Malicious account identification method and device
An identification method and account technology, applied in the Internet field, can solve problems such as low efficiency, achieve the effect of improving identification efficiency and reducing the amount of identification data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
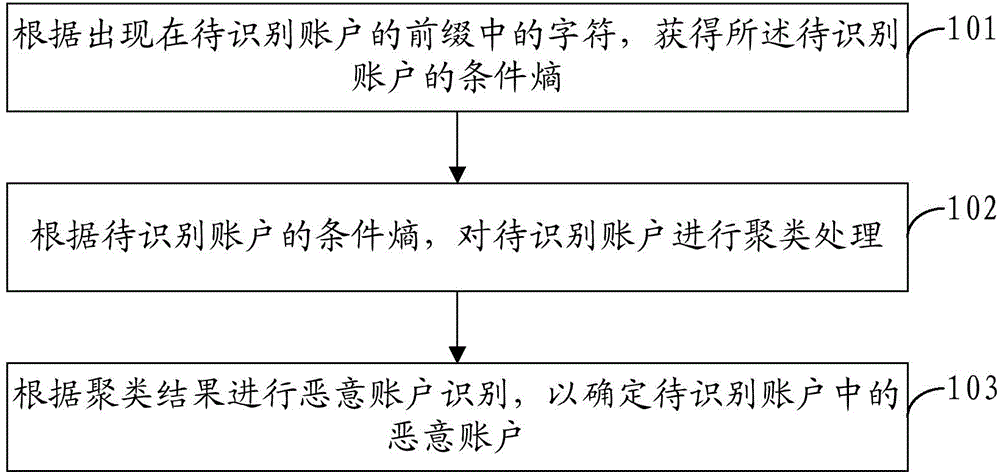
[0031] In an optional implementation manner, an implementation manner of obtaining the conditional entropy of the account to be identified according to the characters in the prefix appearing in the account to be identified includes:
[0032] Determine the regular characters that appear in the prefix of the account to be identified;
[0033] Count the generation probability of each regular character in the prefix of the account to be identified, and count the transition probability of each regular character to other regular characters;
[0034] According to the generation probability of each regular character in the prefix of the account to be identified and the transition probability of each regular character to other regular characters, the conditional entropy of the account to be identified is obtained.
[0035] At present, the characters used in the prefix of most accounts include "a"~"z", "0"~"9" and "." (dot), "-" (hyphen), "_" (underscore) and other characters , Occasio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com