An information processing method and electronic device
An information processing method and technology of electronic equipment, applied in the electronic field, can solve problems such as inability to effectively prevent illegal operations, and achieve the effect of improving user resource security and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
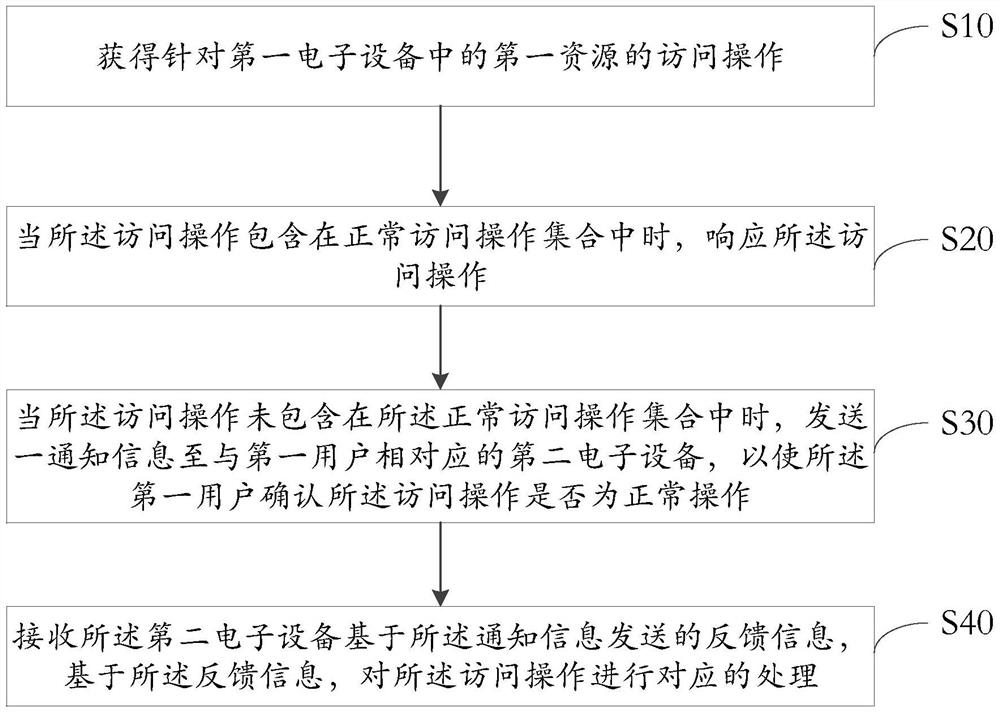
[0054] Please refer to figure 1 , the embodiment of the present application provides an information processing method, including:
[0055] S10: Obtain an access operation for the first resource in the first electronic device;
[0056] S20: When the access operation is included in the set of normal access operations, respond to the access operation;
[0057] S30: When the access operation is not included in the set of normal access operations, send a notification message to the second electronic device corresponding to the first user, so that the first user can confirm whether the access operation is Normal operation, wherein the first user is the user to which the first resource belongs;
[0058] S40: Receive feedback information sent by the second electronic device based on the notification information, and perform corresponding processing on the access operation based on the feedback information.
[0059] In a specific implementation process, the first electronic device m...
Embodiment 2
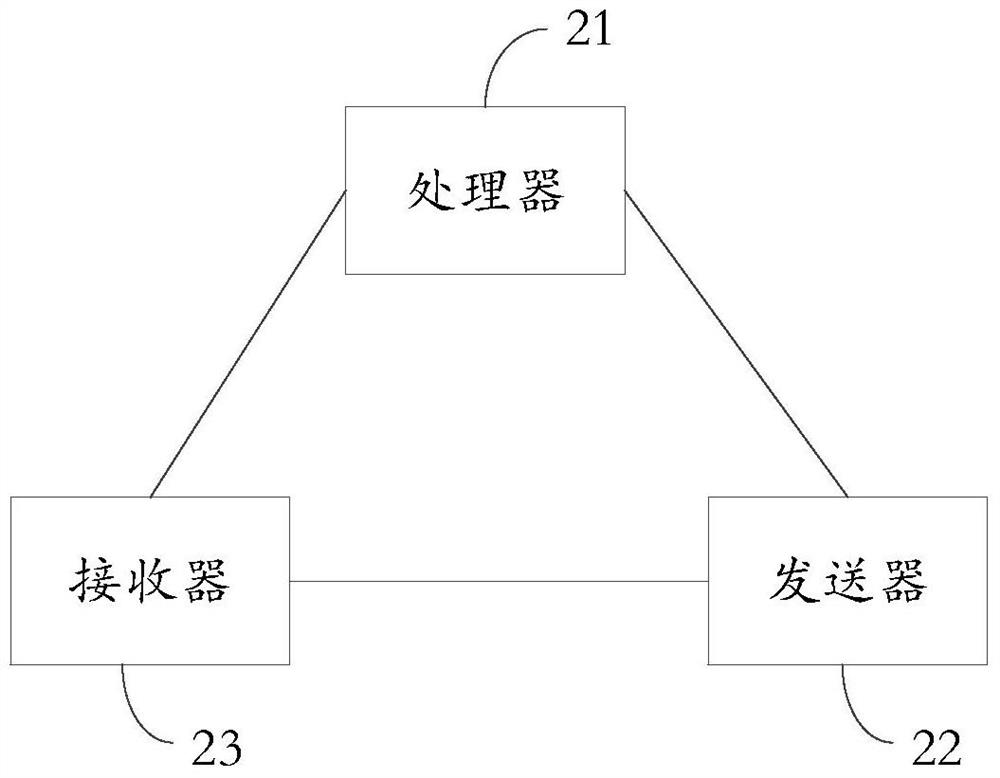
[0087] Based on the same inventive concept as Embodiment 1 of this application, please refer to figure 2 , Embodiment 2 of the present application provides an electronic device, including:
[0088] Processor 21, configured to obtain an access operation for the first resource in the electronic device, and to respond to the access operation when the access operation is included in a set of normal access operations, and to respond to the access operation when the access operation When not included in the set of normal access operations, generate a notification message;
[0089] A transmitter 22, connected to the processor 21, configured to send the notification information to the first electronic device corresponding to the first user, so that the first user can confirm whether the access operation is a normal operation, wherein , the first user is the user to which the first resource belongs;
[0090] A receiver 23, connected to the processor 21, configured to receive the fee...
Embodiment 3
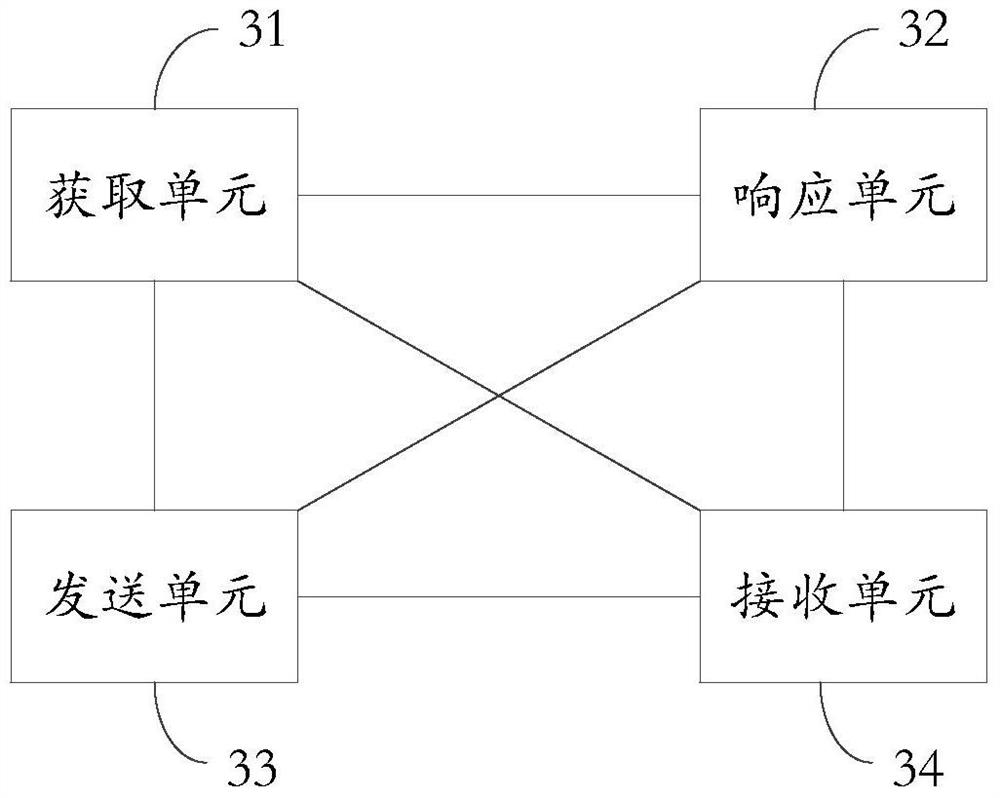
[0106] Based on the same inventive concept as the first embodiment of the present application, the third embodiment of the present application provides an electronic device, please refer to image 3 ,include:
[0107] An obtaining unit 31, configured to obtain an access operation for the first resource in the electronic device;
[0108] A response unit 32, configured to respond to the access operation when the access operation is included in the set of normal access operations;
[0109] A sending unit 33, configured to send a notification message to a first electronic device corresponding to the first user when the access operation is not included in the set of normal access operations, so that the first user confirms the Whether the access operation is a normal operation, wherein the first user is the user who belongs to the first resource;
[0110] The receiving unit 34 is configured to receive feedback information sent by the first electronic device based on the notificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com