Unauthorized resource transmission method and device
A transmission method and an unauthorized technology, applied in the transmission field of unauthorized resources, can solve the problems of many wireless access sites, difficult cooperation, and many wireless access technologies.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
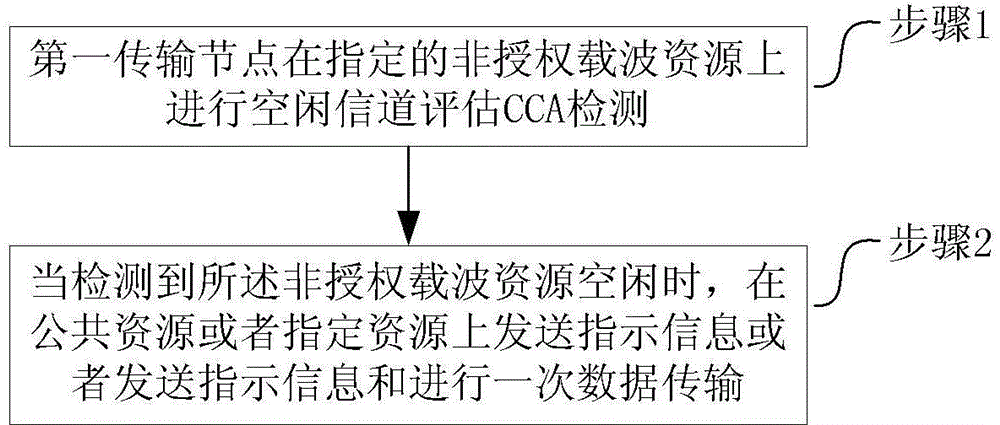
[0103] This embodiment describes the processing performed by the first transmission node in a method for transmitting unauthorized resources, such as figure 1 shown, including:
[0104] Step 1, the first transmission node performs idle channel assessment CCA detection on the designated unlicensed carrier resource;
[0105] The first transmission node includes a first terminal.
[0106] Step 2, when it is detected that the unlicensed carrier resources are idle, send indication information on public resources or designated resources or send indication information and perform a data transmission, the indication information is used to notify that the unlicensed carrier resources are occupied .
[0107] The common resource is located on an unlicensed carrier resource, the maximum range is two subframes, and the minimum range is a complete OFDM symbol.
[0108] Specifically, the common resources include the following resources in the time domain: the first complete OFDM symbol af...
Embodiment 2
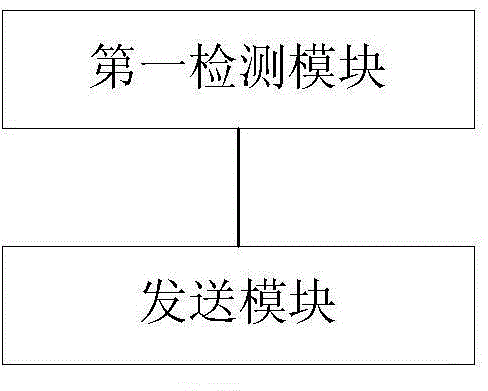
[0124] The device for implementing the above method is located at the first transmission node, such as figure 2 As shown, including a first detection module and a sending module, wherein:
[0125] The first detection module is configured to perform idle channel assessment CCA detection on designated unlicensed carrier resources;
[0126] The sending module is configured to, when the first detection module detects that the unlicensed carrier resource is idle, send indication information on public resources or designated resources or send indication information and perform a data transmission, and the indication information is used To notify that the unlicensed carrier resources are occupied.
[0127] It should be noted that since the device provided in this embodiment can implement the method of the first embodiment above, other detailed operations can refer to the corresponding content of the first embodiment, which will not be repeated here.
Embodiment 3
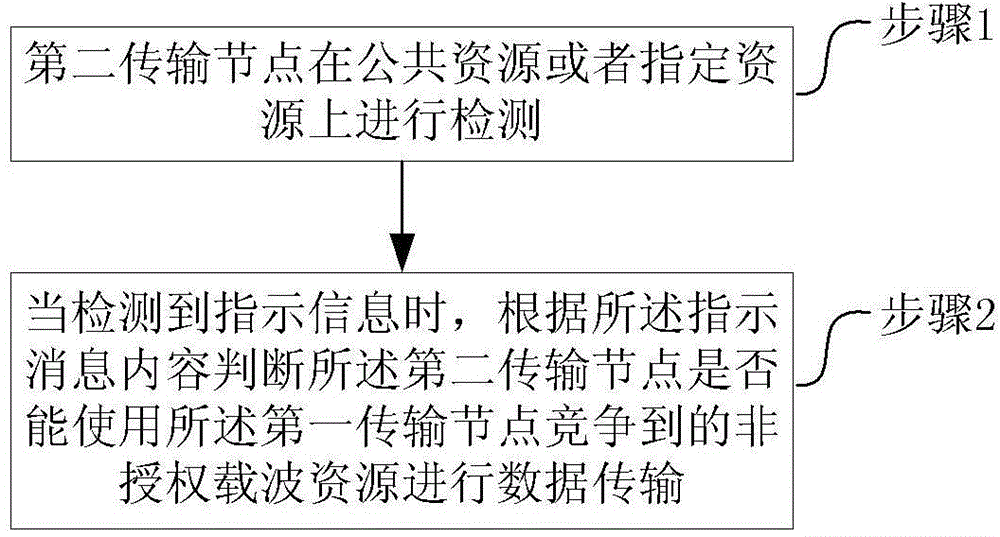
[0129] This embodiment describes the processing performed by the second transmission node in a method for transmitting unauthorized resources, such as image 3 As shown, the method includes:
[0130] Step 1, the second transmission node performs detection on public resources or designated resources;
[0131] For the locations of the public resources and designated resources, refer to the description in Embodiment 1.
[0132] Step 2: When the indication information is detected, judge whether the second transmission node can use the unlicensed carrier resource that the first transmission node competes for to perform data transmission according to the content of the indication message.
[0133] In this example, the first transmission node includes the first terminal; the second transmission node includes one or more of the following nodes: the first base station to which the first terminal belongs, the adjacent base station of the first base station, Other terminals that have p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com