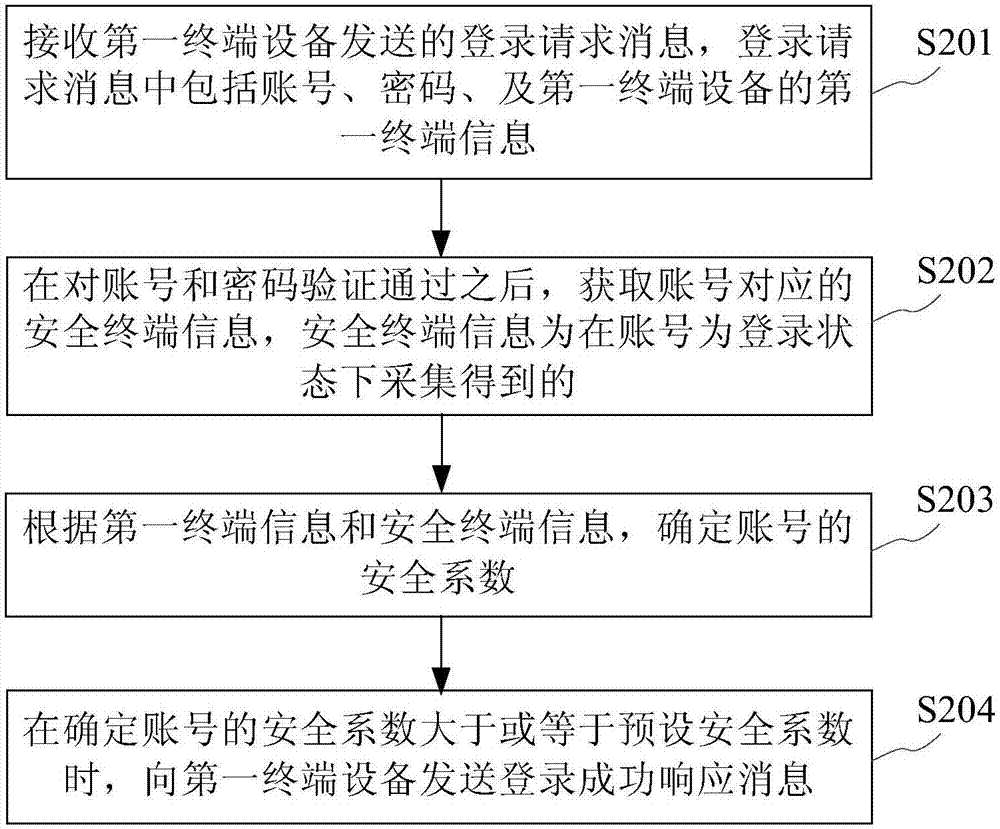
Account verification method and device
A verification method and account technology, which is applied in the field of communication, can solve problems such as poor account verification accuracy, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0112] Example 1, assuming that account 1 has logged in before the current moment, the security terminal information of account 1 is stored in the server, and the security terminal information is shown in Table 2:
[0113] Table 2
[0114]
[0115] When the server determines that the account 1 is in the login state, the server sends an information collection message to the terminal device corresponding to the account 1. Assuming that the account 1 is currently logged in through the terminal device 3 , the server sends an information collection message to the terminal device 3 .
[0116] The terminal device 3 sends the information of the terminal device 3 to the server as follows: terminal device 3, area 1, WiFi-1.
[0117] After receiving the above information, the server updates the security terminal information of account 1 according to the above information. Since the security terminal information shown in Table 2 does not include terminal device 3, it directly adds ter...
example 2
[0120] Example 2, assuming that the security terminal information corresponding to account 1 is as shown in Table 3, when the user requests to log in account 1 in terminal device 4, terminal device 4 sends a login request message to the server, the login request message includes account 1, password , and the information of the terminal device 4, wherein the information of the terminal device 4 is: the terminal device 4, area 1, and WIFI-1.
[0121] After the server receives the login request message from the terminal device 4, it first verifies whether the account 1 and the password match, and if they match, then verifies the information of the terminal device 4 according to the secure terminal information shown in Table 3. If the terminal device 4 is not included in the attribute information set, the safety factor of the terminal device 4 is 0. Since area 1 is included in the terminal location information set, the safety factor of area 1 is 0.9. Since the terminal network info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com