Security verification method, device, terminal device and server
A technology for terminal equipment and security verification, applied in transmission systems, electrical components, etc., can solve problems such as weak security, and achieve the effect of security verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
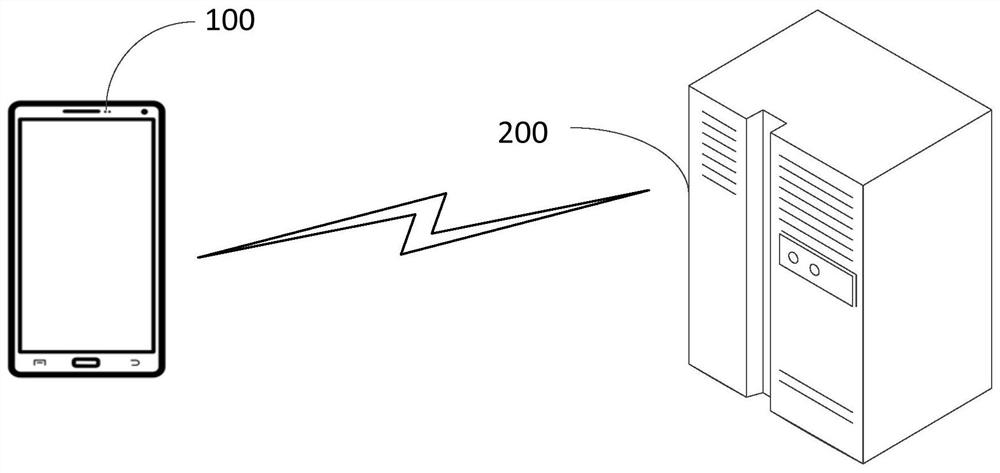
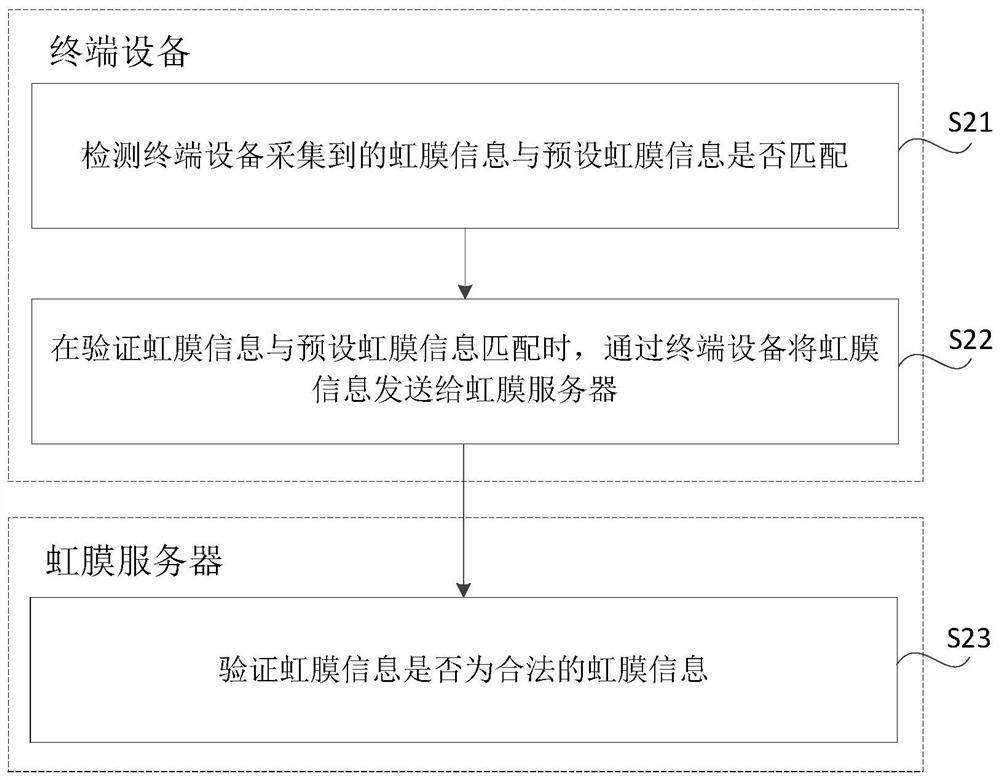
[0074] The security verification method is applied to the access control system of XX company, and the terminal device is the mobile phone of user A. When user A passes the security verification of the access control system, for example, the following process can be followed.
[0075] 1. User A can use the mobile phone to swipe NFC outside the door of the access control system to obtain the destination network address (that is, the address of the iris server, which can be an encrypted address).
[0076] 2. User A scans the iris through the mobile phone. For example, it can scan through the application program pre-installed in the mobile phone. Set iris information for comparison.
[0077] 3. When the mobile phone compares the iris information of user A with the preset iris information, it sends the collected iris information of user A to the iris server corresponding to the destination network address, and a confirmation message with a time stamp encryption duration of, for ex...
Embodiment 2
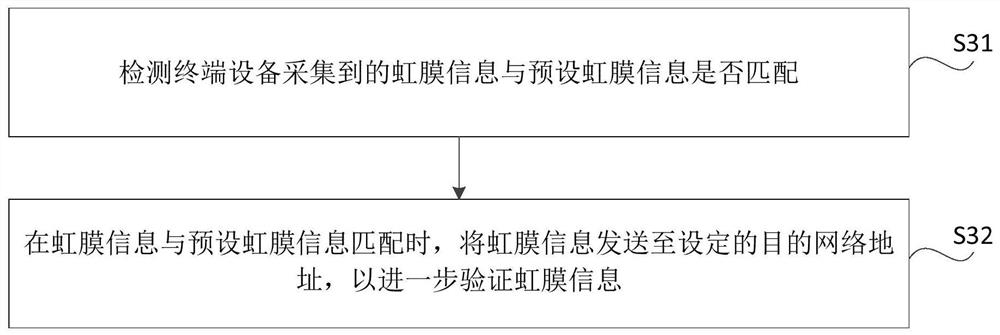
[0080] The security verification method is applied to the access control system of XX company. The terminal device is the mobile phone of user A, and the address of the iris server can be pre-stored in the mobile phone, that is, the address of the destination network. When user A passes the security verification of the access control system, for example, the following process may be performed.
[0081] 1. User A scans the iris through the mobile phone, for example, through an application program installed in the mobile phone.
[0082] 2. During the iris scanning process, the mobile phone performs liveness detection on user A, and compares the collected iris information of user A with the preset iris information stored in the mobile phone. When comparing and matching, set the mobile phone to open the door The NFC information of the virtual door card is available, and the collected iris information of user A is sent to the destination network address; when the comparison does no...
Embodiment 3
[0086] The security verification method is applied to electronic payment, and the terminal device is the mobile phone of user A.
[0087] 1. User A swipes the NFC of his mobile phone when he wants to pay, and obtains the transaction information (including transaction number, transaction amount, etc.) provided by the merchant.
[0088] 2. User A scans the iris through the mobile phone, for example, through a special application program (the application program used for payment can enter the user's iris information and bind it with the payment card when it is used for the first time), and the mobile phone scans the iris during the iris scanning process. Liveness detection is performed on user A, and the collected iris information of user A is compared with the preset iris information stored in the mobile phone (the comparison can be performed in trustzone to improve security). When comparing and matching, the mobile phone sends information such as iris information, payment card ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com