Apparatus and method with enhanced security and reduced trust requirements for quantum key distribution
A quantum key distribution, quantum key technology, applied in the field of quantum key distribution, can solve the problem of not allowing QKD users to modify the parameters of the QKD system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The description of the invention is based on several drawings.
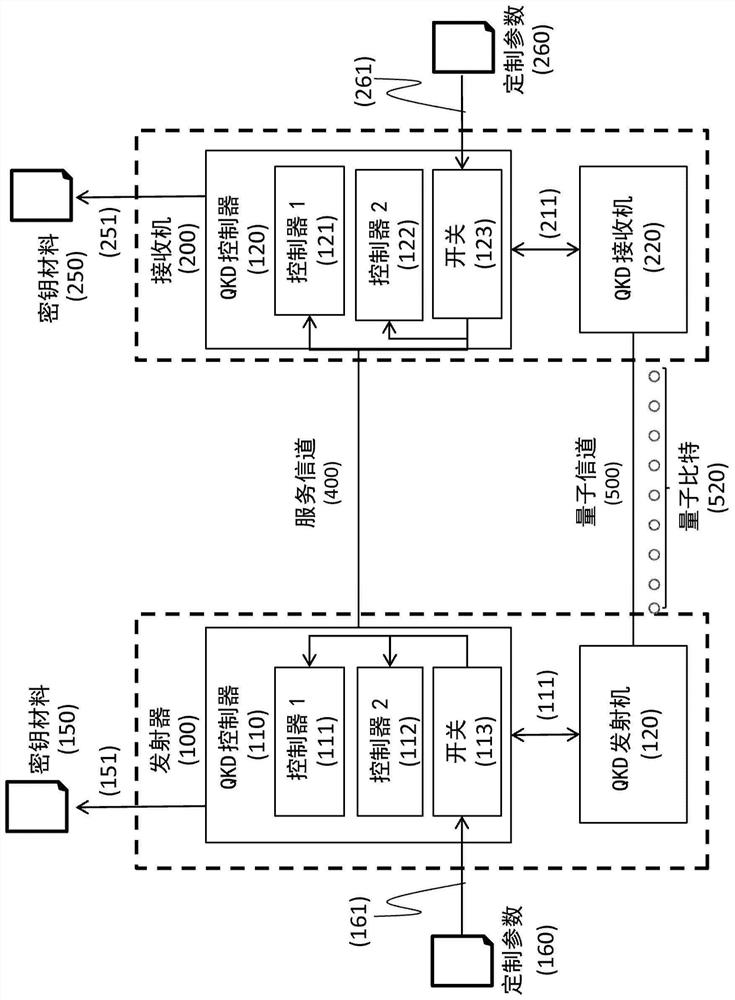
[0039] The main objective of the present invention is to enhance the security provided by the QKD system and reduce the trust requirements of the QKD users on the equipment manufacturers.
[0040] like figure 1 As shown in , the present invention can be used to securely exchange encryption keys between a transmitter (100) and a receiver (200). It is based on a conventional QKD system modified to accept additional custom parameters. The hardware of the QKD system consists of a QKD transmitter (120) and a QKD receiver (220) connected by a quantum channel (quantum channel (500)). The QKD transmitter (120) and receiver (220) generally consist of optical and electronic components suitable for generating and detecting a stream of qubits (520). The QKD transmitter (120) and receiver (220) are controlled by QKD controllers (110 and 210) via communication lines (115 and 215). These controllers consist, for exa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com