A traffic processing method, device and system
A processing method and equipment technology, applied in the field of communication, can solve the problems that affect the normal business of users, cannot solve the problems of high cost and low efficiency, and achieve the effect of improving experience and reducing use cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
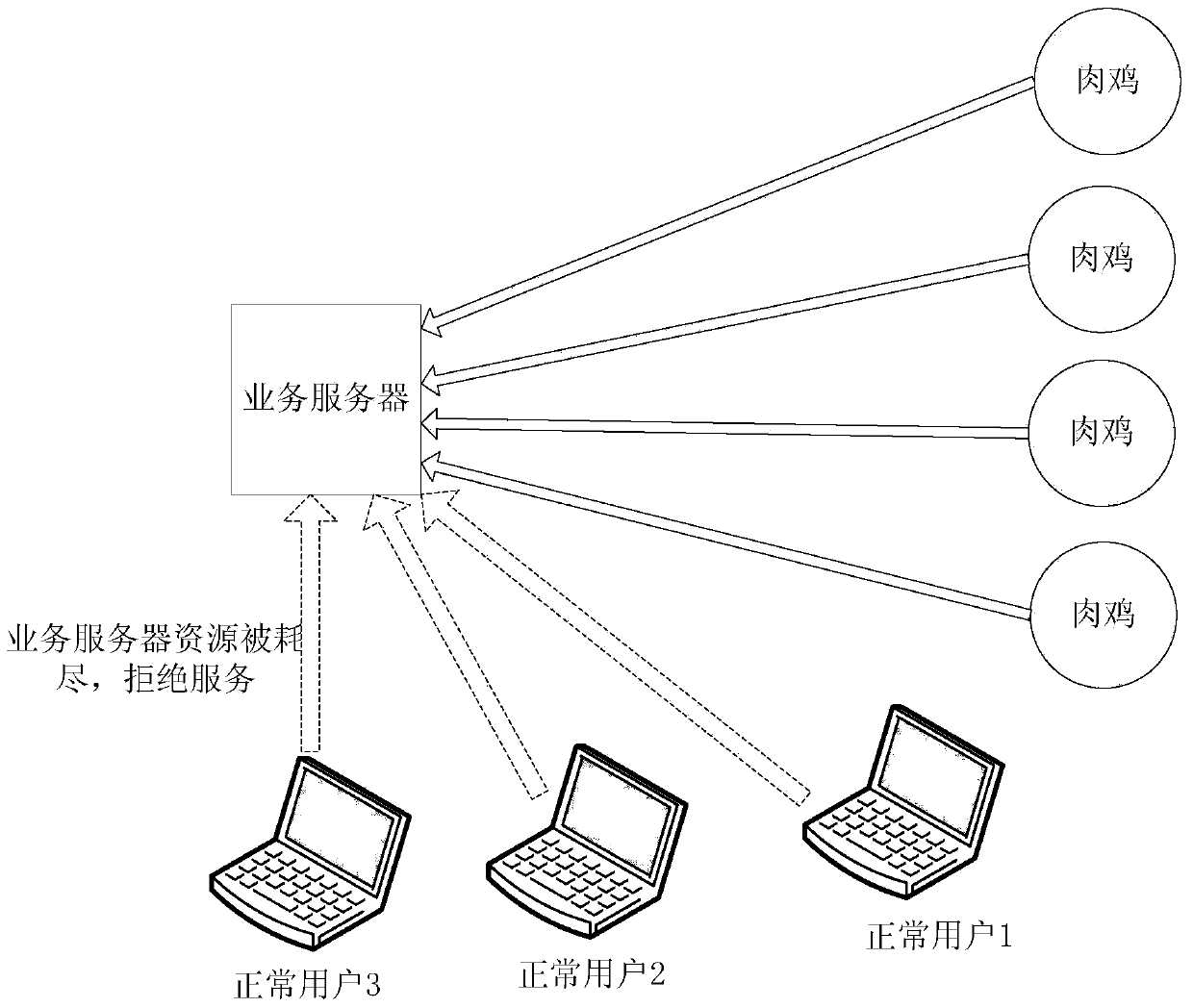
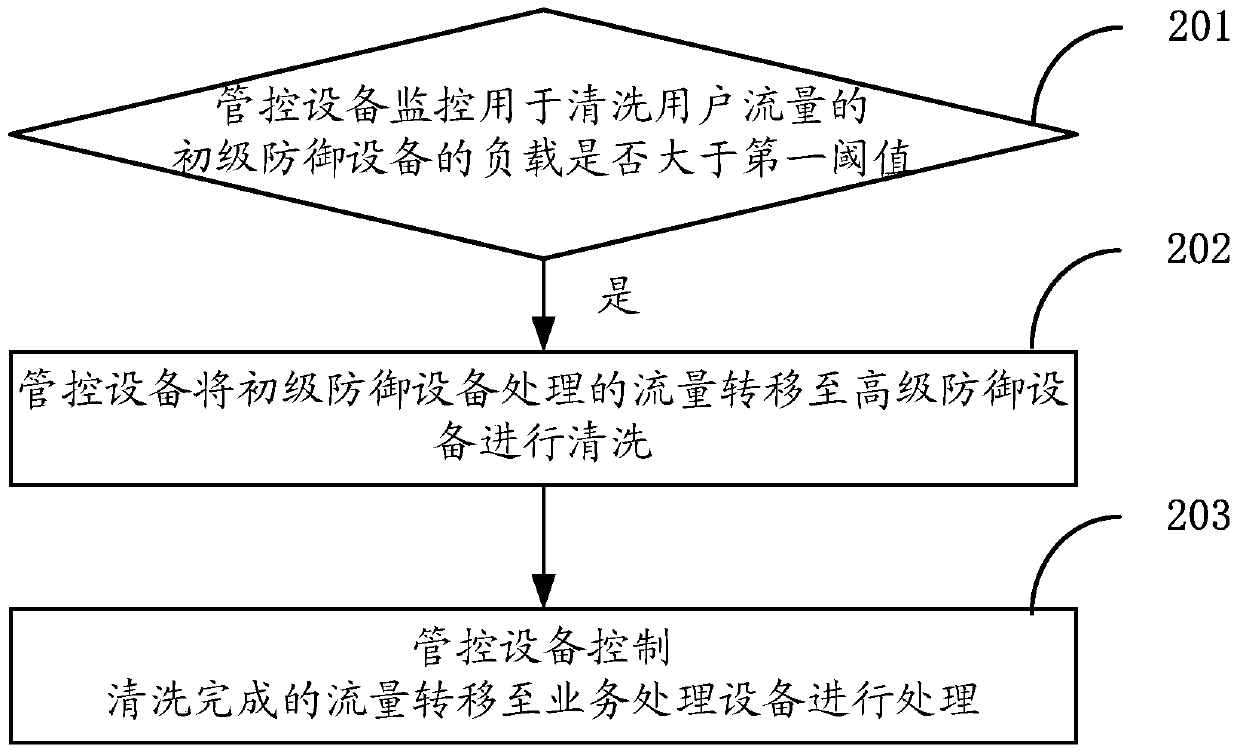
[0057] As mentioned in the background technology, the defense methods in the prior art cannot achieve a good defense effect, the cost of use is too high, the effect is not good, and the user experience is not high, so a traffic processing method is proposed in the embodiment of this application , applied to a system including primary defense equipment and advanced defense equipment, where the traffic cleaning capability of the advanced defense equipment is higher than that of the primary defense equipment, such as figure 2 As shown, the method includes:
[0058] In step 201, the management and control device monitors whether the load of the primary defense device for cleaning user traffic is greater than a first threshold.
[0059] Specifically, when detecting that there is illegal traffic, first start the primary defense device to clean the illegal traffic, wherein the primary defense device can be an IDC (Internet Data Center, Internet Data Center) device, because it is not...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com