Method and device for processing surveillance
A processing method and monitoring and receiving technology, applied in the field of communication, can solve the problems of low monitoring efficiency and complicated operation of monitoring tasks, and achieve the effect of improving monitoring efficiency and reducing complexity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
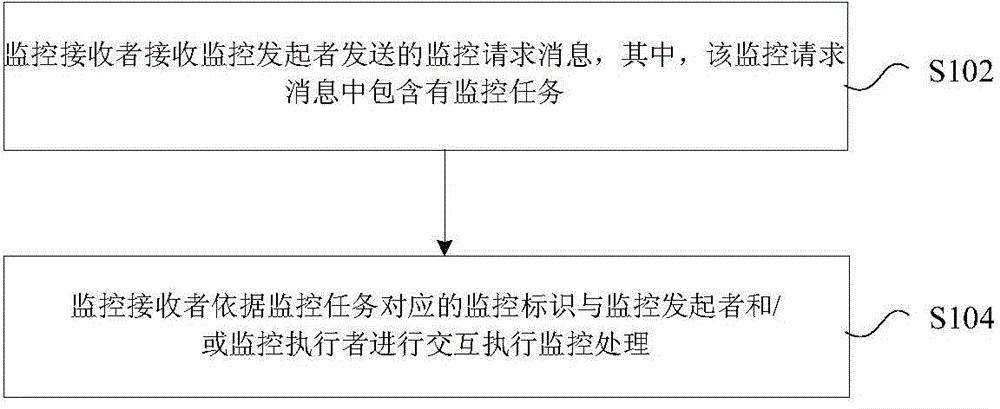
[0133] 1. The CSE sends a monitoring request message to the SCEF / IWF. The request message includes a monitoring task, and the parameter combination included in the monitoring task includes at least one of the following: 1) The identifier of the terminal to be monitored, the event to be monitored; 2) The monitored Terminal ID, events to be monitored, and the number of monitoring reports; 3) IDs of monitored terminals, events to be monitored, and duration of monitoring; 4) IDs of monitored terminals, events to be monitored, monitoring start time, Monitoring end time; 5) The identifier of the monitored terminal, the event to be monitored, the monitoring start time, and the duration of monitoring; 6) The identifier of the monitored terminal, the event to be monitored, and the operation to be performed after the event occurs.
[0134] It should be noted that here, the event parameters to be monitored may be implemented in multiple manners.
[0135] First: directly give the definiti...
Embodiment 2
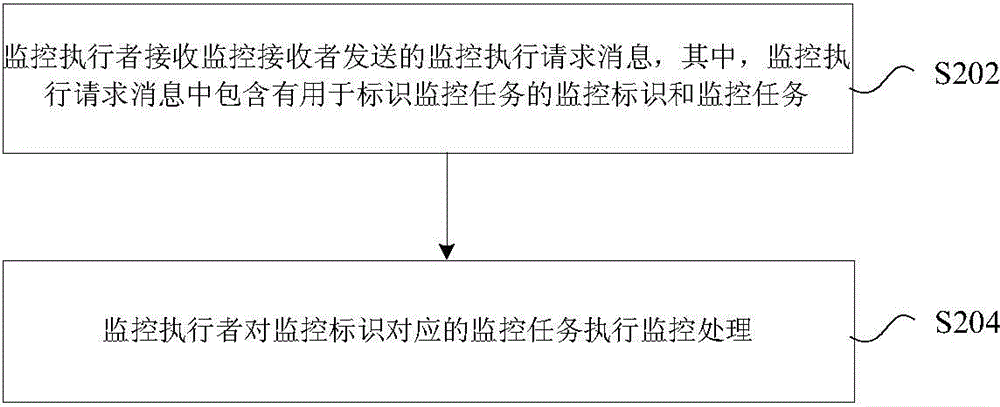
[0186] 1. The CSE sends a monitoring request message to the SCEF / IWF. The request message includes a monitoring task, and the monitoring task includes at least one of the following parameter combinations:
[0187] 1) Monitoring ID, the ID of the monitored terminal, and the event to be monitored; 2) Monitoring ID, the ID of the monitored terminal, the event to be monitored, and the number of monitoring reports; 3) Monitoring ID, the ID of the monitored terminal , the event to be monitored, and the monitoring duration; 4) Monitoring ID, the ID of the monitored terminal, the event to be monitored, the monitoring start time, and the monitoring end time; 5) Monitoring ID, the ID of the monitored terminal, and the monitoring ID Event, monitoring start time, monitoring duration; 6) Monitoring ID, ID of the monitored terminal, the event to be monitored, and the operation to be performed after the event occurs.
[0188] Here, the monitoring identifier is used to identify a monitoring t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com