Encryption and decryption method, encryption and decryption apparatus and data transmitting system
An encryption method and encryption device technology, applied in the field of communication, can solve problems affecting OTN system performance, decrypted data errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
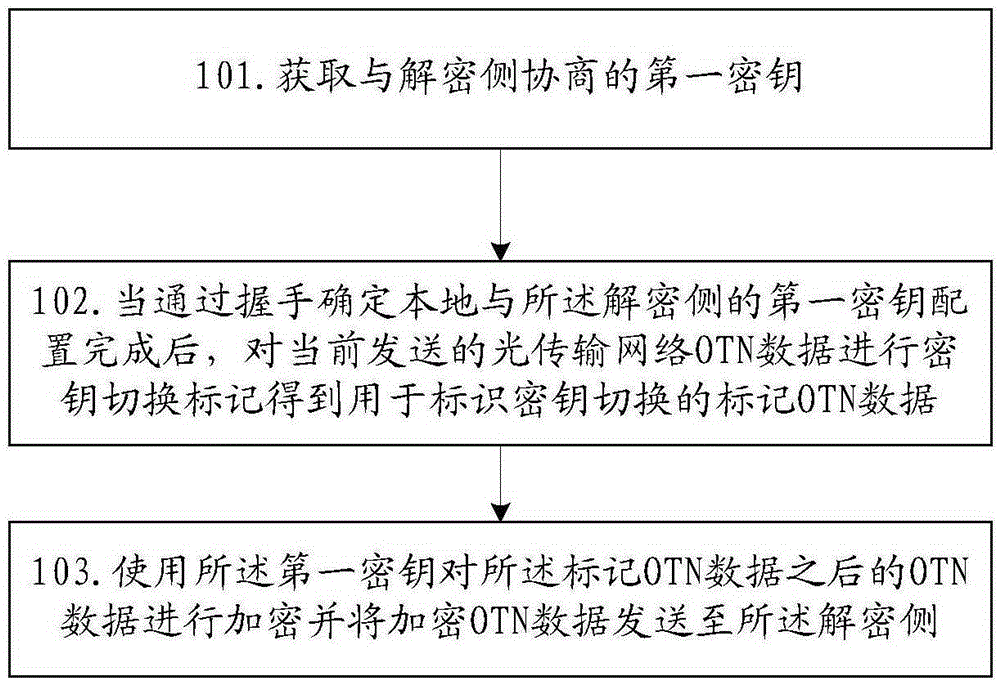
[0082] Embodiment 1 of the present invention provides an encryption method, which is applied to the encryption side, such as figure 1 As shown, the encryption method includes:
[0083] S101: Obtain the first key negotiated with the decryption side;
[0084] When the key for encrypting and decrypting transmitted OTN data in the OTN network needs to be updated, for example, when the key update period is reached, the encryption side and the decryption side perform key negotiation, so that the encryption side and the decryption side configure the same A key. After the key negotiation process between the encryption side and the decryption side is completed, the negotiated first key is obtained. Here, the negotiated key is an encryption and decryption algorithm such as AES, and the present invention does not limit the specific encryption and decryption algorithm. Moreover, the key negotiation process is an existing technology, and will not be repeated here.
[0085] In order to f...
Embodiment 2
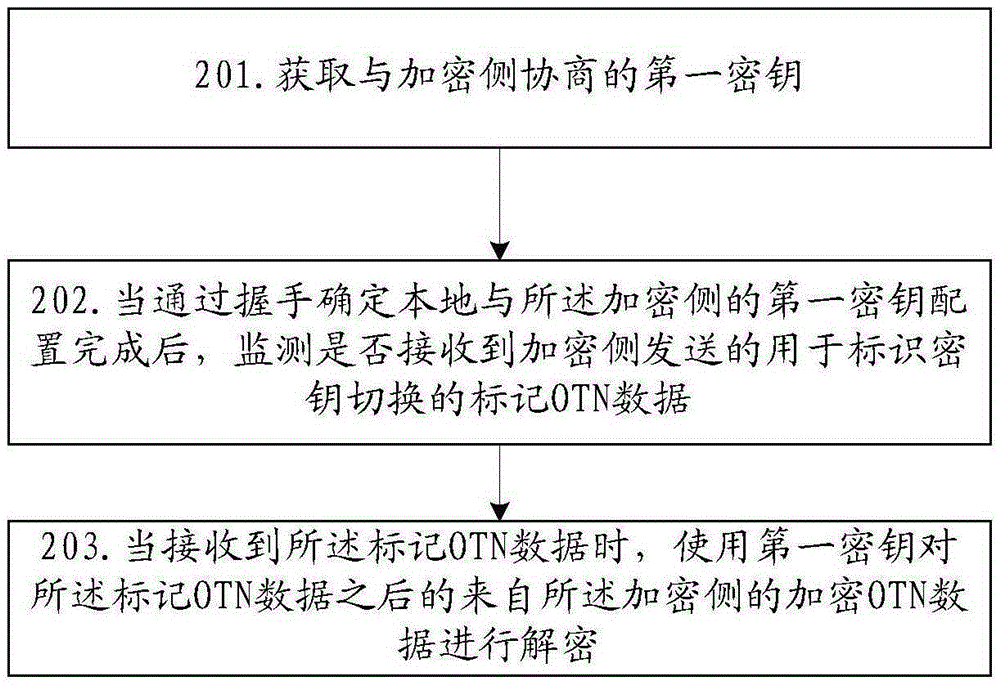
[0105] Embodiment 2 of the present invention provides a decryption algorithm corresponding to the encryption algorithm in Embodiment 1, such as figure 2 As shown, the decryption method includes:
[0106] S201: Obtain the first key negotiated with the decryption side;
[0107] Here, when the key for encrypting and decrypting transmitted OTN data in the OTN network needs to be updated, for example, when the update period of the key is reached, the decryption side and the encryption side conduct key negotiation to obtain a new key, namely the first secret key. key, and obtain a new first key, in case the original second key key2 is switched to the first key key1, and the new key is used for decryption. Wherein, when key1 is configured on the decryption side, the same key1 is configured on the encryption side at the same time, so as to ensure that the encryption and decryption keys on the encryption side and the decryption side are consistent, and the decryption side can correct...
Embodiment 3
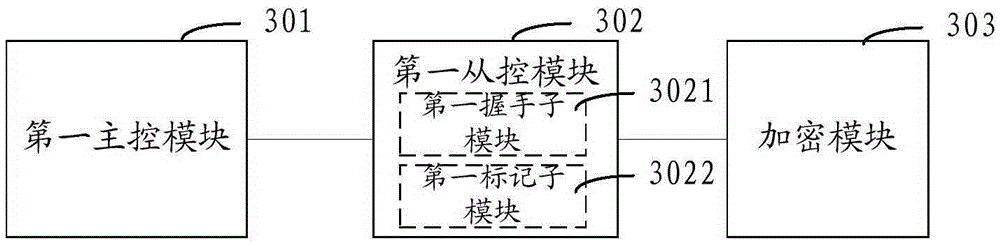
[0119] In order to implement the encryption method provided by the first embodiment above, the embodiment of the present invention provides an encryption device, such as image 3 As shown, the encryption device includes: a first master control module 301, a first slave control module 302, and an encryption module 303; wherein,
[0120] The first main control module 301 is configured to obtain the first key negotiated with the decryption side;
[0121] The first slave control module 302 is configured to perform a key switch mark on the currently sent optical transport network OTN data to obtain a key switch identification key after the handshake determines that the configuration of the first key on the local side and the decryption side is completed. Mark OTN data;
[0122] like image 3 As shown, the first slave control module 302 includes a first handshake sub-module 3021,
[0123] The first handshake submodule 3021 is configured to: receive the key update message sent by ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com