Big data security protection cloud system based on trusted computing
A security protection and trusted computing technology, applied in the field of big data, can solve problems such as side channel attacks, achieve the effect of small calculation, increase calculation speed, and save time and cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention is further described in conjunction with the following examples.
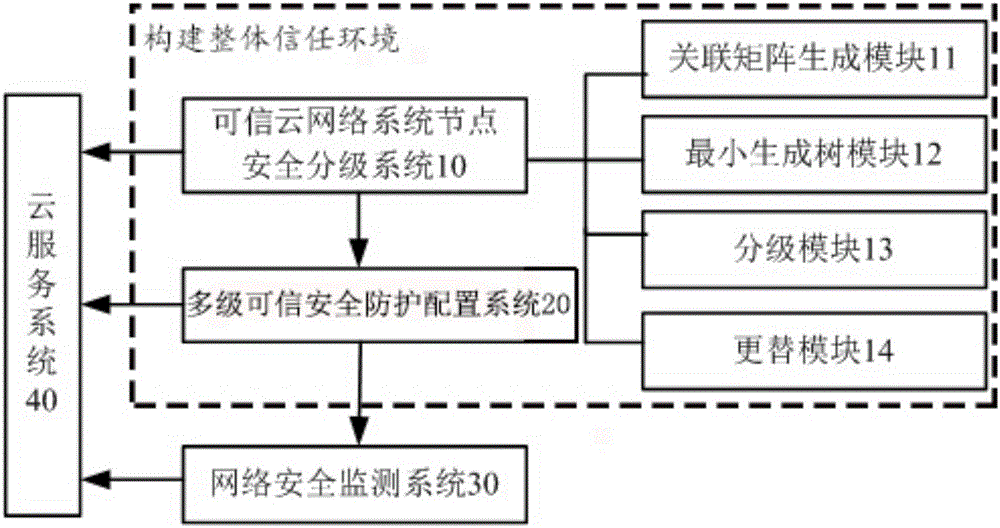
[0040] Such as figure 1 The shown big data security protection cloud system based on trusted computing includes a trusted cloud network node security classification system 10, a multi-level trusted security protection configuration system 20, a network security monitoring system 30, and a cloud service system 40. The trust cloud network node security grading system 10 divides the network nodes into 4 different security levels by calculating the importance value of the network nodes, and the multi-level trusted security protection configuration system 20 is based on the trusted cloud network node security grading system 10. Classification results provide different security encryption services for network nodes of different security levels and links between nodes; the network security monitoring system 30 is used to monitor the status of network nodes, and the cloud service system 40 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com