A method for implementing vpn tunnel protocol
A technology of tunneling protocol and implementation method, applied in the field of network communication, can solve the problem of not being able to proxy Internet data, etc., and achieve the effects of reducing data communication traffic, simple encapsulation format, and increasing encryption complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The embodiments of the present invention are described in detail below. This embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following implementation example.
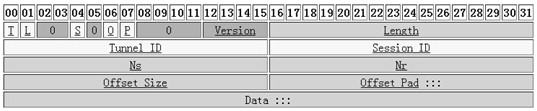
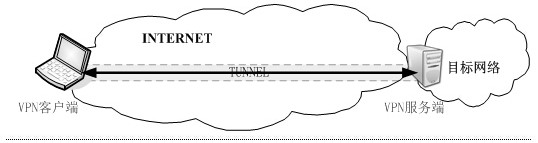
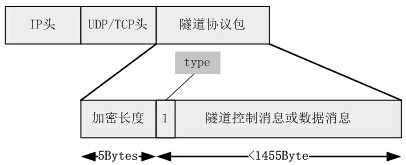
[0030] Such as figure 2 , image 3 , Figure 5 Shown: a VPN tunneling protocol implementation method, applied to the tunnel communication between the VPN client and the VPN server, the VPN client encrypts the user communication data in the tunnel, sends it to the VPN server, and the VPN server forwards and decrypts it After the user data is sent to the target network, the tunnel communication includes the following processes: (1) client: send a link establishment request; (2) when the negotiation times out or the client message error stops; when the client authentication is successful, the server sends the estab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com